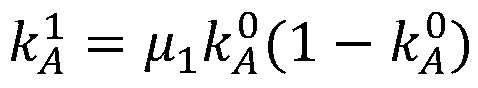Patents
Literature
58results about How to "Reduce the possibility of tampering" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
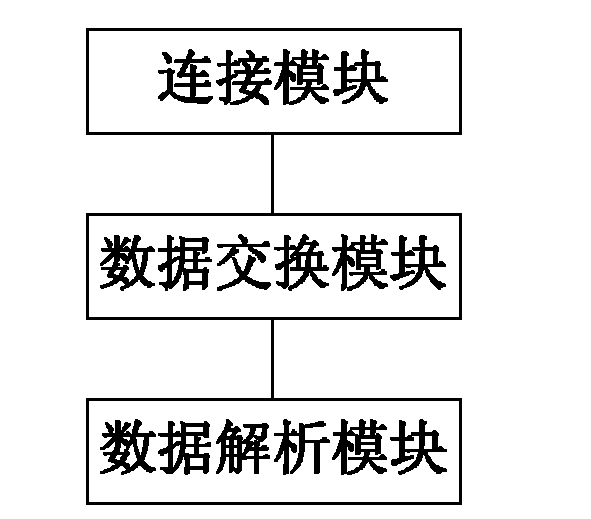
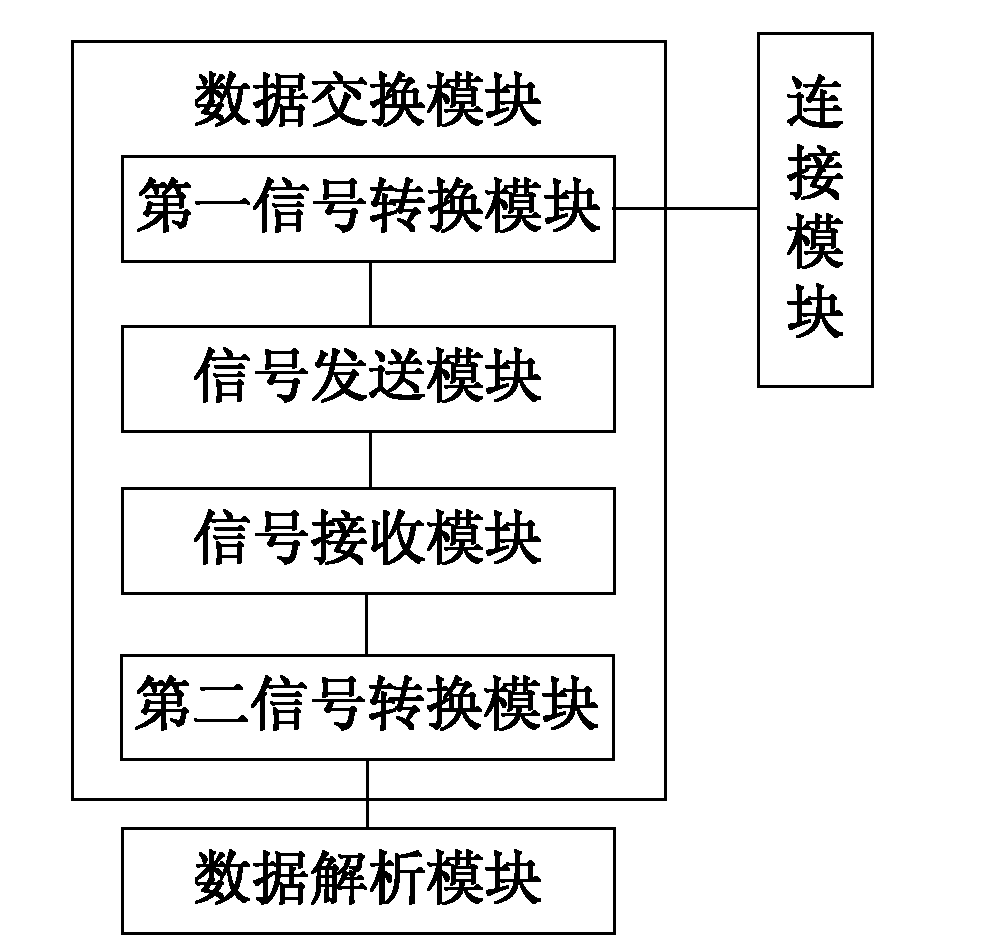
Method, system and terminal equipment for mobile payment
InactiveCN102360479AReduce the possibility of tamperingLow transplantPayment architectureEmbedded systemLoudspeaker
The invention discloses a method, a system and terminal equipment for mobile payment. According to the method, the system and the terminal equipment, the transaction is safe by controlling the payer distance and sound wave frequency, the possibility that transaction data is intercepted, stolen and tampered is reduced, the transaction efficiency is high, and the transaction data is transmitted in a form of sound waves. Especially, the sound waves are transmitted by using loudspeakers and microphones on terminal equipment, hardware equipment is not required to be modified or increased, the expansibility is high, transplantation is easy to perform, low end mobile phones are compatible, the cost is low, the transaction is safe by controlling the distance and the frequency, the possibility that the transaction data is intercepted, stolen and tampered is reduced, the transaction efficiency is high.
Owner:SHENZHEN TEMOBI SCI &TECH
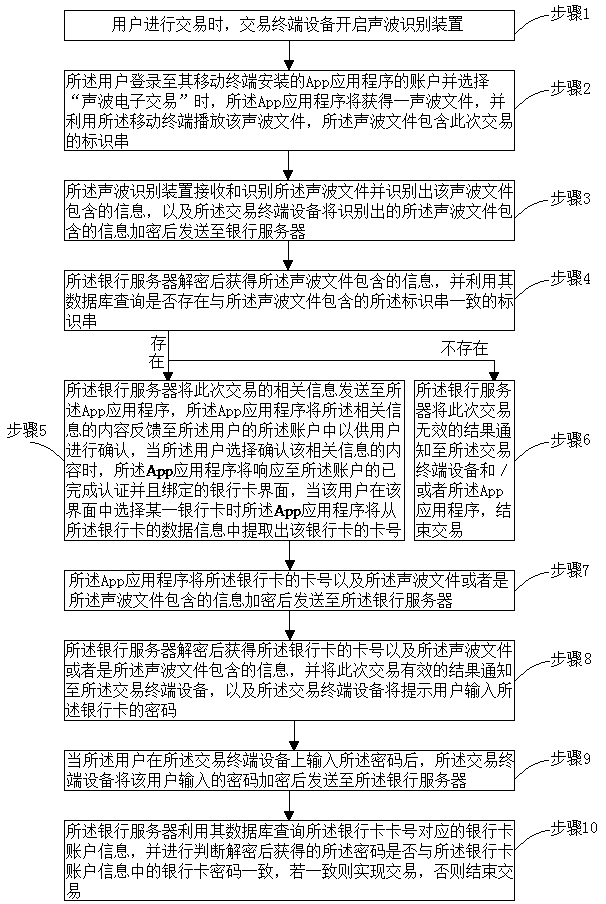
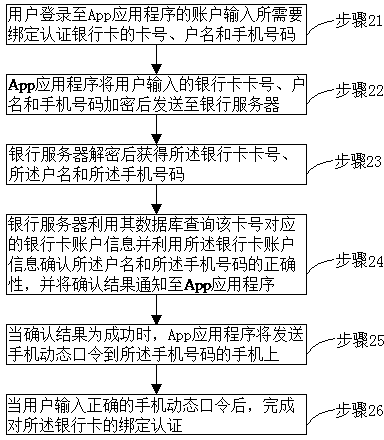
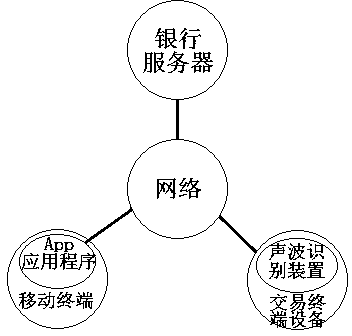
Method and system for realizing electronic transaction through sound waves
InactiveCN103942691AReduce the possibility of tamperingImprove securityCash registersProtocol authorisationUser inputPassword
The invention provides a method and system for realizing an electronic transaction through sound waves. The method comprises the steps that a user uses a mobile terminal of the user to log in an App account to select a sound-wave electronic transaction item, the user obtains a sound wave file, and the sound wave file is played; after a sound wave recognition device receives and recognizes information contained in the sound wave file, a transaction terminal device encrypts the information contained in the sound wave file and sends the encrypted information to a bank server; the bank server decrypts the encrypted information, then carries out transaction confirm according to the information contained in the sound wave file, and sends related information of the transaction to the App when the transaction is confirmed to be successful; when the user selects the confirm item, and selects some bank card on an interface, responded by the App, of bank cards which are in the account of the user, are successfully authenticated and bound, the App sends information of the bank card and the sound wave file or the information contained in the sound wave file to the bank server after carrying out encryption, and the transaction is completed after the bank server carries out decryption, and the user inputs a correct bank card password on the transaction terminal device.
Owner:王恩惠
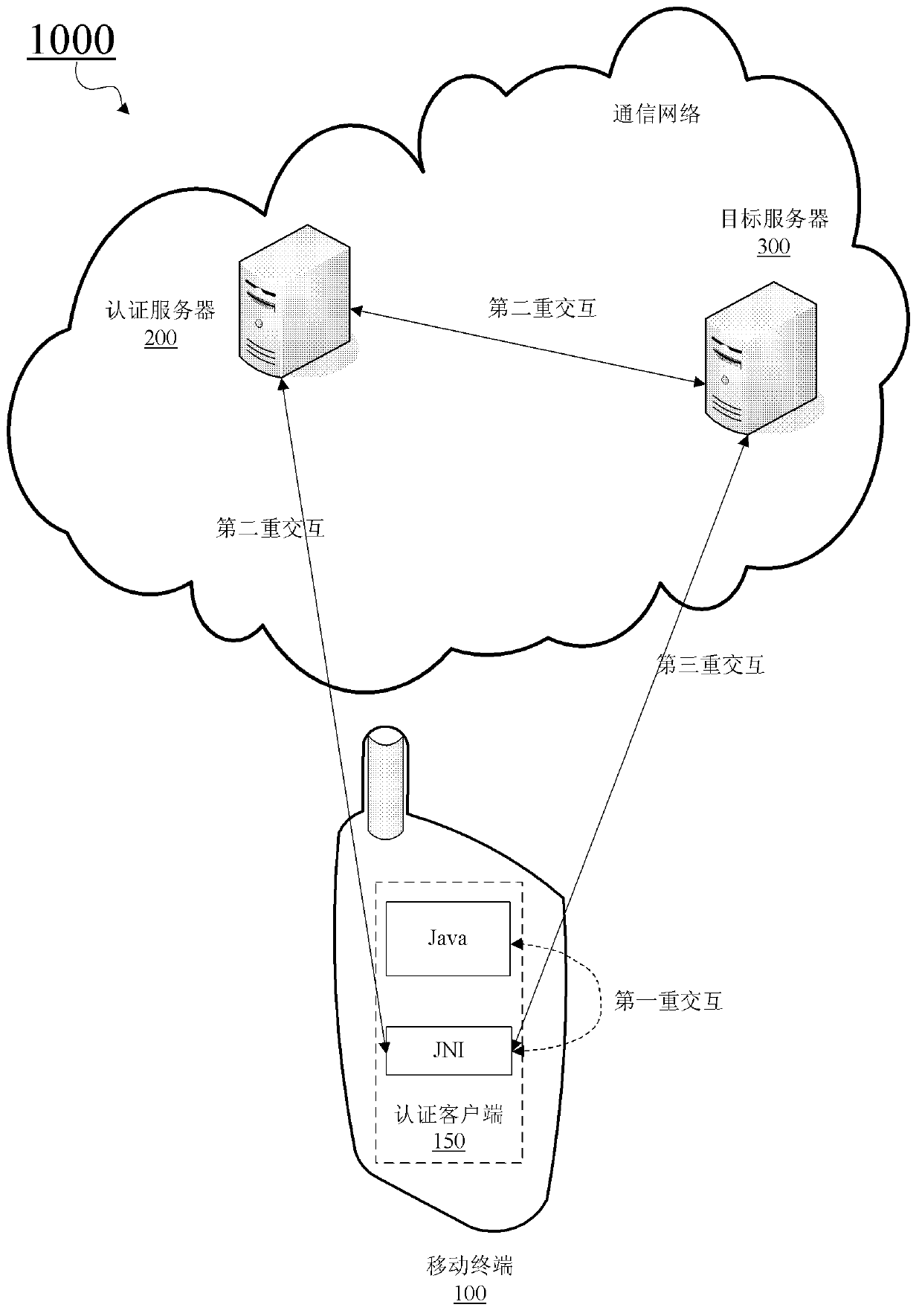
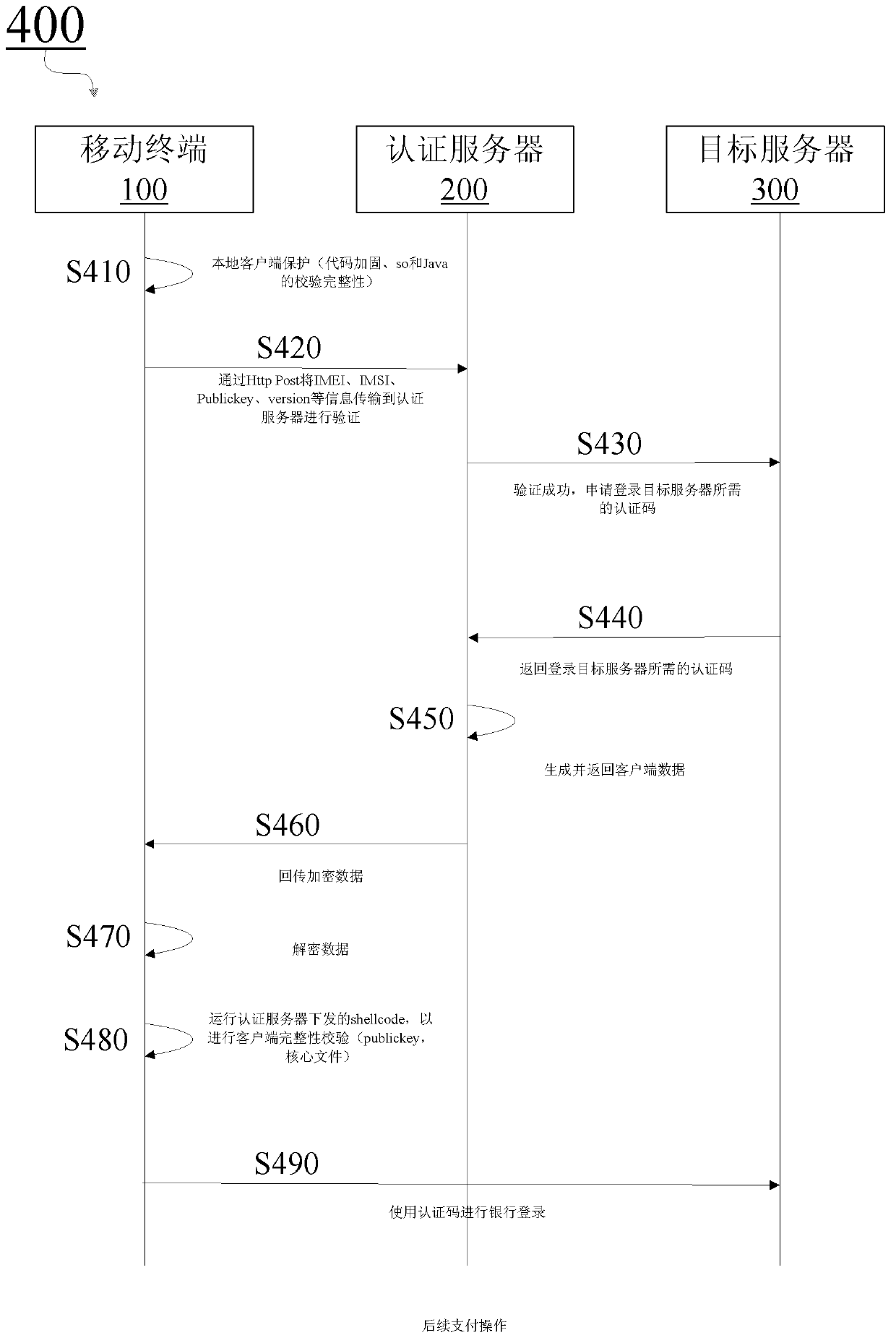
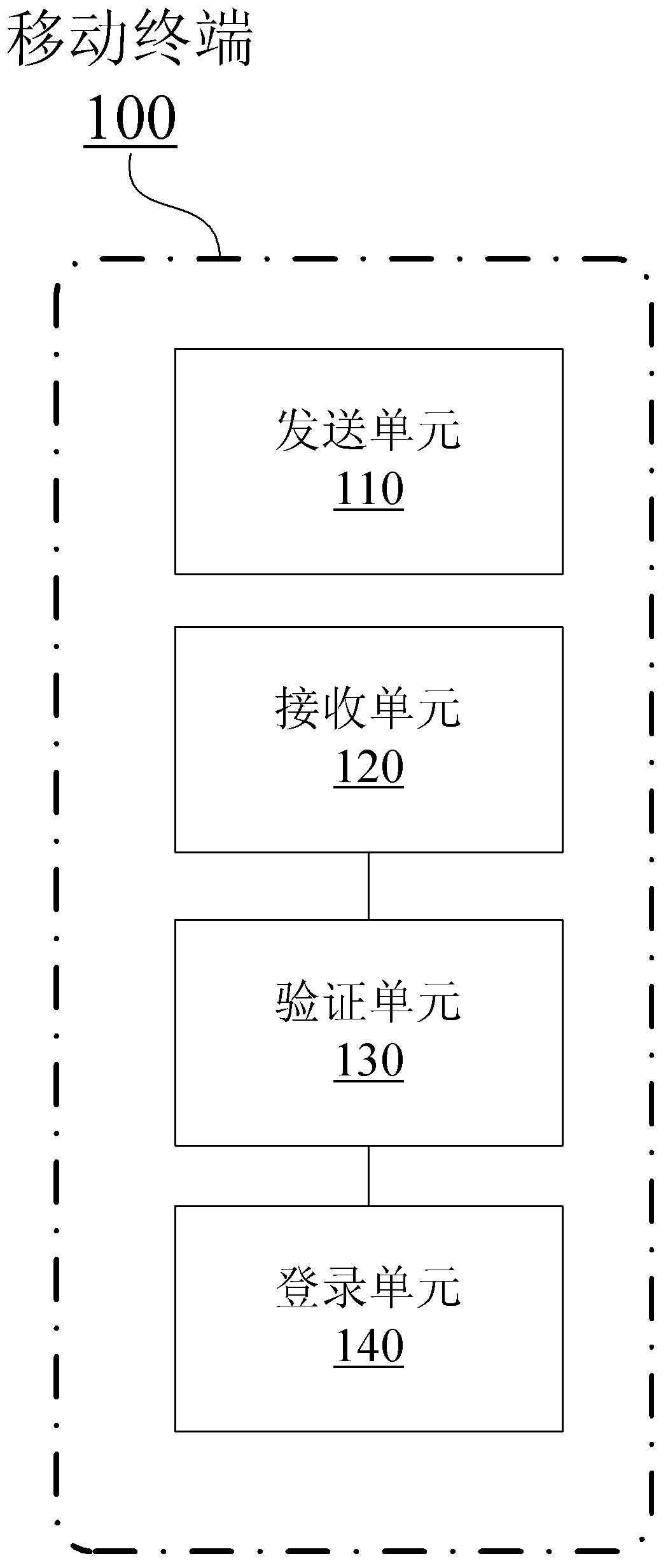
Security authentication method, equipment and system
InactiveCN103281187AReduce the possibility of tamperingIncrease the difficulty of crackingUser identity/authority verificationPayment architectureAuthentication serverSecurity authentication
The invention provides a security authentication method, which comprises the steps: (a) sending data related to an authentication client-side to an authentication server; (b) receiving client-side data formed by the authentication server based on the data related to the authentication client-side and authentication data returned by a target server from the authentication server; (c) using an executable code included in the client-side data to verify the safety of the authentication client-side; and (d) under the condition of determining the safety of the authentication client-side, using the authentication data to log in the target server.
Owner:BEIJING NETQIN TECH
System, method and device for providing vehicle information
InactiveCN108243223AReduce experienceReduce the possibility of tamperingCustomer relationshipBuying/selling/leasing transactionsThird partyThe Internet
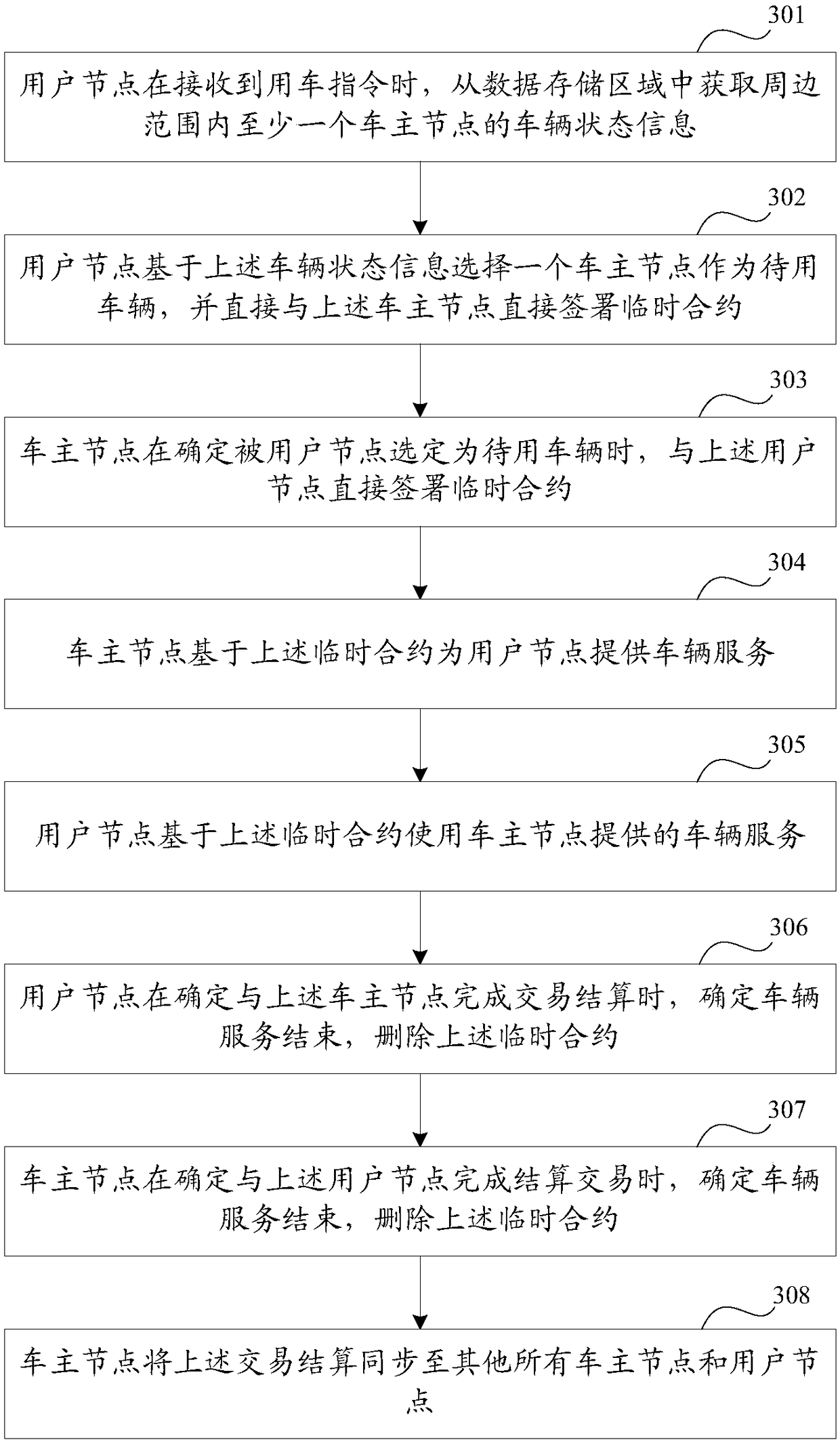
The invention relates to the internet-of-vehicle communication field and especially relates to a system, method and device for providing vehicle information. The method is characterized in that a usernode obtains vehicle state information of at least one vehicle owner node in a surrounding range, directly signs a temporary contract with one vehicle owner node selected based on the vehicle state information, and triggers the vehicle owner node to directly sign the temporary contract with the user node, to provide vehicle service for the user node based on the temporary contract and to delete the temporary contract when determining that the vehicle service ends. According to the method, the user node and the vehicle owner node no longer use a center node and no longer need a third-party platform as an interaction medium, and can directly finish service interaction, thereby preventing reduction of user experience due to slow system operating speed caused by large data storage at the center node side, reducing overall operating cost of the system, and meanwhile, reducing the possibility that the transaction settlement records between the user node and the vehicle owner node are tampered.
Owner:CHINA MOBILE COMM LTD RES INST +1
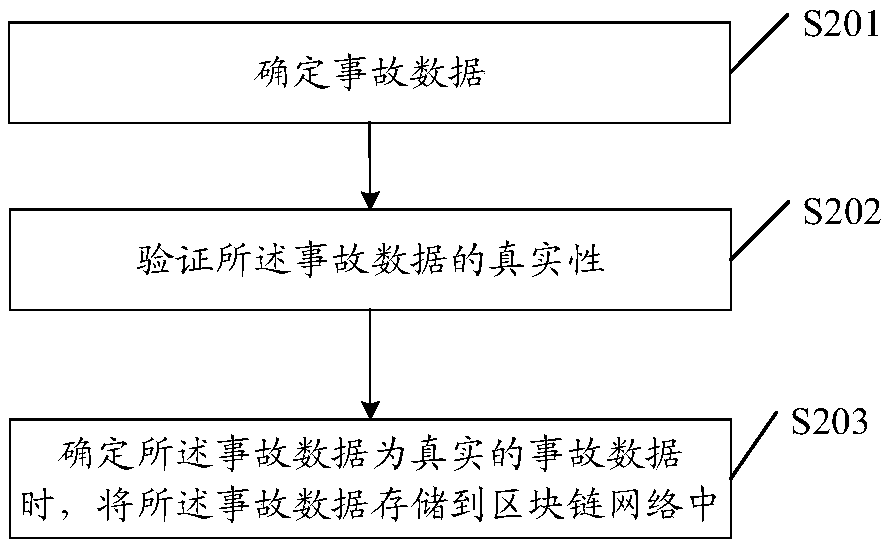
Accident data writing method and device, apparatus, and storage medium
InactiveCN109190402AReduce the possibility of tamperingEnsure integrity and correctnessDigital data protectionChain networkComputer science
An embodiment of the present application discloses an accident data writing method. The method comprises the following steps: determining accident data, wherein the accident data characterizes an accident situation at the time of an accident of a first vehicle; werifying the authenticity of the accident data; when it is determined that the accident data is real accident data, storing the accidentdata in a block chain network. In addition, embodiments of the present application also disclose an accident data writing apparatus, an apparatus, and a storage medium.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
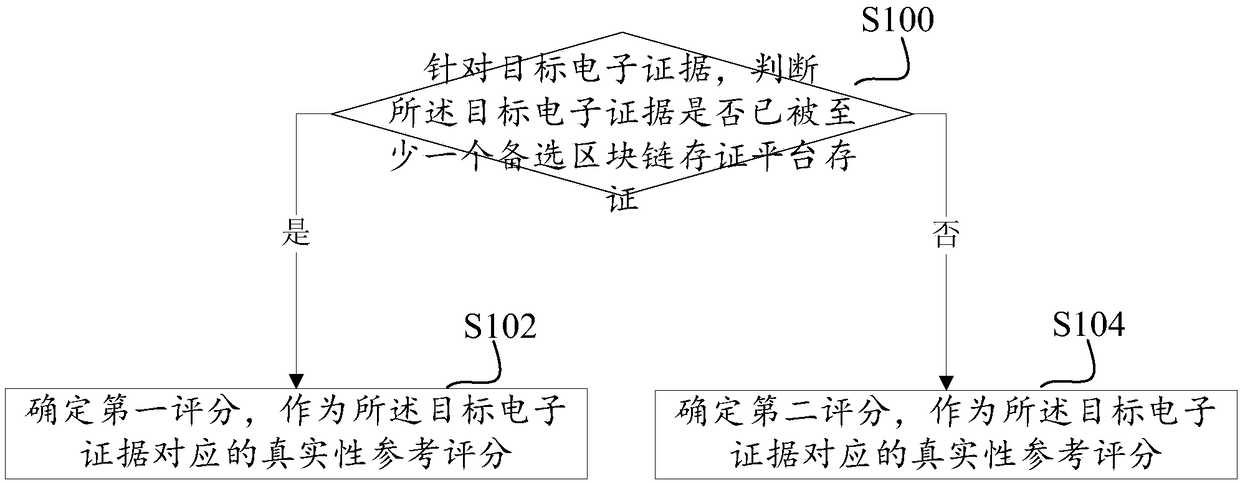
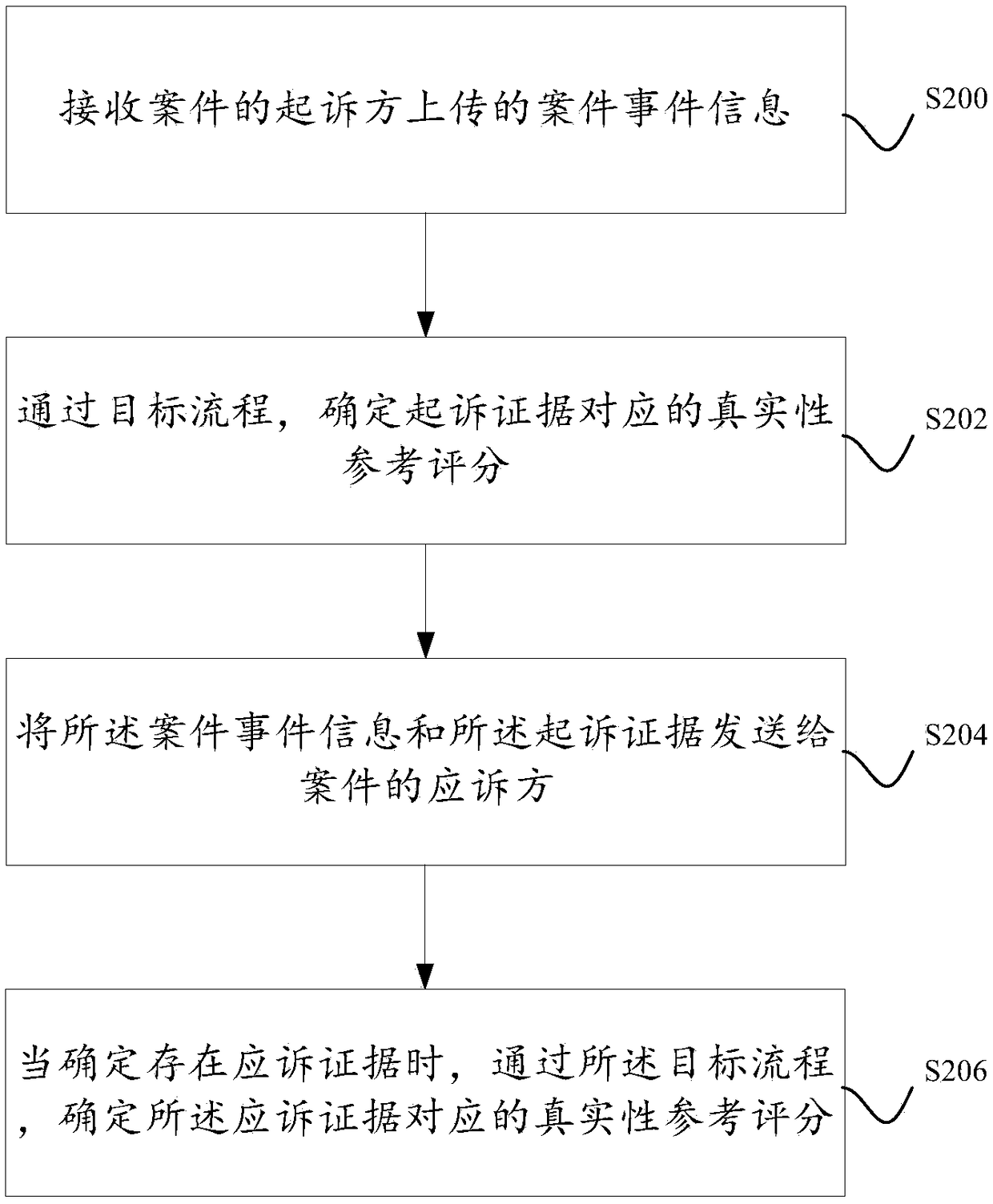
A method and apparatus for identifying authenticity of evidence of both parties based on block chain storage
InactiveCN109255628AHigh Authenticity Reference ScoreIncrease the degree of realismPayment protocolsEnergy efficient computingComputer scienceBlockchain
Disclosed are a method and apparatus for identifying authenticity of evidence of both parties based on a block chain storage. According to the prosecutor's claim of a real case event, on the one hand,the prosecutor can identify the prosecution evidence used to confirm the case event through the objective process, on the other hand, the respondent can identify the evidence used to falsify the caseevent through the objective process. Wherein the target flow includes: identifying the electronic evidence of the target, giving a higher authenticity reference score to the target electronic evidence when it is determined that the target electronic evidence has been deposited by the at least one alternative block chain depository platform, and giving a lower authenticity reference score to the target electronic evidence when it is determined that the target electronic evidence has not been deposited by the at least one alternative block chain depository platform.
Owner:ADVANCED NEW TECH CO LTD
Data management method and device based on block chain
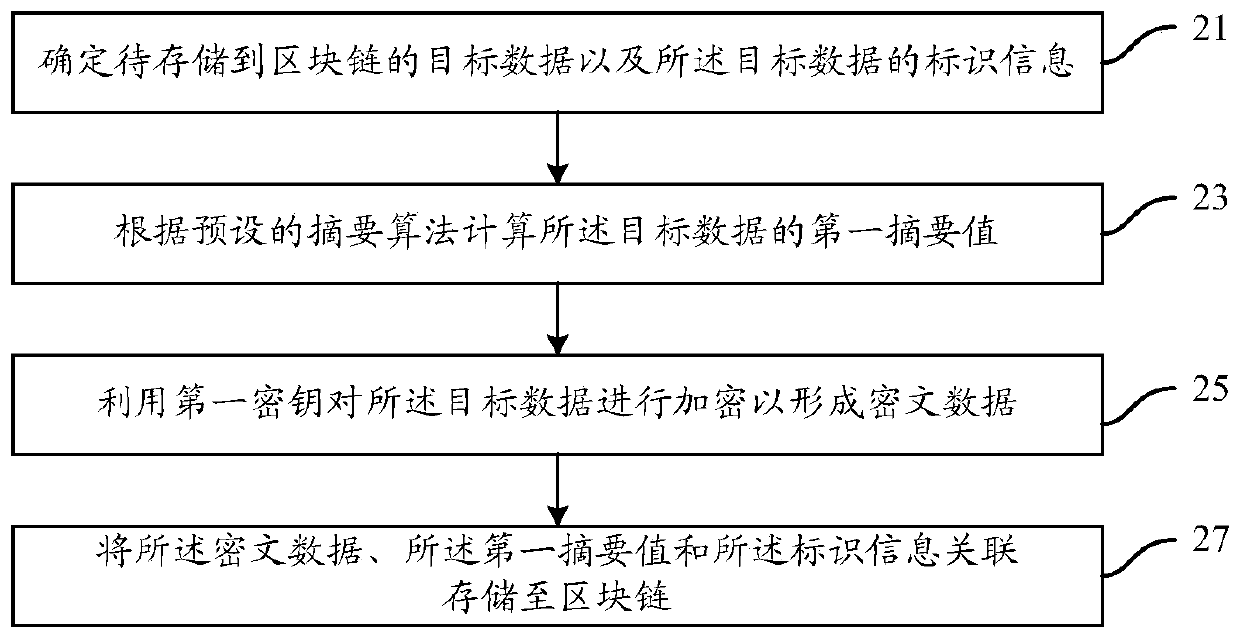
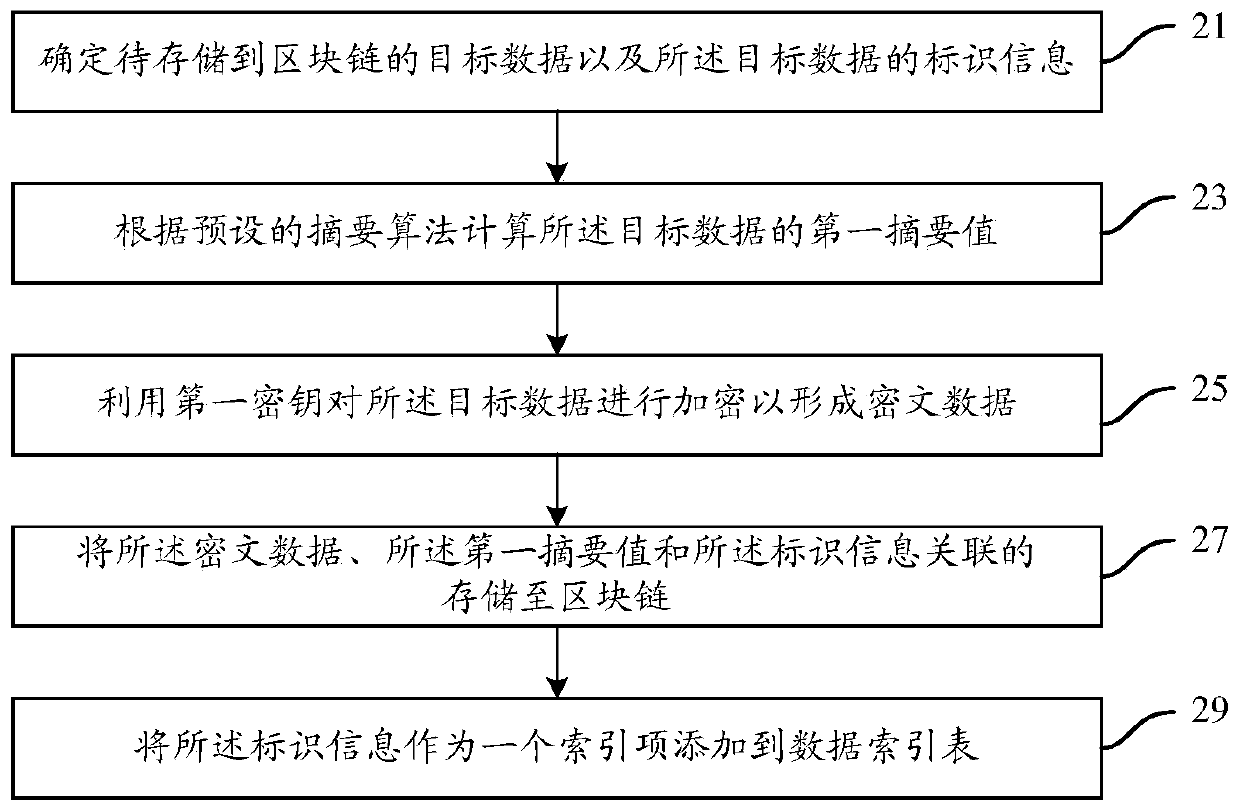
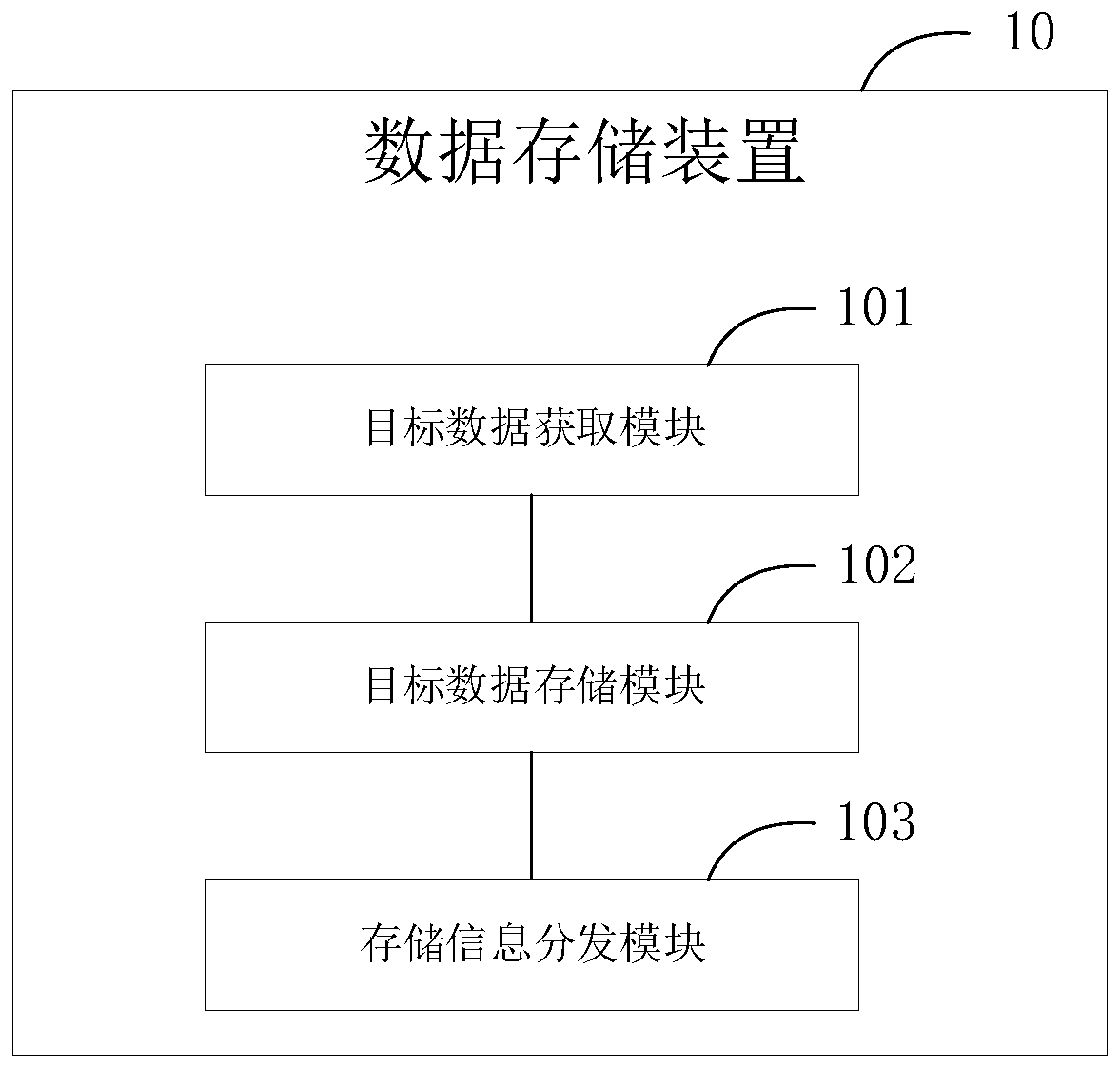
PendingCN110851843APrevent theftPrevent tamperingDigital data protectionCiphertextTheoretical computer science
The embodiment of the invention discloses a data management method and device based on a block chain, the data management method and device based on the block chain are applied to terminal equipment,and the method at least can comprise the following steps: determining target data to be stored in the block chain and identification information of the target data; calculating a first abstract valueof the target data according to a preset abstract algorithm; encrypting the target data by using a first key to form ciphertext data; and associatively storing the ciphertext data, the first abstractvalue and the identification information to a block chain. Through the technical scheme of the embodiment of the invention, the data can be more effectively prevented from being stolen and tampered byan intruder, so that the security of the data is improved.
Owner:LI ZHAN SHANGHAI TECH CO LTD
Confidential file protection method
InactiveCN101273366ADefense against improper access behaviorReduce the frequency of issuing certification requestsDigital data protectionDigital data authenticationInternet privacyApplication software
Owner:HITACHI SOFTWARE ENG
Internet of things communication method, platform, terminal and system
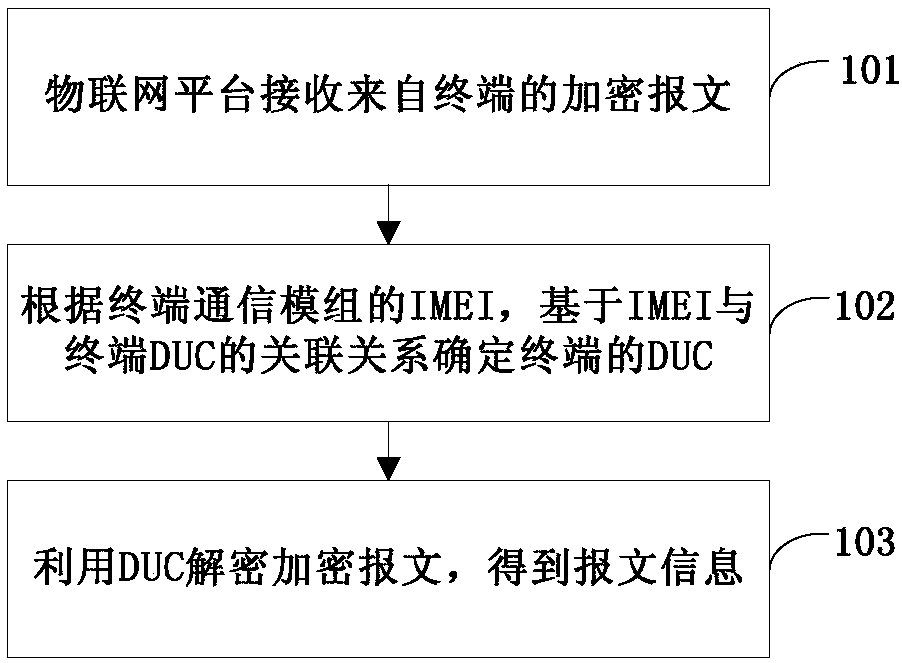
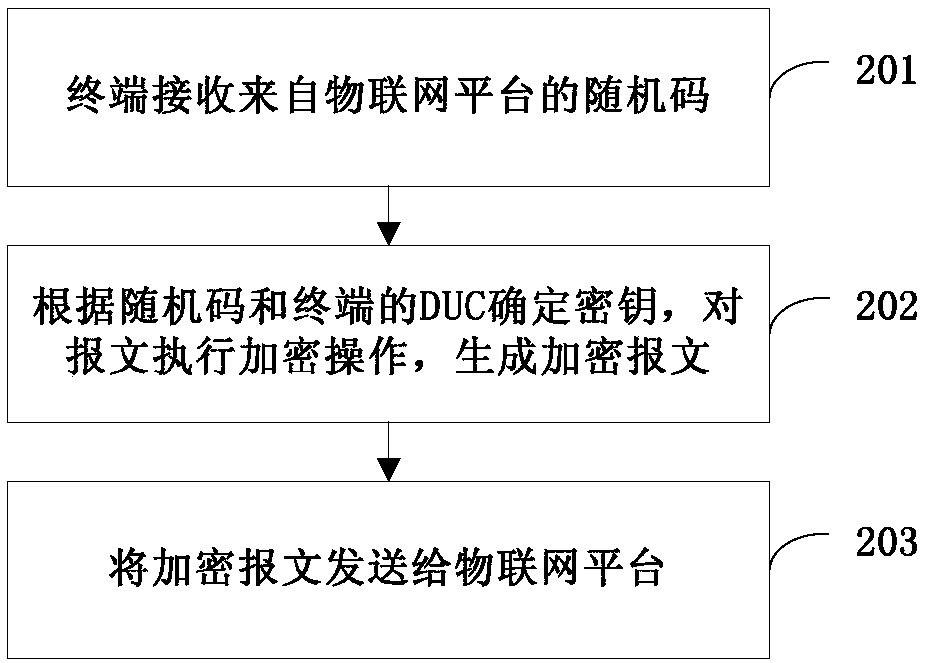
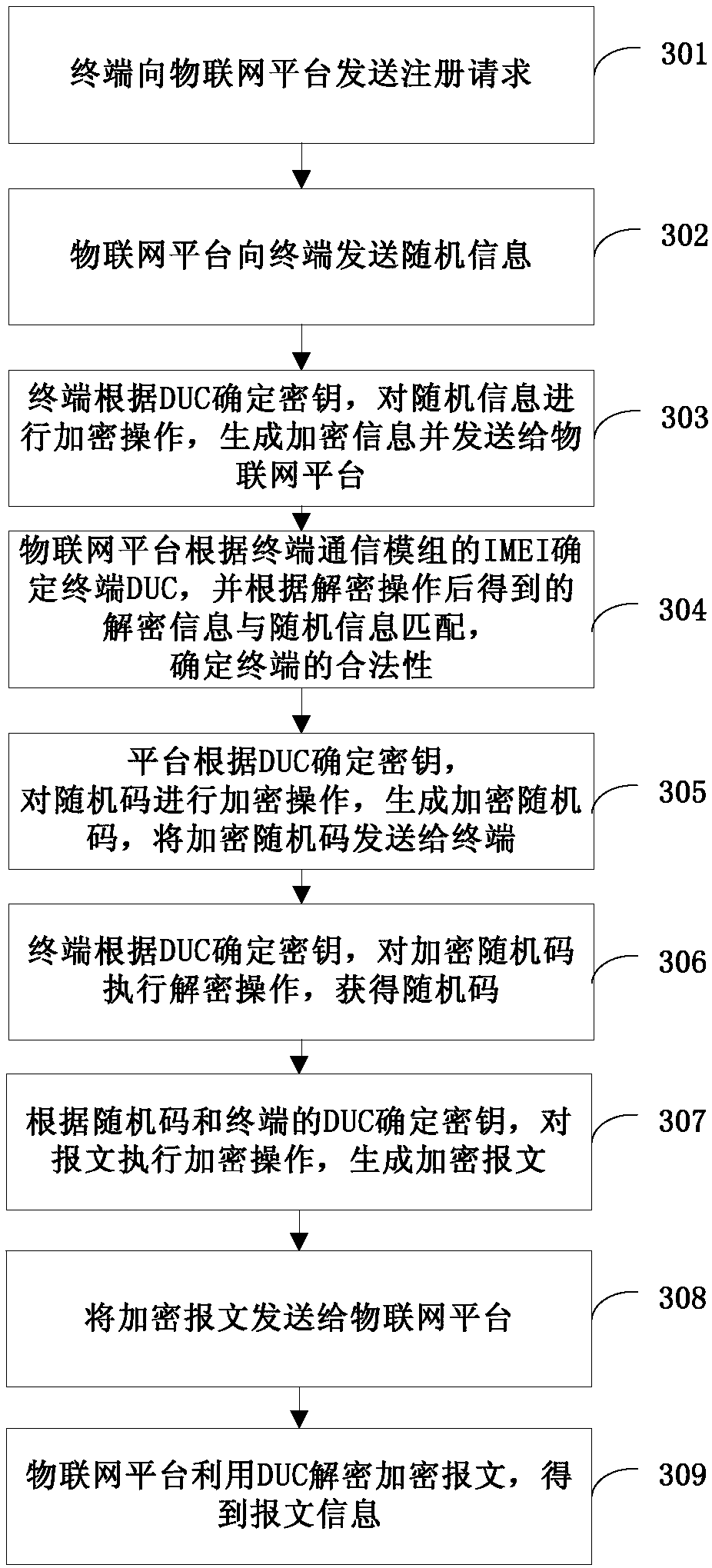
InactiveCN109922022AImprove reliabilityReduce attackKey distribution for secure communicationThe InternetComputer terminal
The invention provides an Internet of Things communication method, platform, terminal and system, and relates to the technical field of Internet of Things. The Internet of Things communication methoddisclosed by the invention comprises the following steps: an Internet of Things platform receives an encrypted message from a terminal; a DUC (Device Unique Code) of the terminal is determined based on the association relationship between the IMEI (International Mobile Equipment Identity) and the DUC according to the IMEI of the terminal communication module; and the encrypted message is decryptedby using the DUC to obtain message information. Through the method, the Internet of Things terminal and the platform can utilize the DUC as a secret key to perform encryption and data interaction, and the DUC is not transmitted in the interaction process, so that the encryption reliability is improved, and the possibility of attack and data tampering is reduced.
Owner:CHINA TELECOM CORP LTD
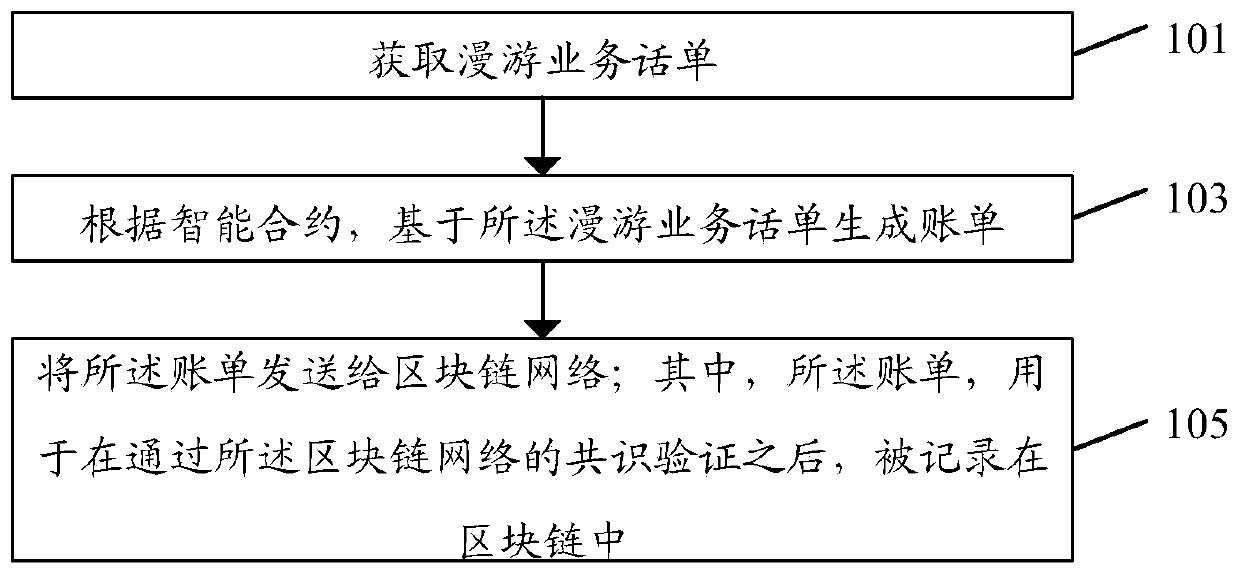
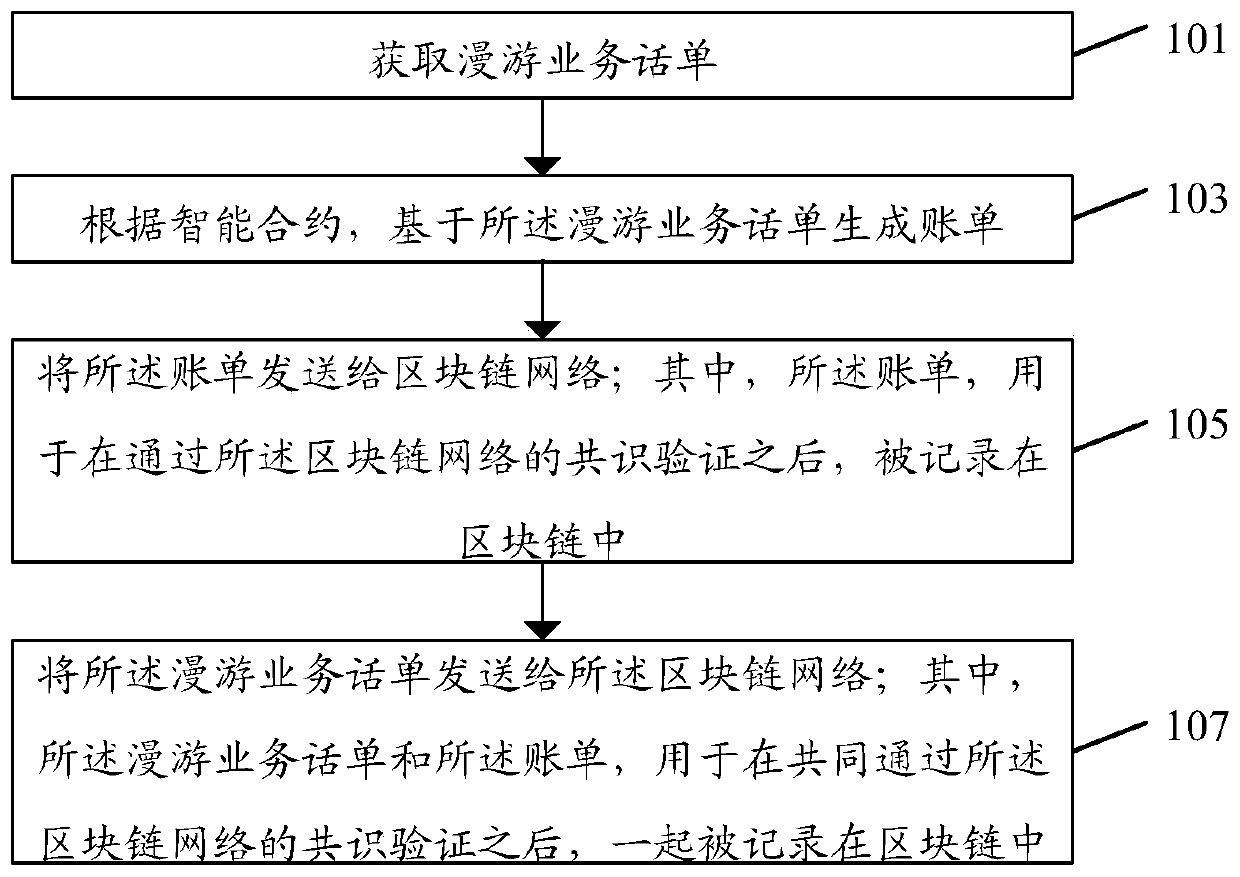
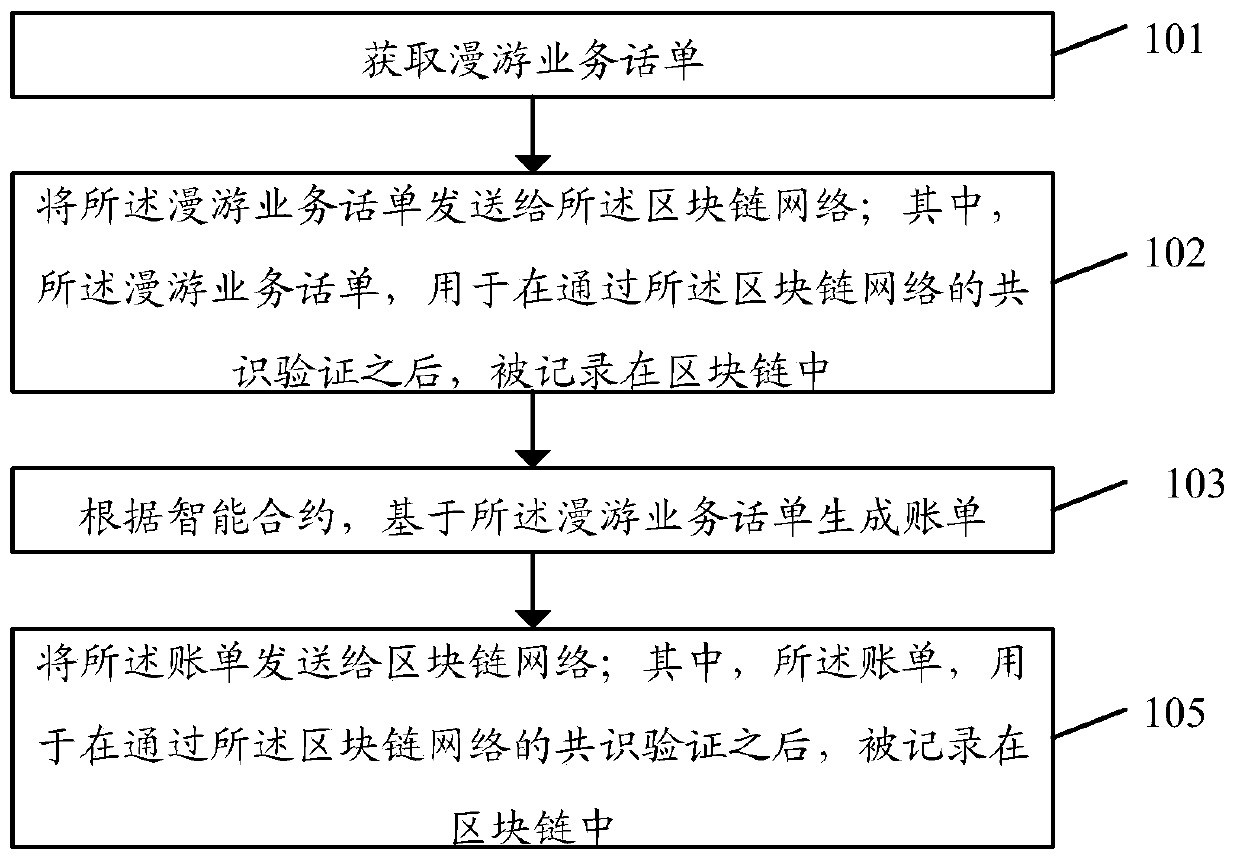
Bill processing method and system for roaming service and storage medium
ActiveCN111405505AReduce consistencyReduce the possibility of tamperingAccounting/billing servicesTelephonic communicationTelecommunicationsChain network
The embodiment of the invention discloses a bill processing method for a roaming service. The method comprises the following steps: acquiring a roaming service bill; generating a bill based on the roaming service ticket according to the intelligent contract; sending the bill to a block chain network; wherein the bill is used for being recorded in the block chain after passing the consensus verification of the block chain network. The embodiment of the invention further discloses a bill processing system of the roaming service and a storage medium.
Owner:CHINA MOBILE COMM LTD RES INST +1
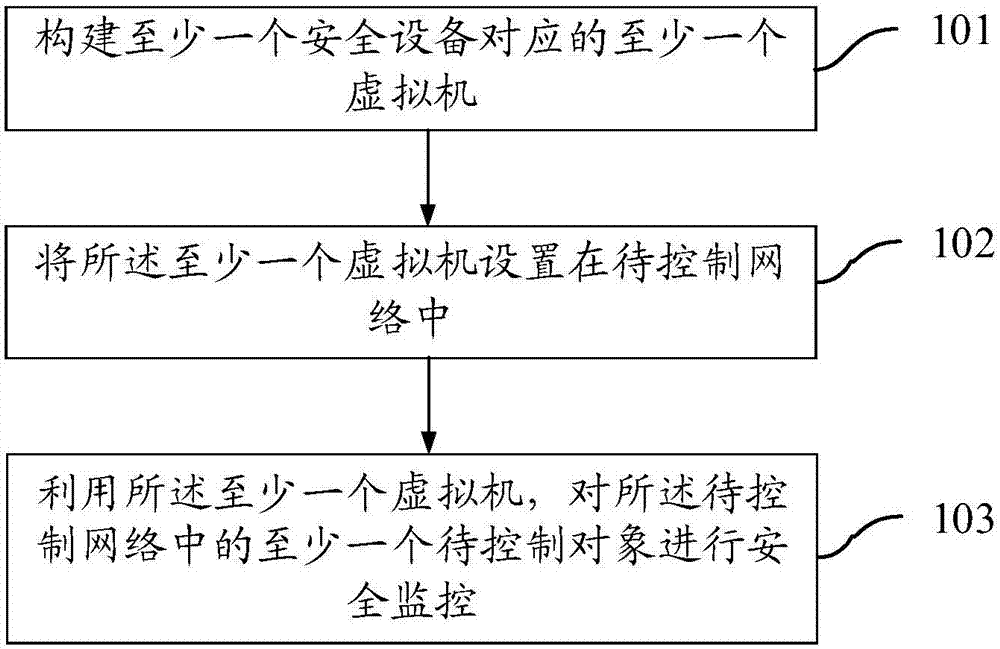
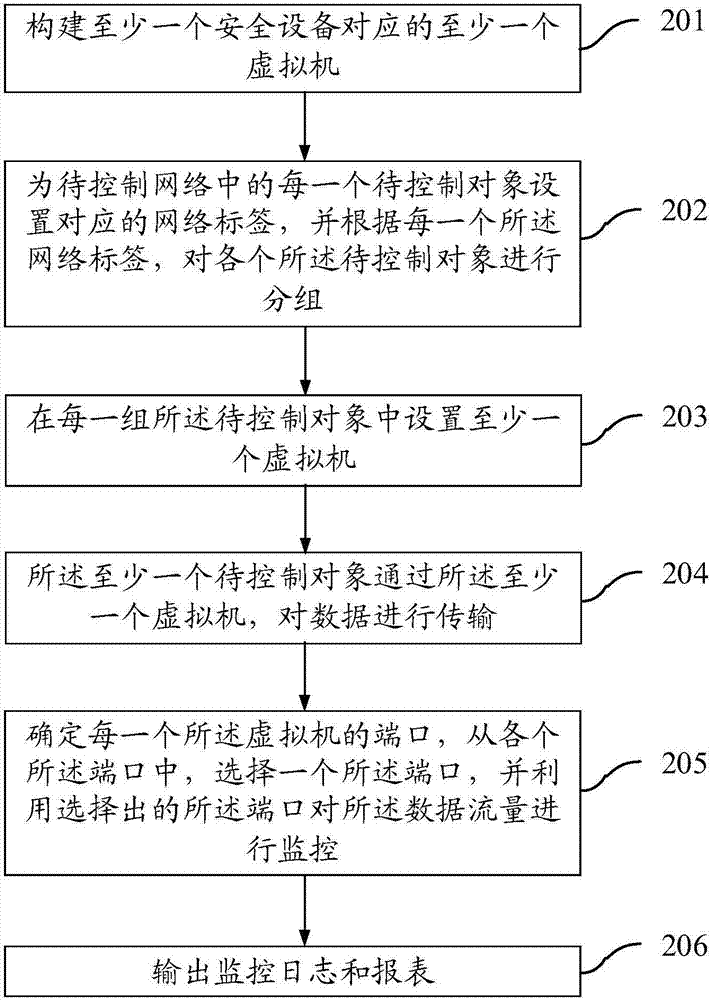
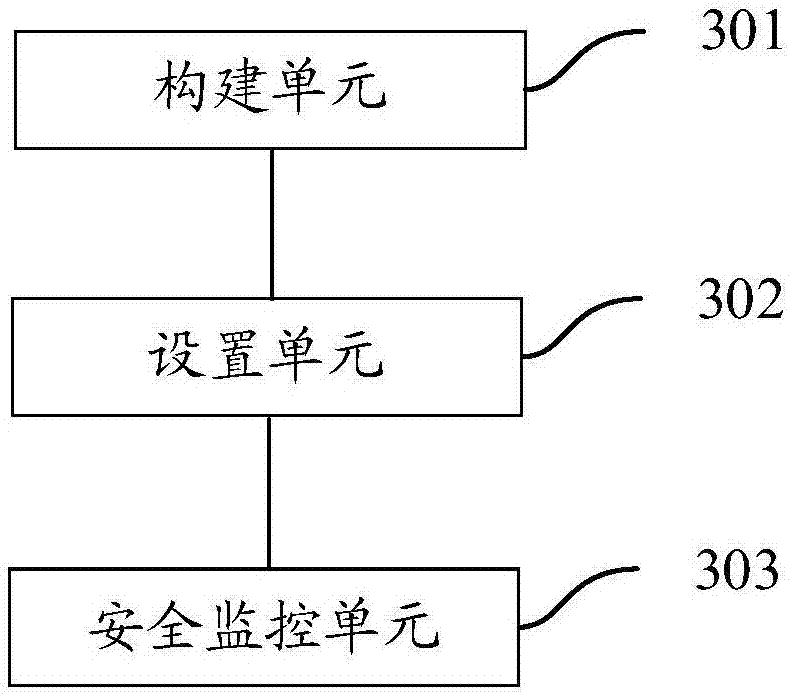
Network security control method and device
InactiveCN107046546AReduce attackReduce the possibility of tamperingTransmissionSoftware simulation/interpretation/emulationSecurity monitoringVirtual machine
The invention provides a network security control method and device. The method comprises the following steps: constructing at least one virtual machine corresponding to at least one piece of security equipment; arranging the at least one virtual machine in a network to be controlled; and performing security monitoring on at least one object to be controlled in the network to be controlled by using the at least one virtual machine. Through the scheme, the data security can be enhanced.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
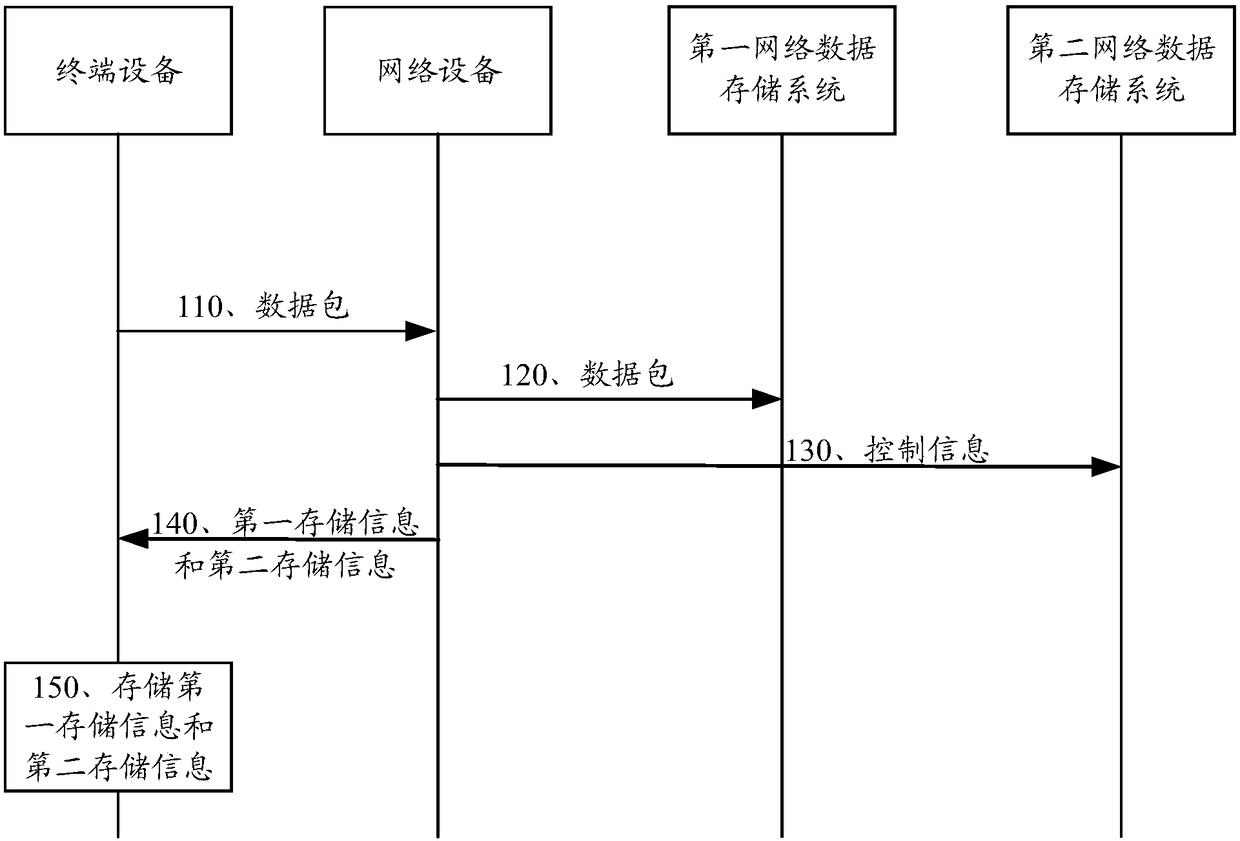
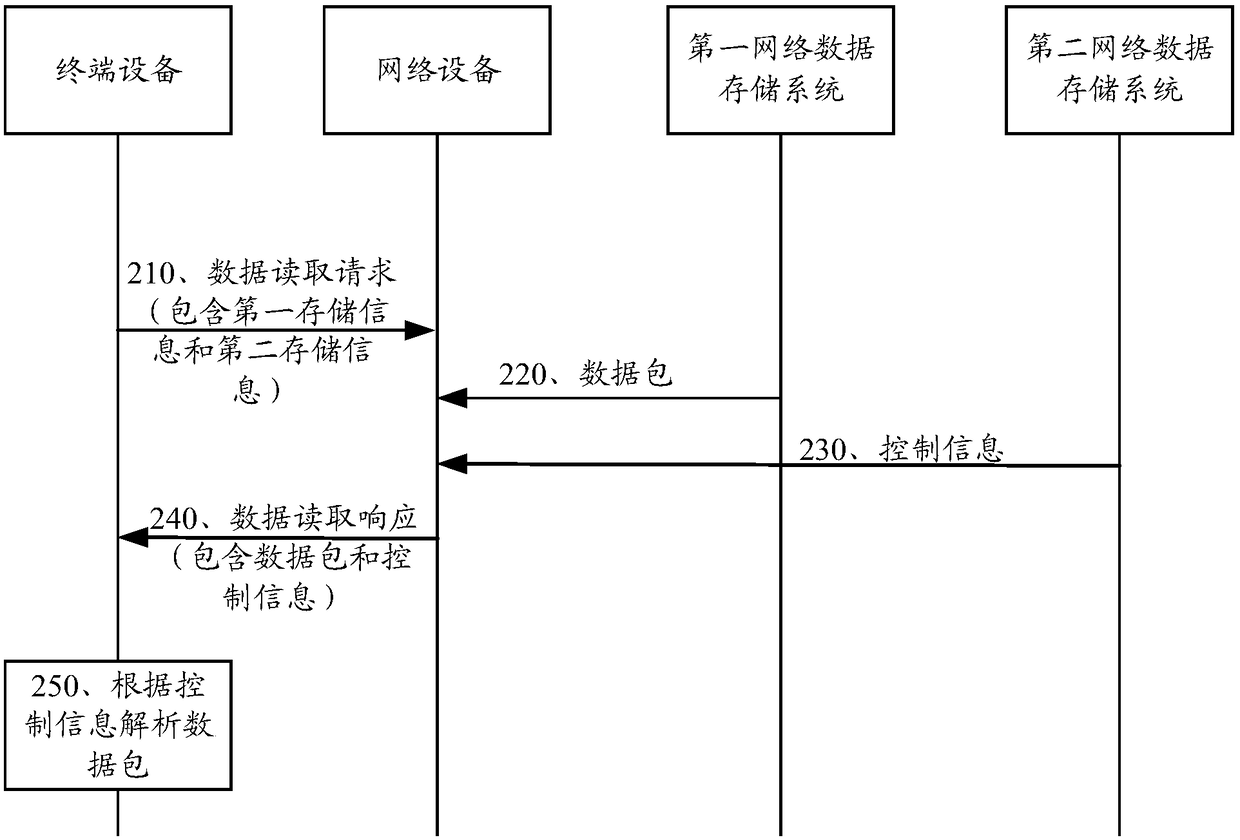
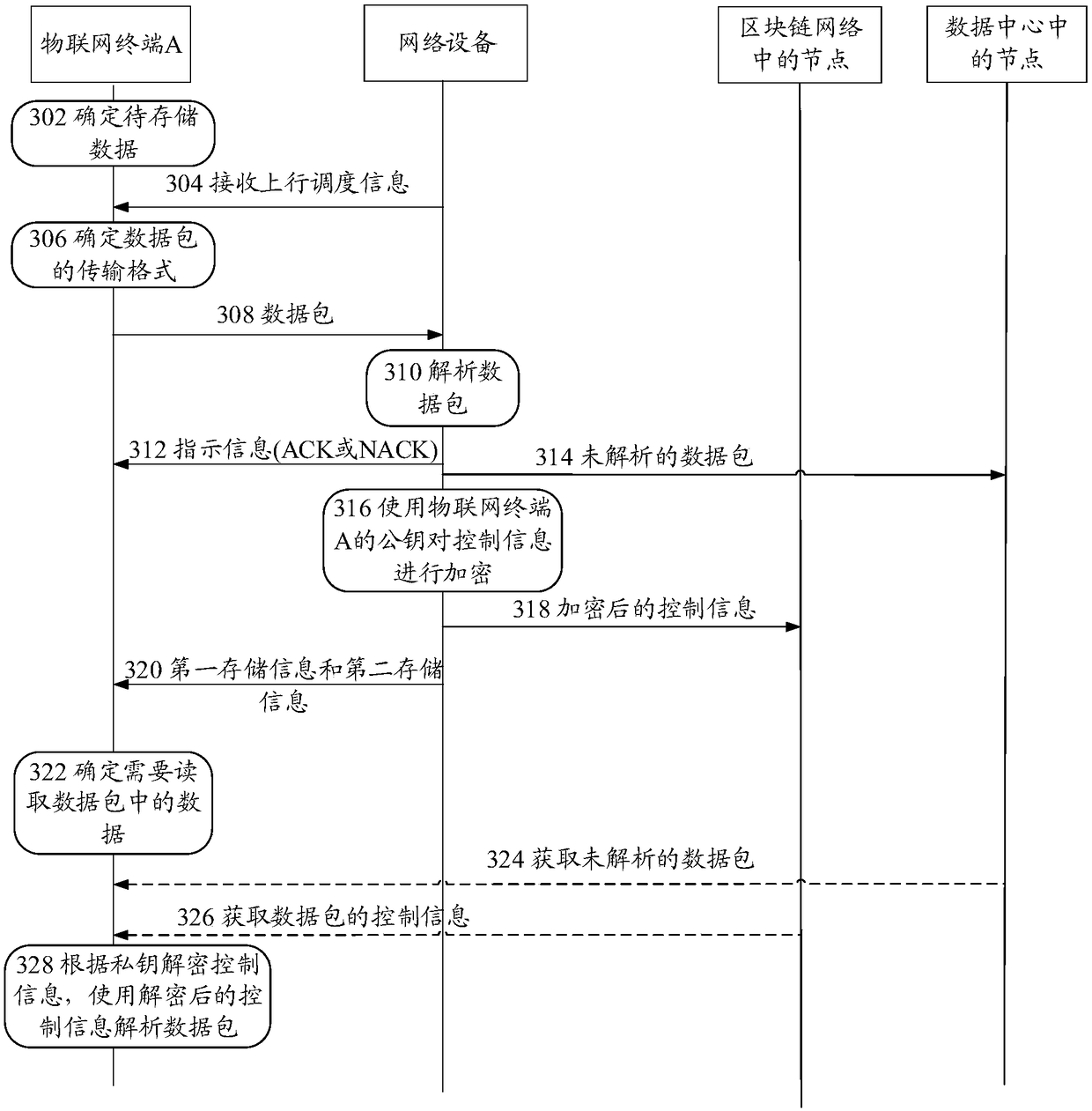
Data processing method, terminal device and network device
The invention provides a data processing method, a terminal device and a network device. The data processing method comprises the steps that: the network device receives a data packet comprising to-be-stored data sent by the terminal device; the network device stores the data packet in a first network data storage system, and stores control information of the data packet in a second network data storage system, wherein the control information is used for indicating the transmission format of the data packet; and at least one of the first network data storage system and the second network datastorage system is a blockchain network. By means of the technical scheme provided in the invention, the network data storage security can be improved.
Owner:SUZHOU YUDESHUI ELECTRIC TECH CO LTD
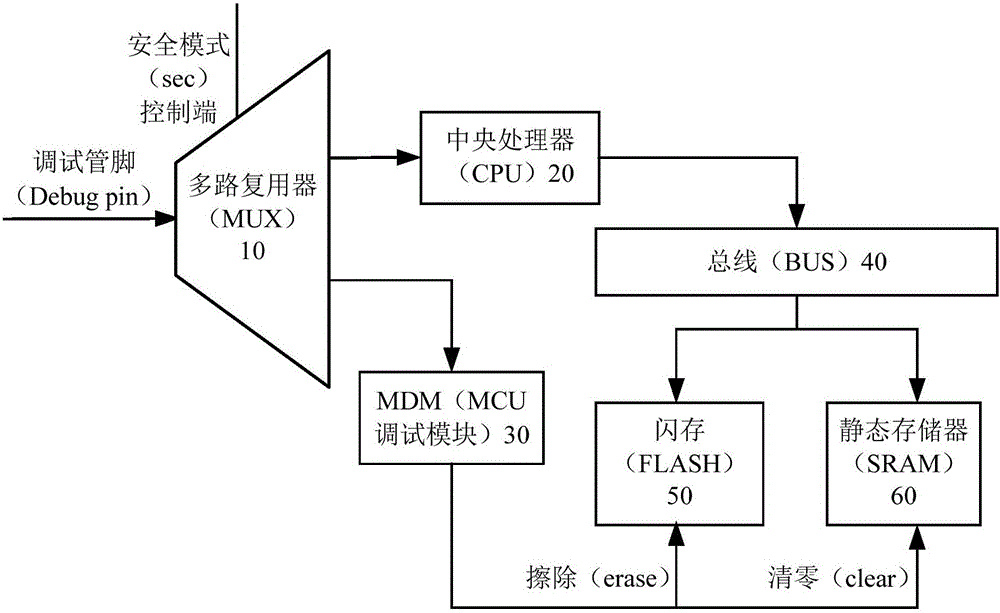
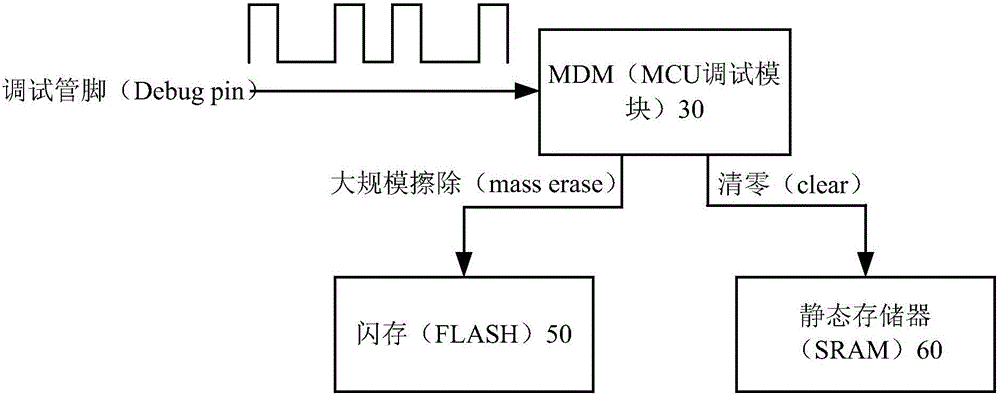
MCU, terminal and control method
ActiveCN105843112AReduce the possibility of tamperingImprove securityProgramme controlComputer controlInput selectionComputer module
Owner:珠海艾维普信息技术有限公司 +1
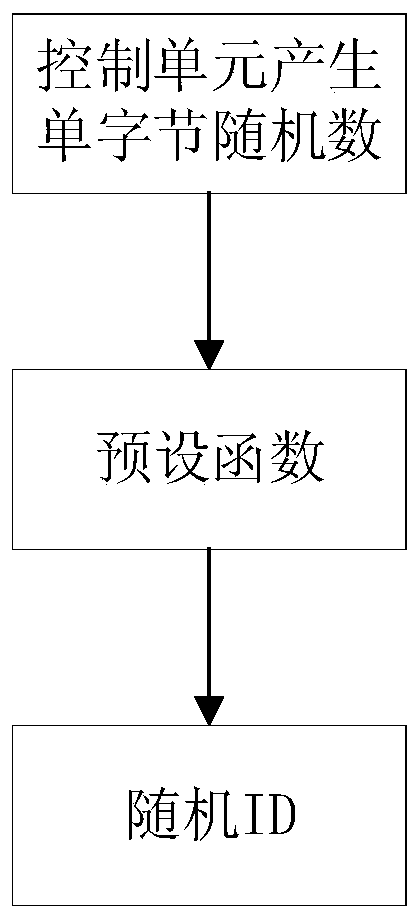
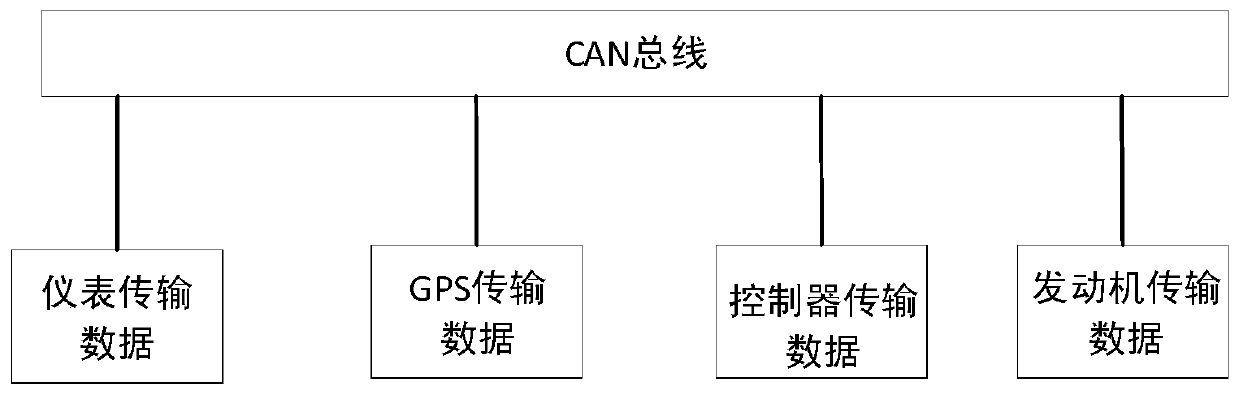
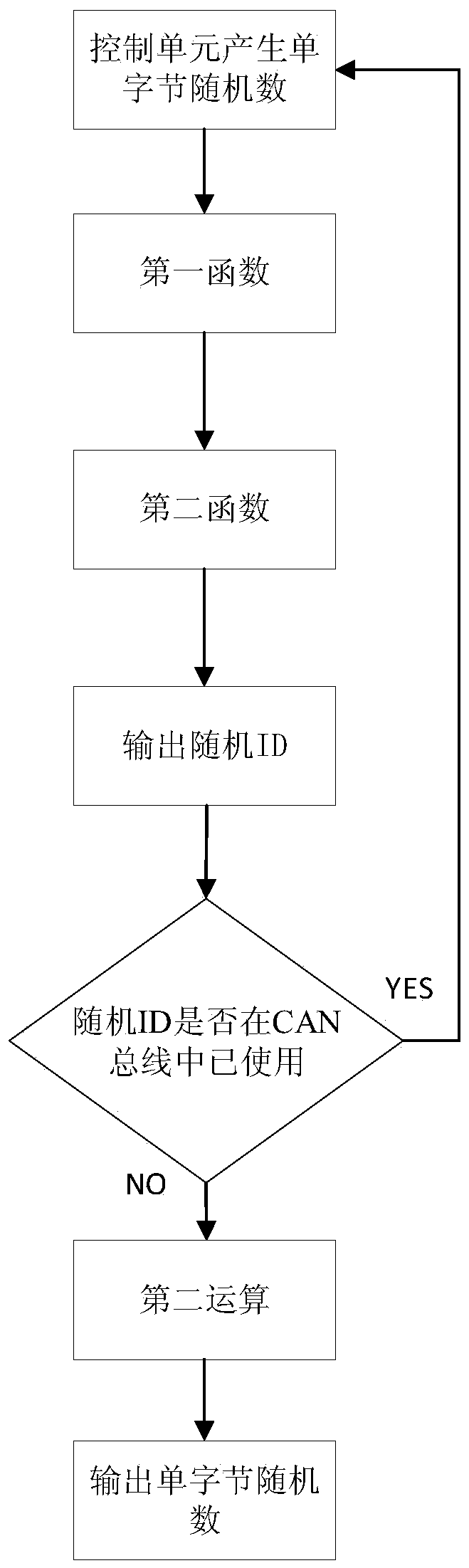
CAN bus data encryption and decryption method and device
ActiveCN110247760AImprove securityAvoid economic lossKey distribution for secure communicationBus networksBus encryptionByte
The invention provides a CAN bus data encryption and decryption method and device, and the method comprises the steps: generating a single-byte random number through a control unit, and enabling the range of the single-byte random number to be 1-255, processing the single-byte random number by a preset function to obtain a random ID with an ID domain of 29 bits, wherein the preset function is a reversible function, and the random ID for sending the encrypted data is random each time, data security is improved, the economic loss caused by modification of important parameters (hours, GPS parameters) of a service and leasing unit is avoided, at least two random IDs can be sent each time, and the true value exists in one random ID, so that the possibility that the CAN bus data is tampered is reduced, and the data security is greatly improved.
Owner:XCMG EXCAVATOR MACHINERY
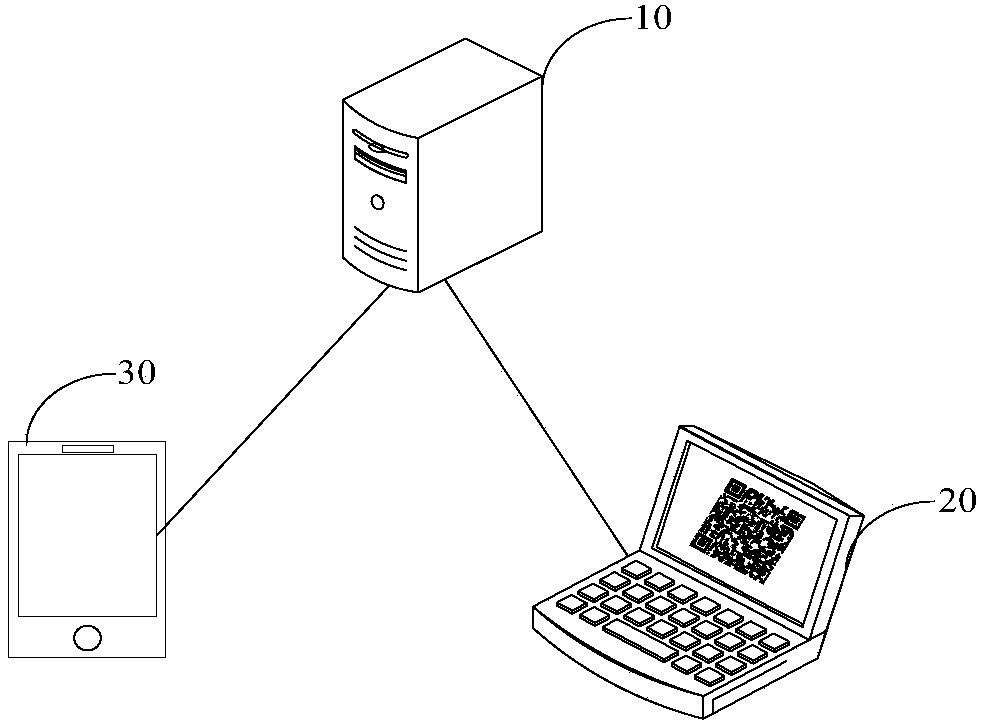
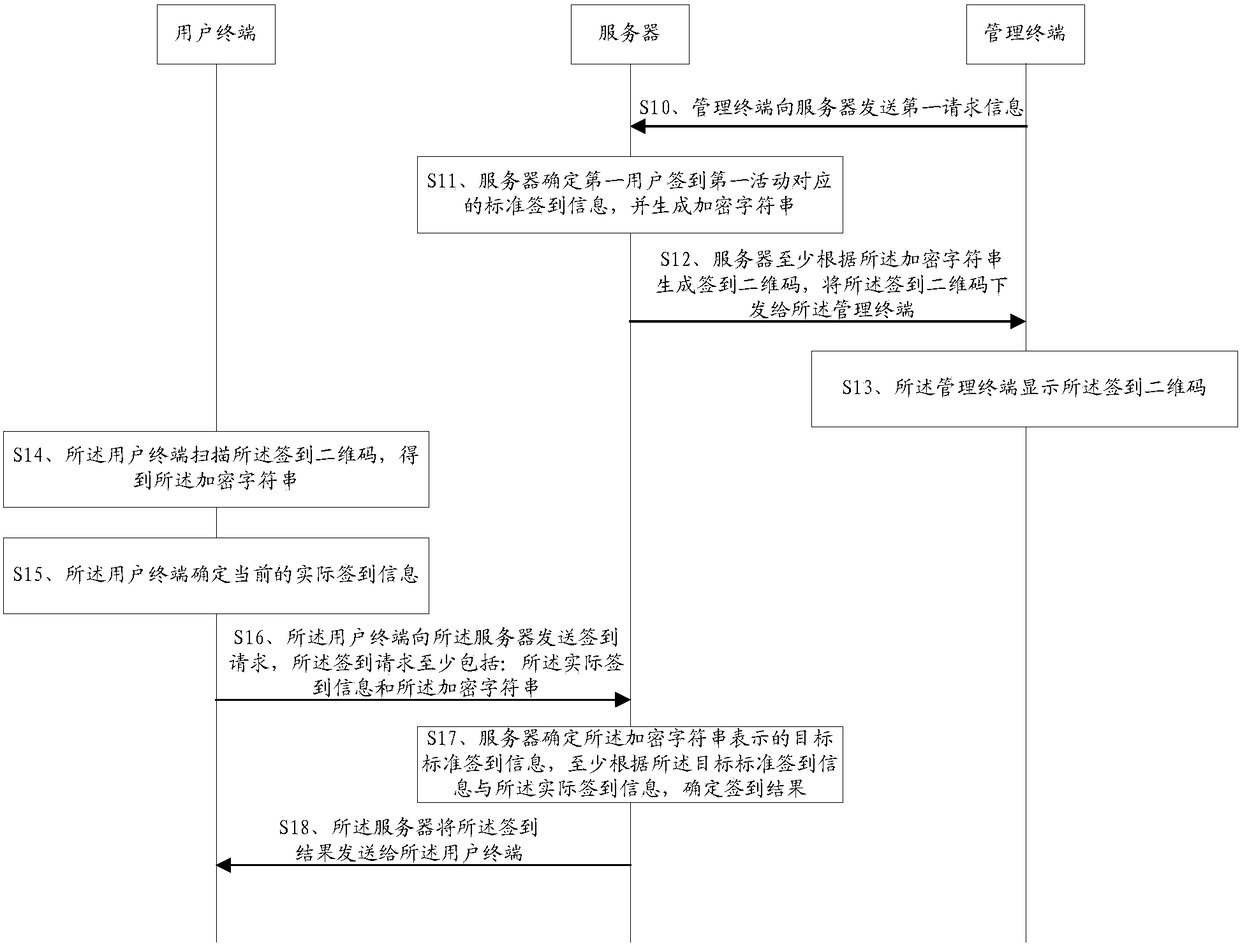
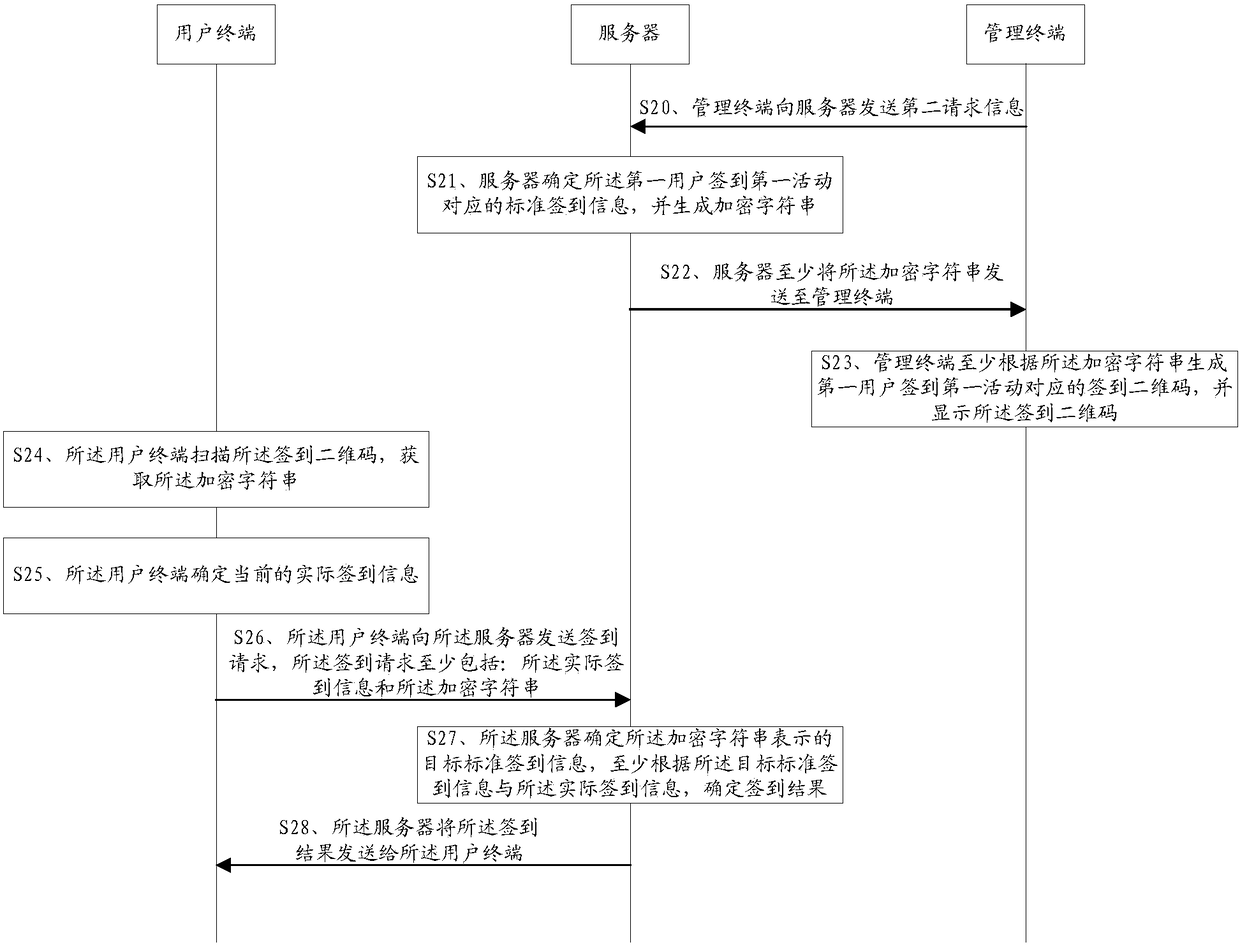
Activity sing-in method, user terminal, server and system
ActiveCN108737339AImprove accuracyReduce the possibility of tamperingTransmissionRecord carriers used with machinesComputer terminalReal-time computing
The embodiment of the invention provides an activity sing-in method, a user terminal, a server and a system. The method comprises the following steps: scanning a corresponding sign-in two-dimensionalcode that a first user signs in a first activity by the user terminal; parsing the sign-in two-dimensional code, and acquiring an encrypted character string; determining current actual sign-in information, wherein the actual sign-in information at least comprises the identity of a current sign-in user; sending a sign-in request to the server, so that the server determines a sign-in result at leastaccording to target standard sign-in information and the actual sign-in information indicated by the encrypted character string, wherein the sign-in request at least comprises the actual sign-in information and the encrypted character string; and receiving the sign-in result sent by the server. The activity sing-in method provided by the embodiment of the invention can improve the accuracy of thesign-in result.
Owner:TENCENT TECH (SHENZHEN) CO LTD
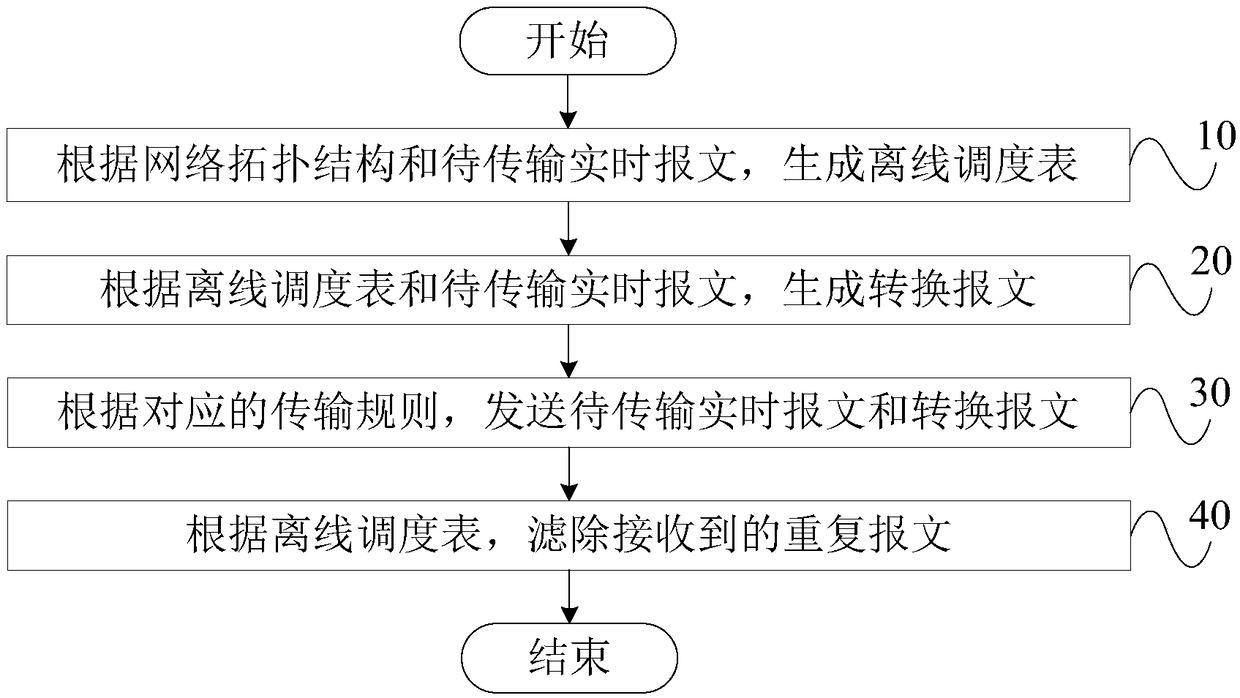
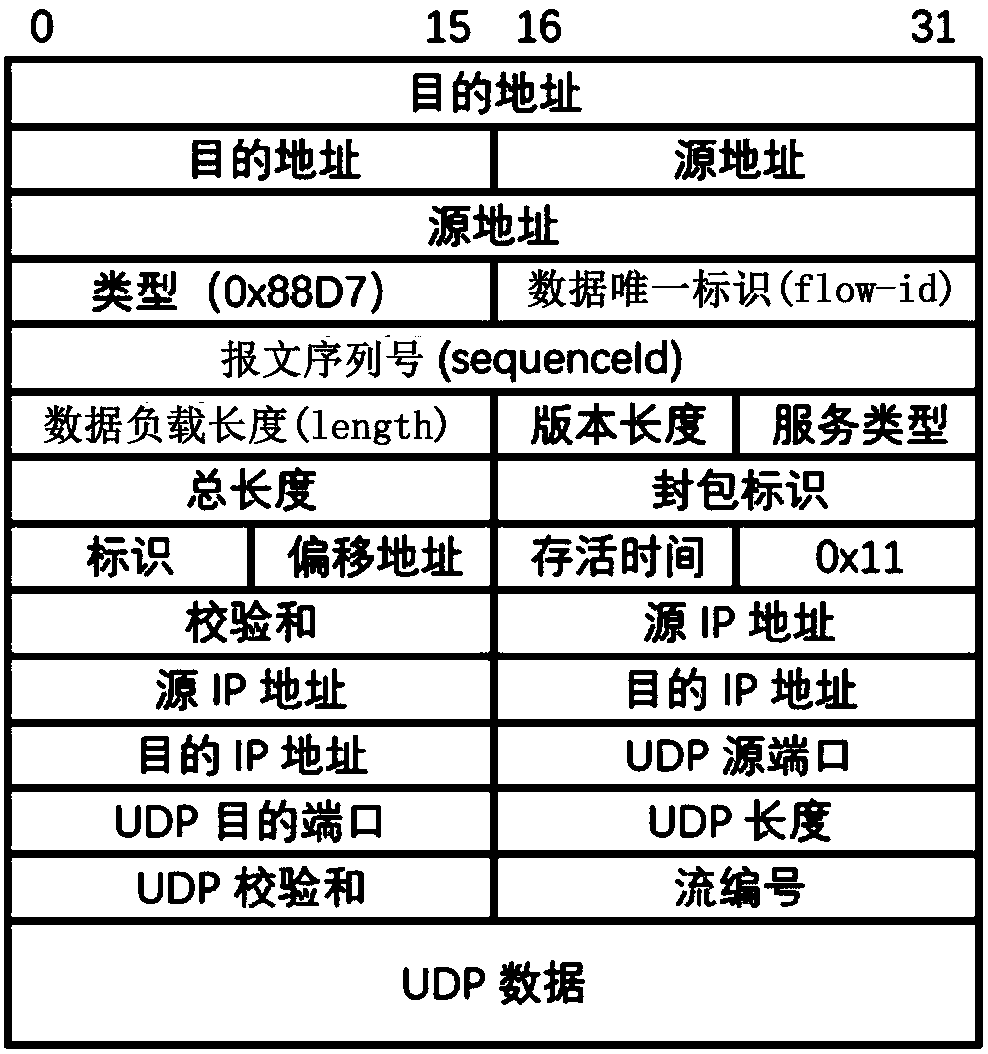
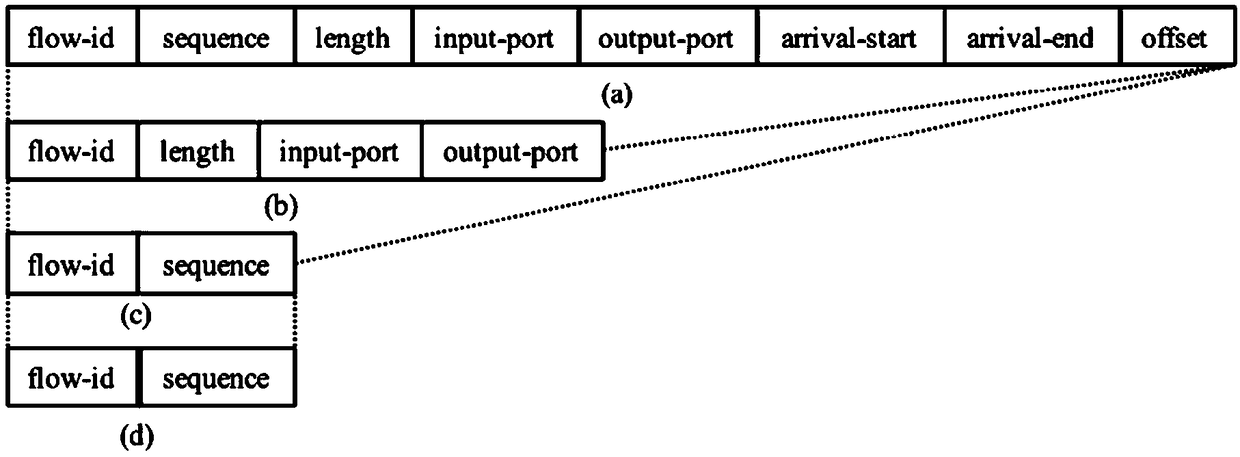
A real-time Ethernet scheduling method for transmitting real-time data
The invention discloses a real-time Ethernet scheduling method for transmitting real-time data. The method comprises the following steps: step 10, generating an offline scheduling table according to anetwork topology structure and a real-time message to be transmitted; step 20, generating a conversion message according to an offline schedule table and a real-time message to be transmitted, wherein that conversion message is a non-real-time message; Step 30, according to the corresponding transmission rule, sending the real-time message to be transmitted and the conversion message; Step 40, according to the offline scheduling table, filtering the received duplicate message, wherein, the duplicate message is a message to be transmitted with the same data unique identification or a convertedmessage with the same data unique identification. By adopting the technical proposal of the invention, the accuracy of transmitting the real-time message is ensured, the time delay in the process oftransmitting the real-time message is reduced, and the utilization rate of the data transmission bandwidth is improved.
Owner:TSINGHUA UNIV
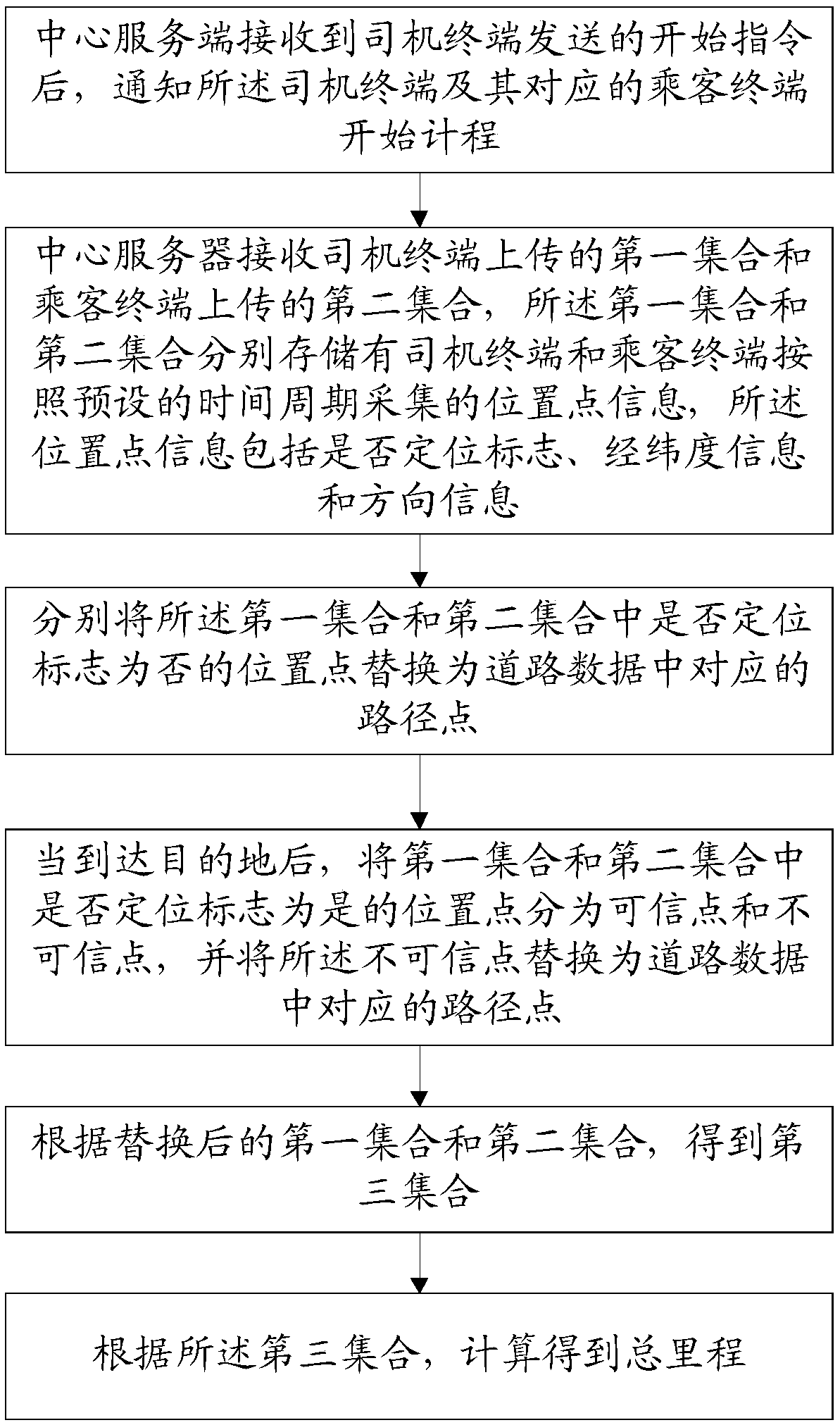
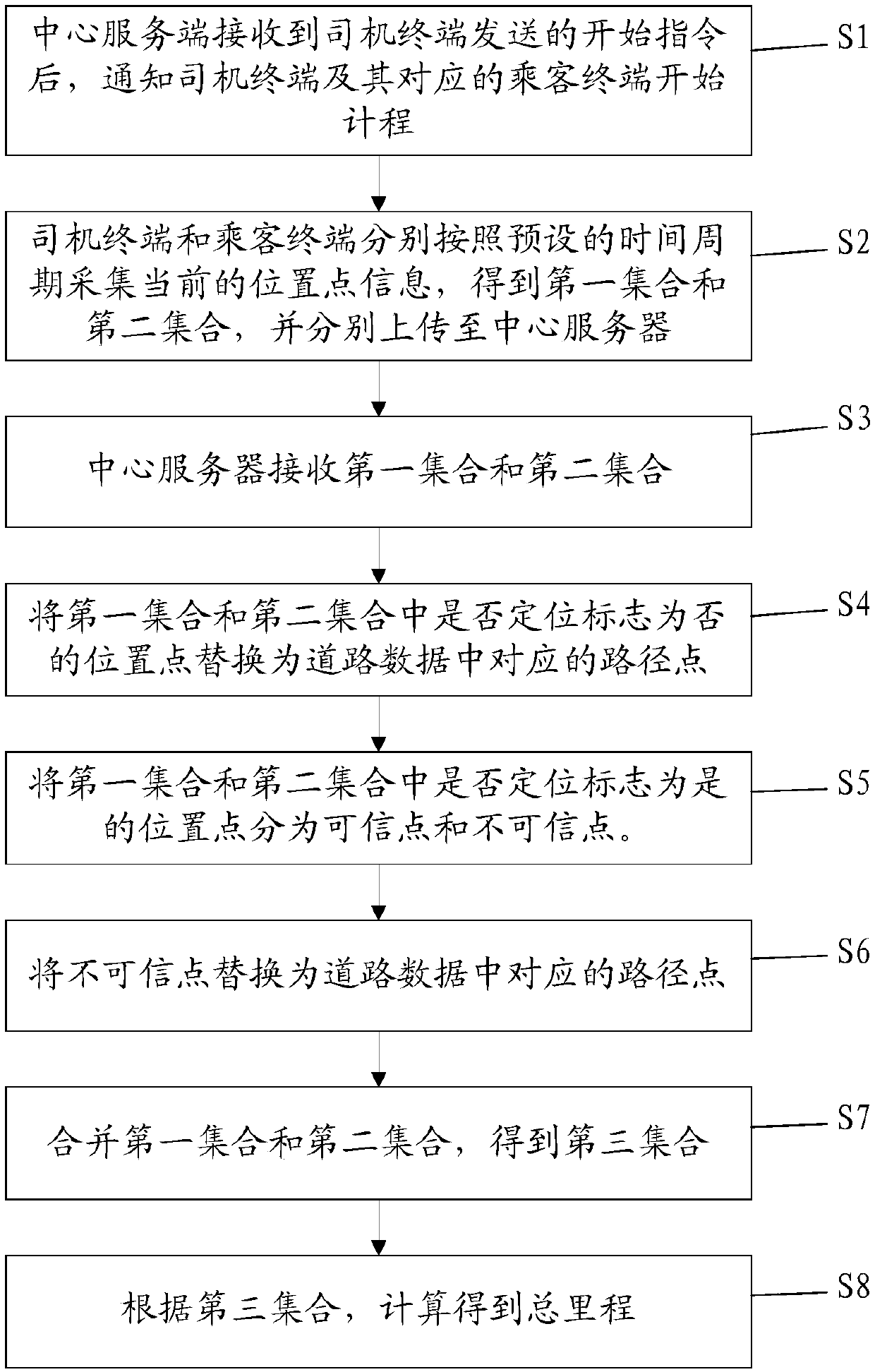
Online car-hailing metering method and computer readable storage medium
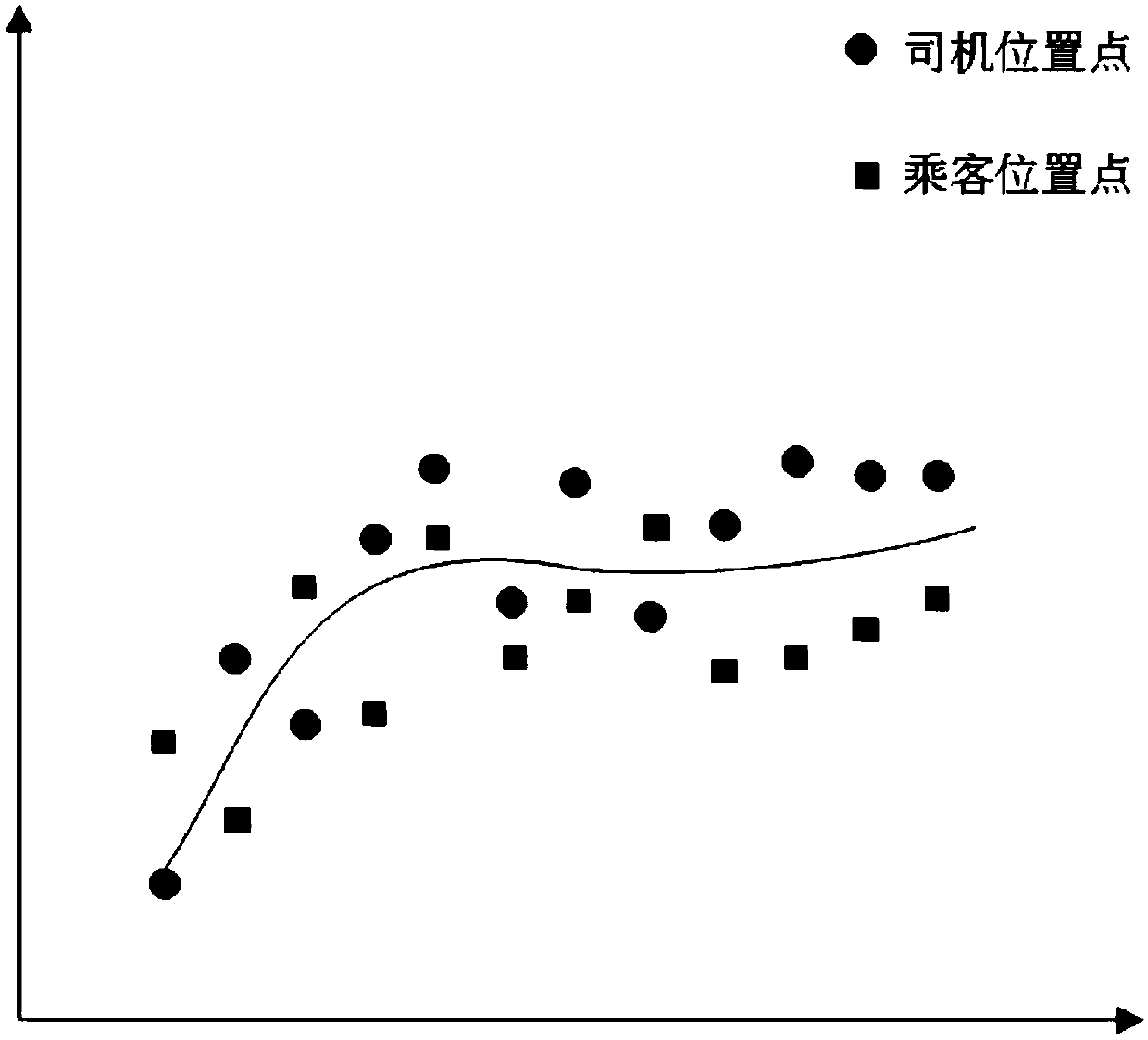
The invention discloses an online car-hailing metering method and a computer readable storage medium, and the method comprises the steps: notifying a driver terminal and a corresponding passenger terminal to start metering after a central server receives a start instruction transmitted by the driver terminal; receiving a first set uploaded by the driver terminal and a second set uploaded by the passenger terminal; respectively replacing the position points in the first set and the second set the positioning mark is no with corresponding path points in the road data; after arriving at the destination, dividing the position points in the first set and the second set where the positioning mark is yes into credible points and uncredible points, and replacing the uncredible points with the corresponding path points in the road data; obtaining a third set according to the replaced first set and second set; and performing calculating to obtain the total mileage according to the third set. According to the invention, the accuracy of online taxi-hailing distance measurement can be improved, so that the accuracy of taxi-hailing cost is improved.
Owner:XIAMEN YAXON NETWORKS CO LTD
Traceable data storage method
ActiveCN110209347AImprove safety and traceabilityReduce the possibility of tamperingInput/output to record carriersDigital data protectionNetwork dataData store
The invention provides a traceable data storage method. The method comprises the following steps: obtaining target data to be stored; cutting the target data into a plurality of sub-data and storing the sub-data in a plurality of storage nodes in a storage network database; and storing the storage information of the target data to each node of the storage network database. Compared with the priorart, the data storage method provided by the invention can effectively improve the security and traceability of data storage.
Owner:TERMINUSBEIJING TECH CO LTD
Digital authentication control medium and digital terminal device having network communication function
InactiveCN103678956AWith security featuresShort transfer timeTransmissionProgram/content distribution protectionTime informationDigital content
A digital authentication control medium comprises: a digital capturing unit for capturing a digital content file; an attribute generating unit for generating terminal information corresponding to the digital content file, wherein the terminal information comprises user information of the digital content file and digital terminal device position identifying information; an encripting unit for generating a file secret key by performing an encripting program to the digital content file; and a data transceiving unit for driving the digital terminal device to transmit the file secret key and the terminal information outwards, and driving the digital terminal device to receive a certification identification code from the outside, wherein the certification identification code is generated by compiling of a certification file, the certification file comprises the file secret key, the terminal information, external time information and external cloud storage information, and content of the certification file in the certification identification code can be read by an external optical reader.
Owner:TEKGLORY BEIJING TECH CO LTD
Privacy protection communication method based on chaotic system, server and communication system
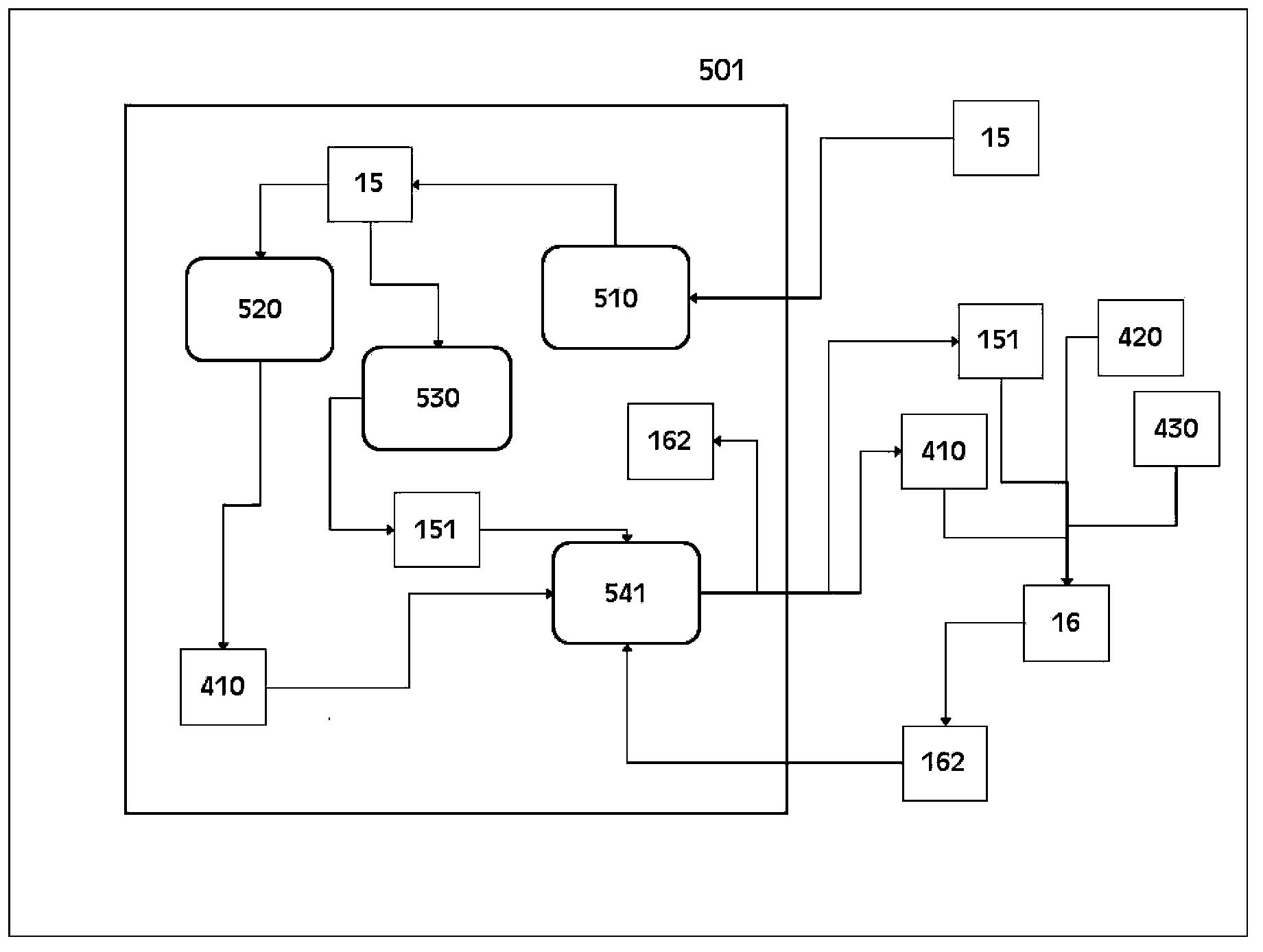
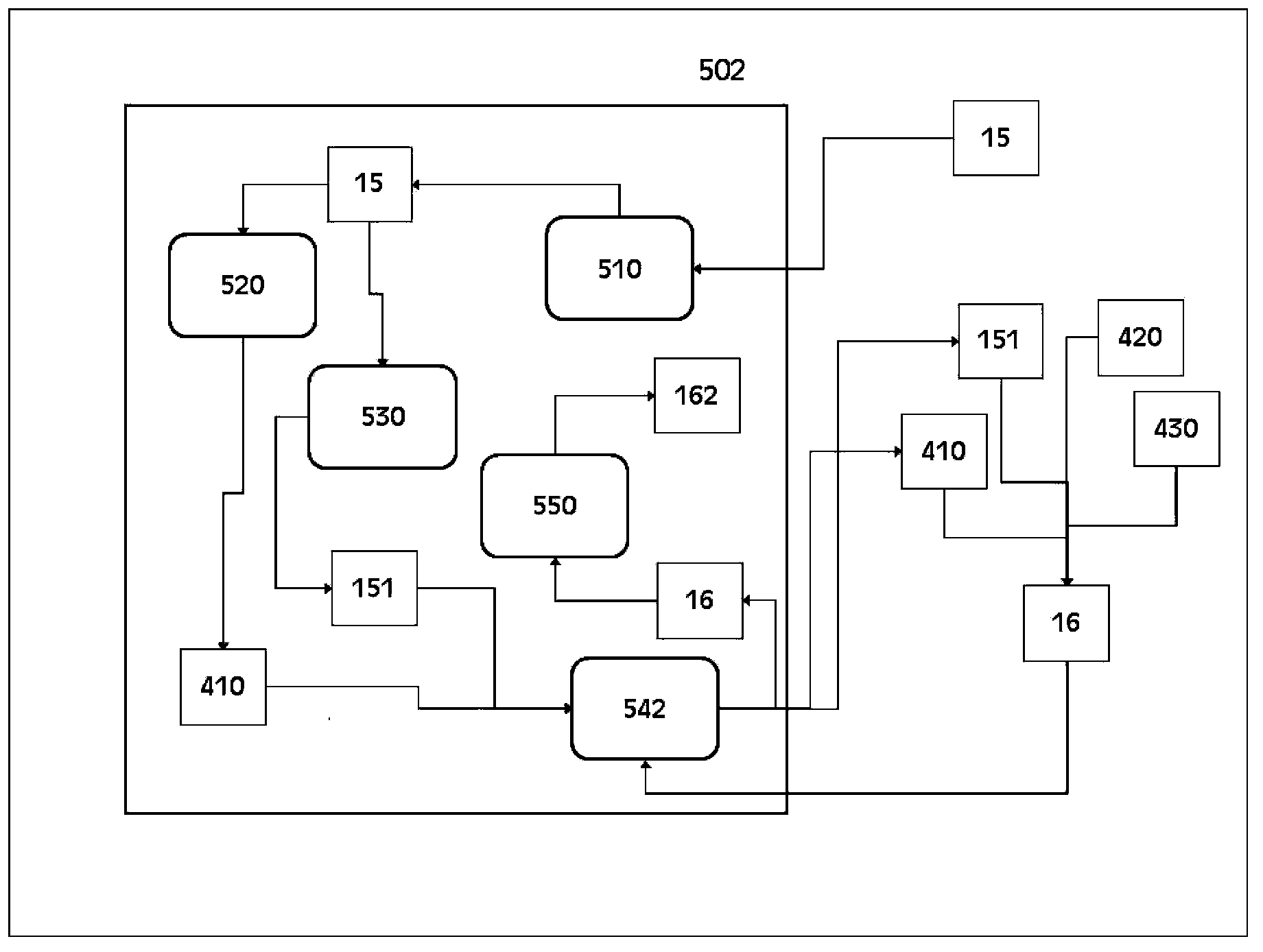
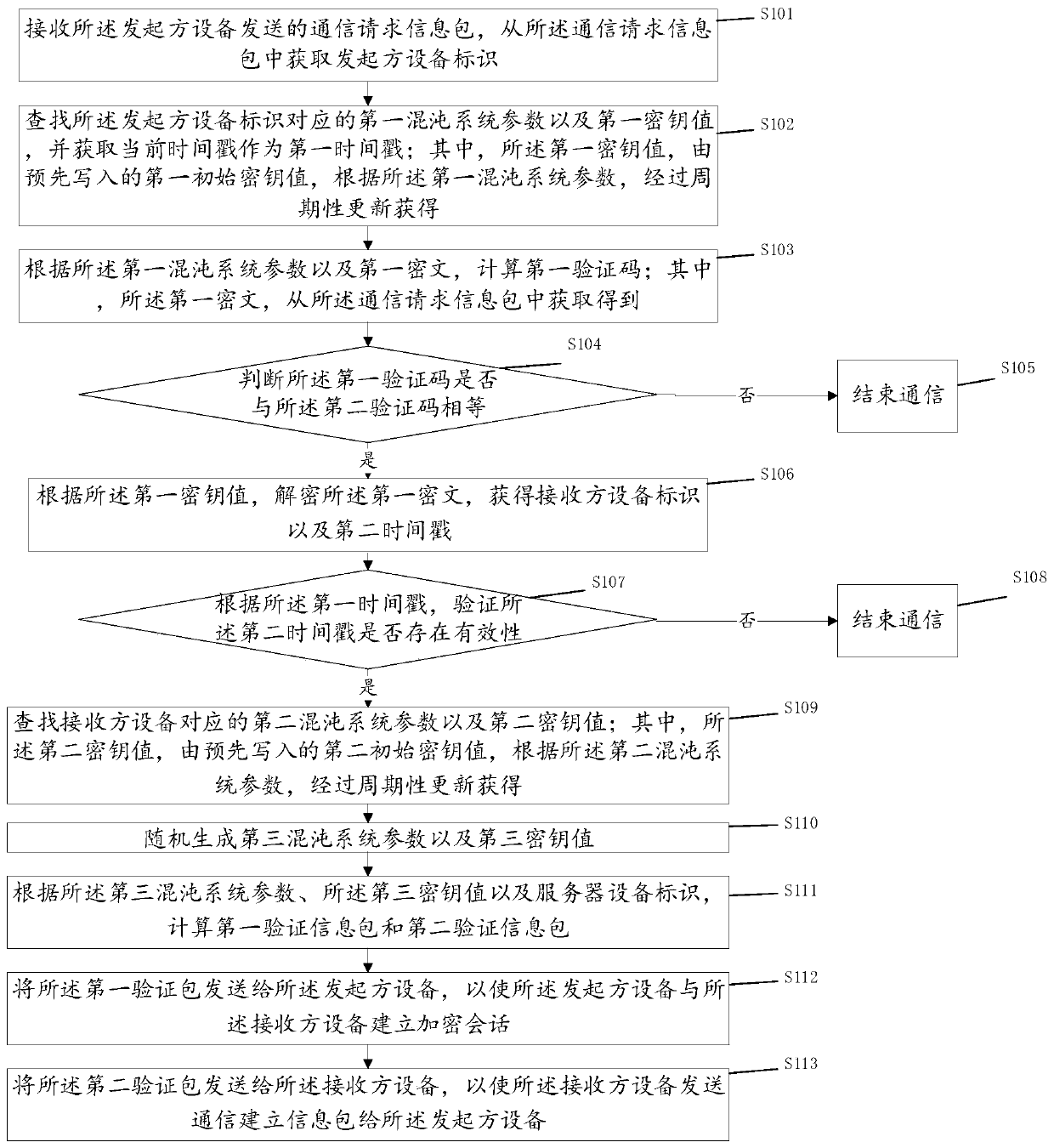
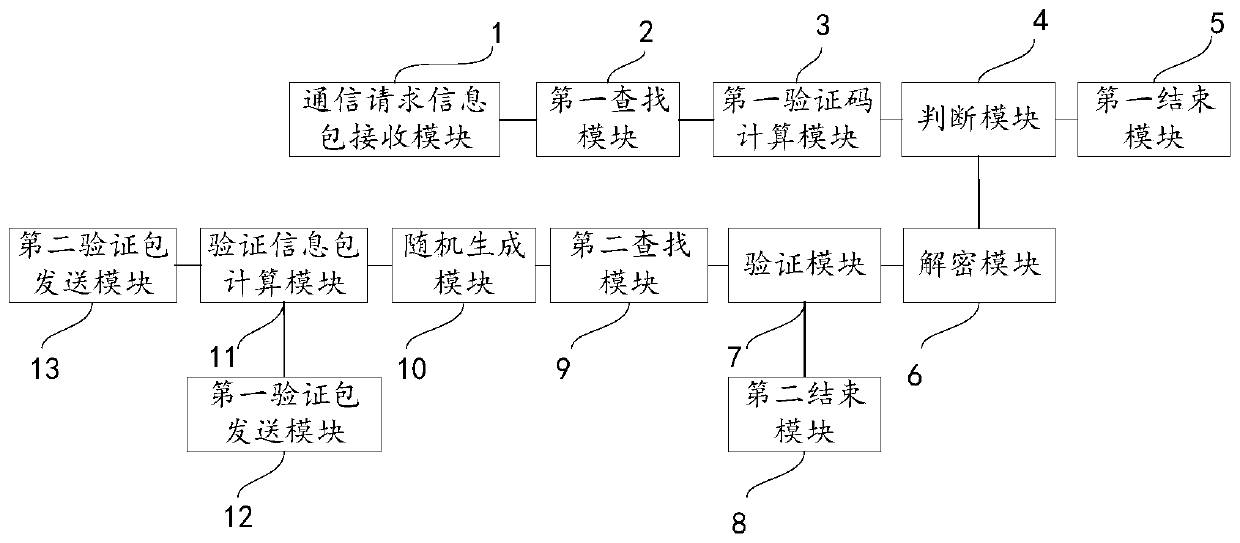
ActiveCN111404659AImprove update efficiencySimple calculationUser identity/authority verificationSecuring communication by chaotic signalsCommunications systemCiphertext
The invention provides a privacy protection communication method based on a chaotic system, a server and a communication system. The method comprises the following steps: receiving a communication request information packet sent by initiator equipment, searching corresponding chaotic system parameters and key values; verifying the verification code in the communication request information packet;after verification is passed, through the searched key value, decrypting the ciphertext in the communication request information packet; obtaining a recipient device identity, searching a chaotic system parameter and a key value corresponding to the receiver equipment; generating a chaotic system parameter and a key value for the session between the initiator device and the receiver device; calculating a first verification information packet and a second verification information packet, and sending the first verification packet to the initiator device to enable the initiator device and the receiver device to establish an encrypted session, and sending the second verification packet to the receiver device to enable the receiver device to send the communication establishment information packet to the initiator device. The method can save the storage space of the communication parameters and protect the privacy security of the user.
Owner:GUANGZHOU UNIVERSITY +1
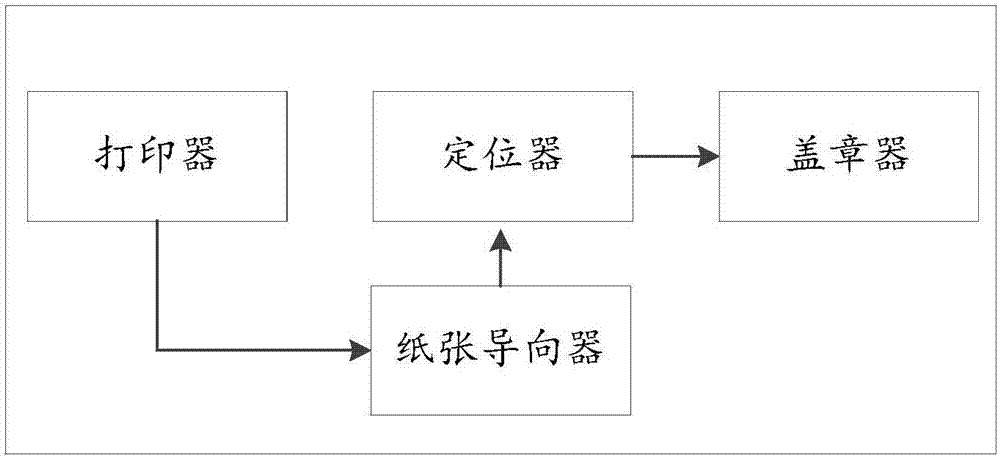
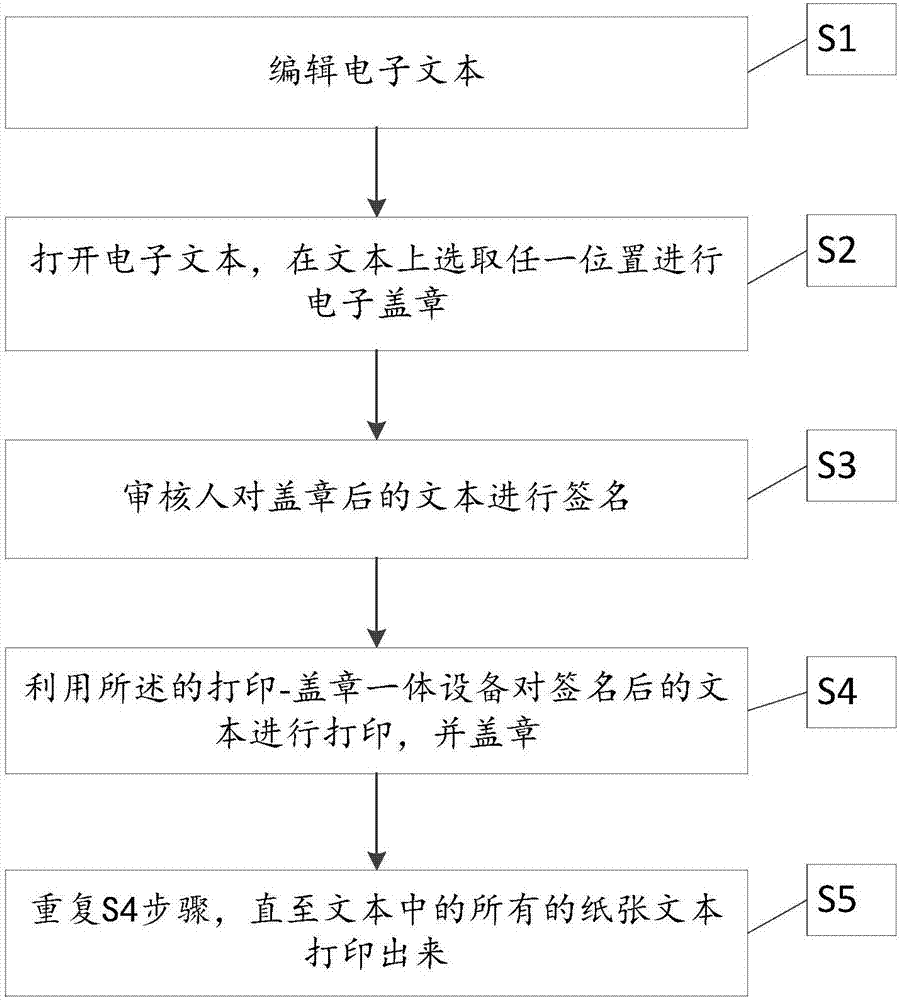
Printing-stamping integrated device and printed text stamping method
InactiveCN107169369AEasy to distinguishIncreased difficulty of being tampered withDigital data protectionDocument preparationIntegrated devices
The invention relates to a printing-stamping integrated device. The device comprises a printer, a locator and a stamper which are sealed in a box body, wherein the locator is used for determining a stamping position; and the stamper is used for stamping. The invention furthermore relates to a method. The stamping method comprises the steps of editing an electronic text; selecting any position on the text to perform electronic stamping; performing signature on the stamped text; printing and stamping the signed text; and repeating the step S4 until all paper texts in the text are printed out. Through the device and the method, a document of a contract is confirmed through a key technology and a physical sealing action, and the stamper is ensured to only stamp the paper document of the contract; and after text contents and the stamping position are audited and determined, the document is signed by a private key, so that the text cannot be tampered.
Owner:胡金钱
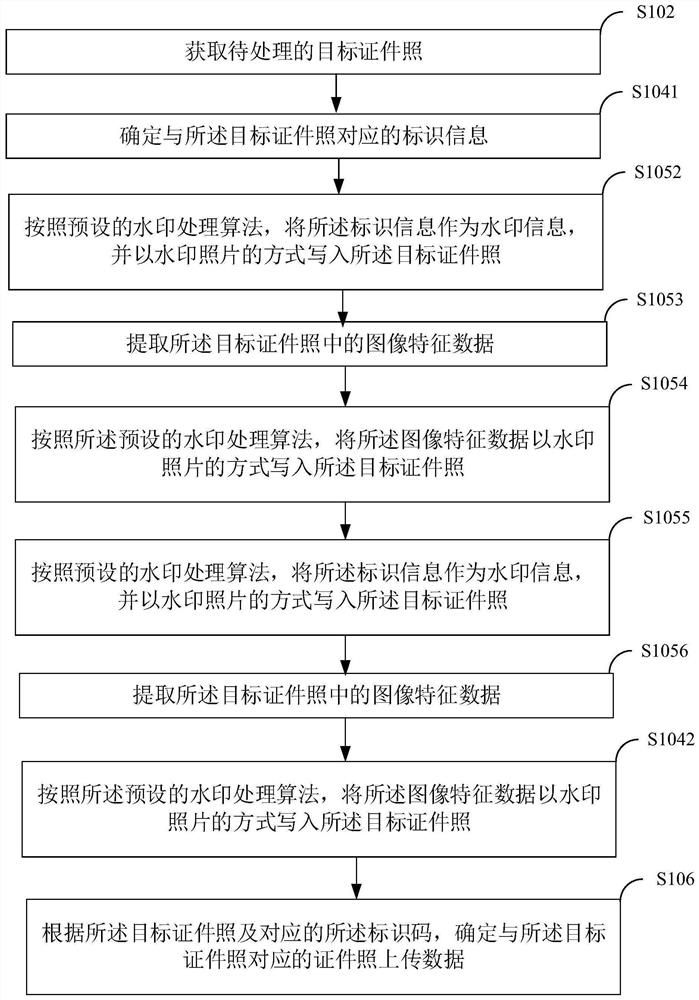
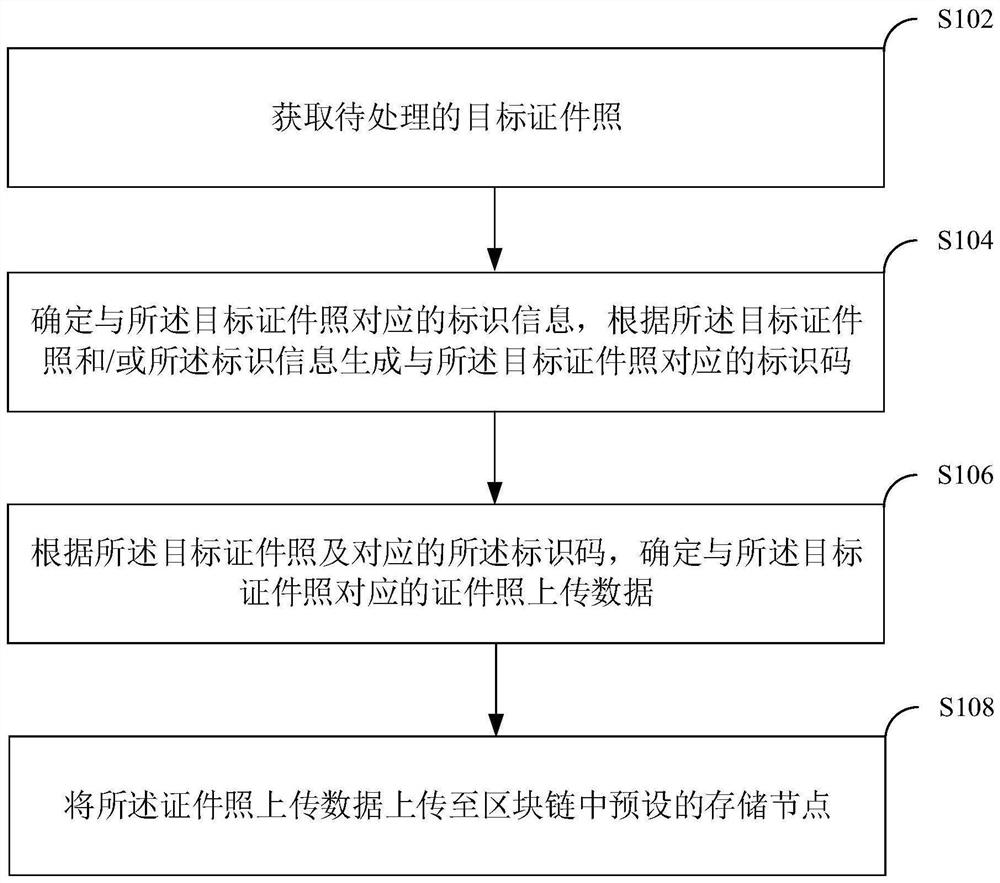
Identification photo management method and device based on block chain, equipment and readable medium
ActiveCN112003888AImprove securityReduce the possibility of tamperingTransmissionComputer hardwarePhoto management
The embodiment of the invention discloses an identification photo management method and device based on a block chain, computer equipment and a computer readable storage medium. The method comprises the steps of obtaining a to-be-processed target identification photo; determining identification information corresponding to the target identification photo, and generating an identification code corresponding to the target identification photo according to the target identification photo and / or the identification information; and determining identification photo uploading data corresponding to the target identification photo according to the target identification photo and the corresponding identification code, and uploading the identification photo uploading data to a preset storage node inthe block chain. According to the invention, the security of identification photo management can be improved.
Owner:SHENZHEN EMPEROR TECH
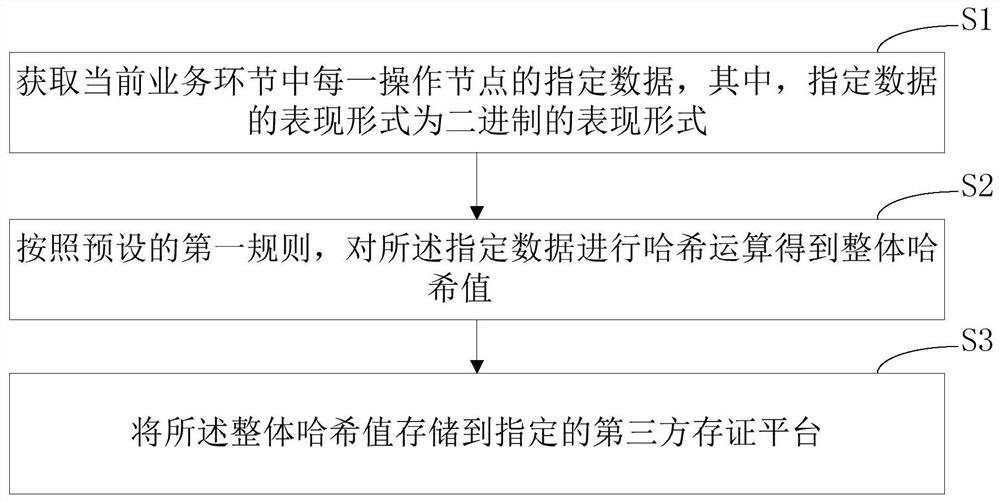
Evidence storage method and device, computer equipment and storage medium
PendingCN111767579AReduce difficultyReduce the possibility of tamperingData processing applicationsVideo data clustering/classificationThird partyData class
The invention discloses an evidence storage method and device, computer equipment and a storage medium, and the evidence storage method comprises the steps: obtaining the specified data of each operation node in a current business link, wherein the representation form of the specified data is a binary representation form; according to a preset first rule, performing hash operation on the specifieddata to obtain an overall hash value; and storing the overall hash value to a specified third-party evidence storage platform. Through the principle that hash calculation is irreversible, the evidence storage method converts the evidence storage data into hash values and stores the hash values on a third-party evidence storage platform, so that no matter what data type of the evidence storage data is, the data type can be converted into the hash value to be uniformly stored; the storage difficulty of different types of evidences is reduced, and the possibility of enterprise user data tampering is reduced; and meanwhile, the generated hash value shields the original data content, and the safety of enterprise data is ensured, and the problems of enterprise data leakage and the like are avoided.
Owner:PINGAN PUHUI ENTERPRISE MANAGEMENT CO LTD
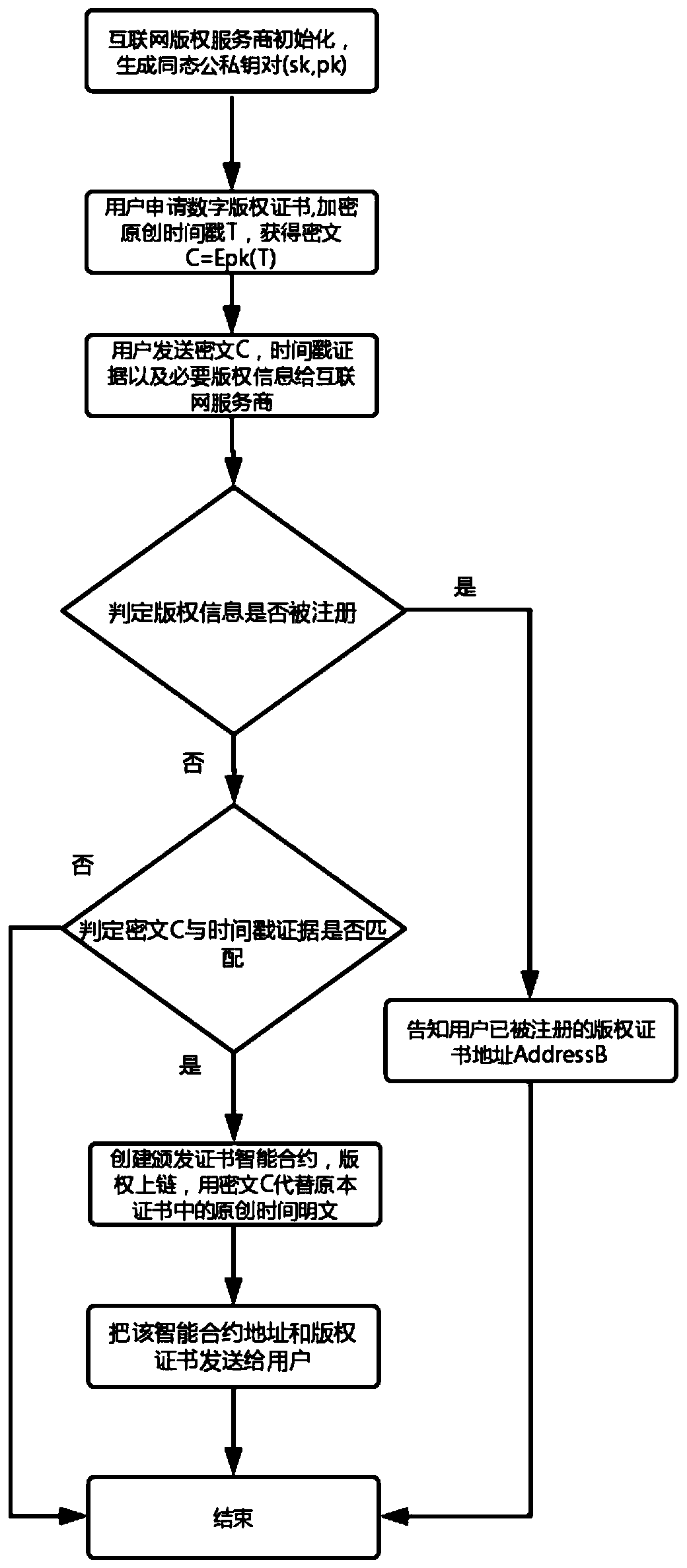
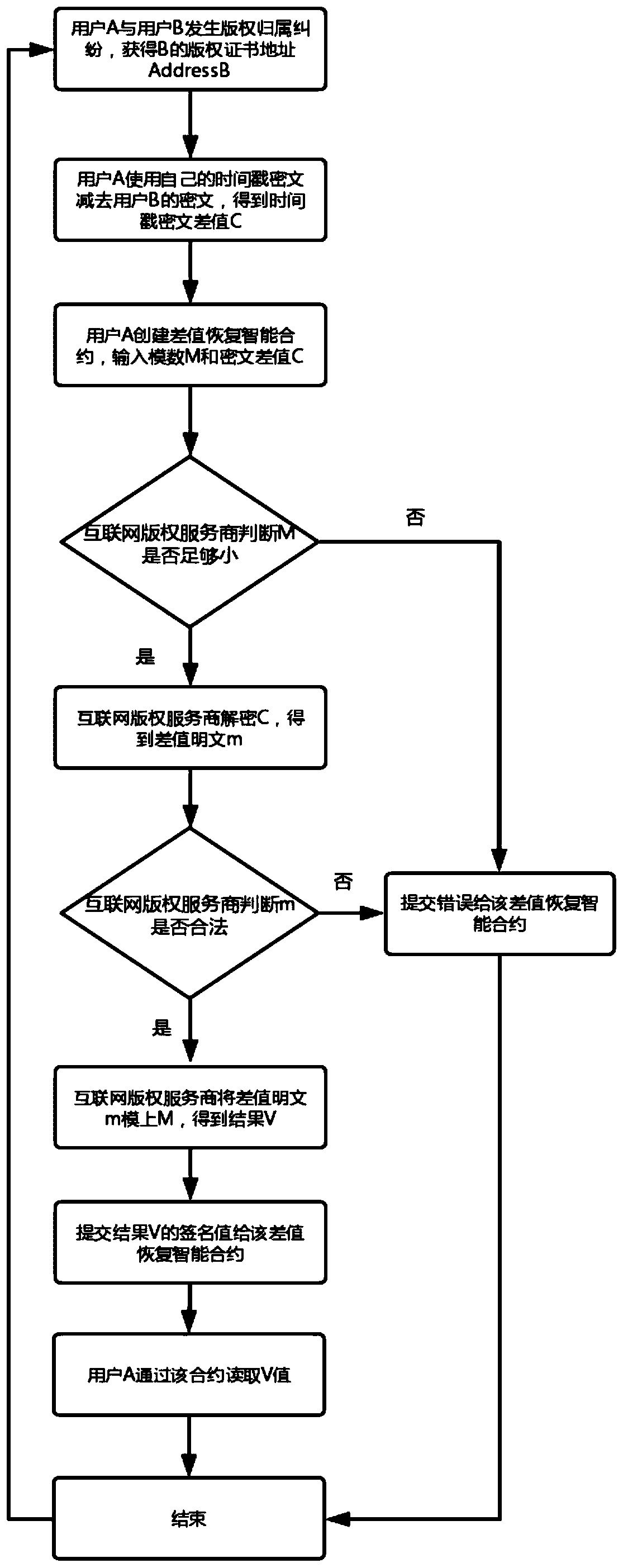
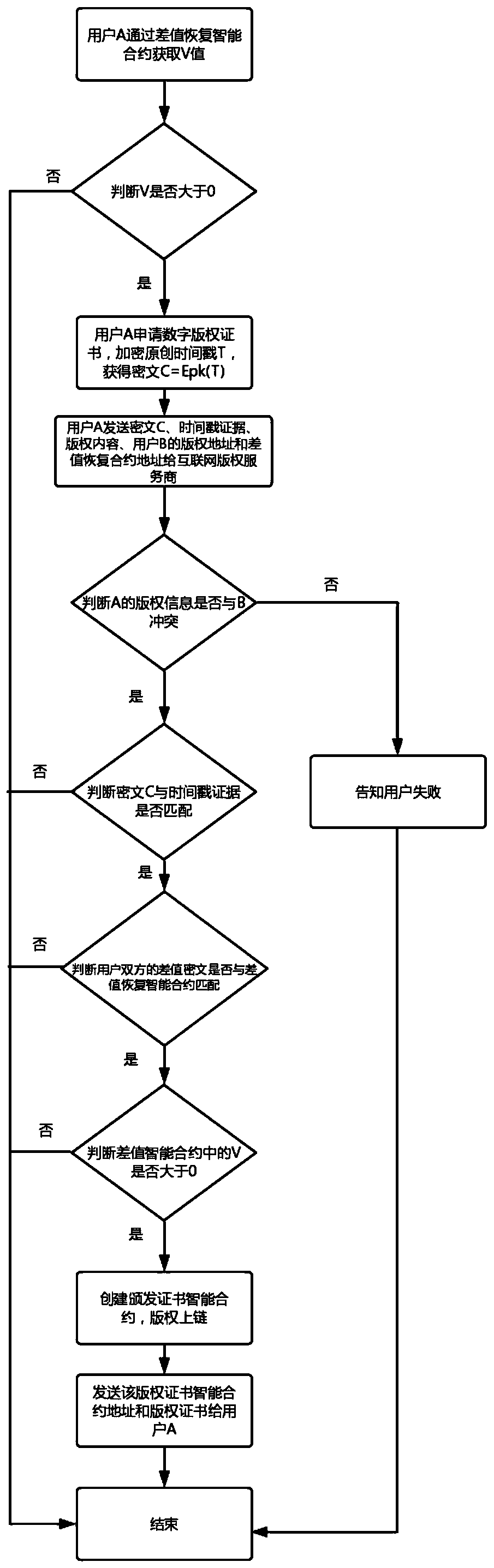
Blockchain digital rights protection method and system based on prior inventive principle
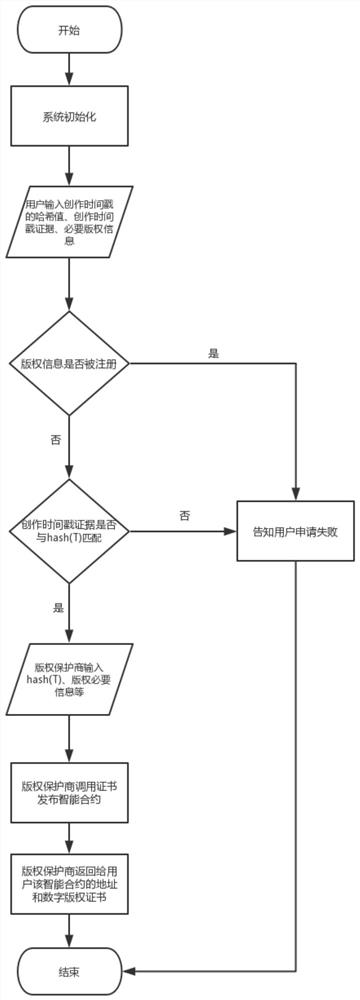
ActiveCN110659453ARealize the function of privacy protectionSolve the privacy protection problem of authoring timestampProgram/content distribution protectionTimestampCiphertext
The invention discloses a blockchain digital rights protection method and system based on prior inventive principle. The method comprises the following steps: 1) when a user applies for a digital copyright certificate from a blockchain for a finished work, a creation timestamp of the work is encrypted by using a homomorphic public key of an Internet copyright service party to obtain a creation timestamp ciphertext, and sending the creation timestamp ciphertext to the Internet copyright service party; 2) the Internet copyright service party compares the creation timestamp ciphertext with creation time evidence provided by the user, if the creation time ciphertext is matched with the creation time evidence and the copyright content of the work is not registered, a certificate issuing smart contract is created, and the address of the smart contract is sent to the user; and 3) the Internet copyright service party stores the creation timestamp ciphertext in a copyright certificate and uplinks the copyright certificate, so that the problem that an original author cannot submit a digital copyright application in time due to high fluidity of original content on the network at present is solved.
Owner:INST OF INFORMATION ENG CAS +1
Detection device, air detection device, control system and control method
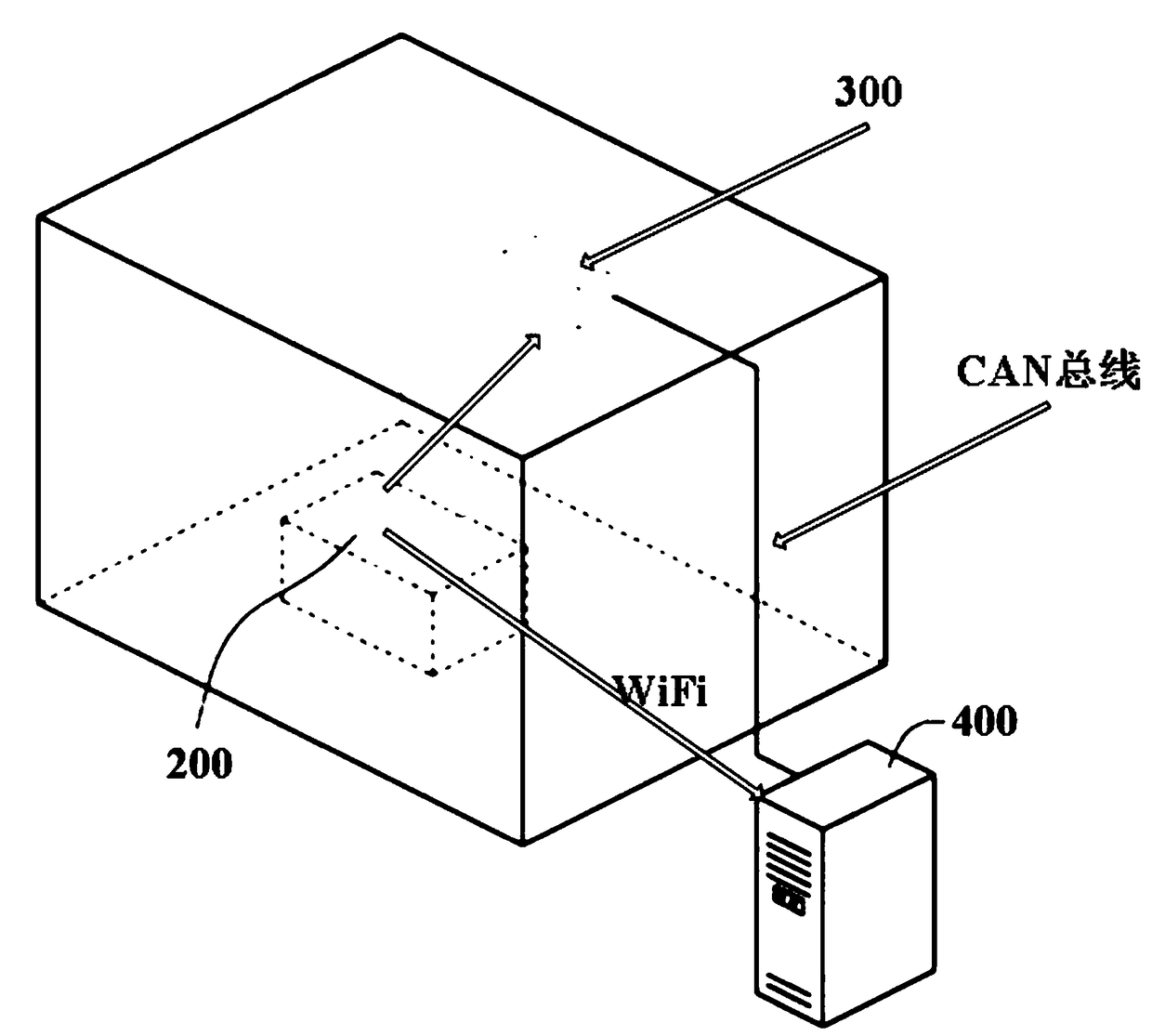
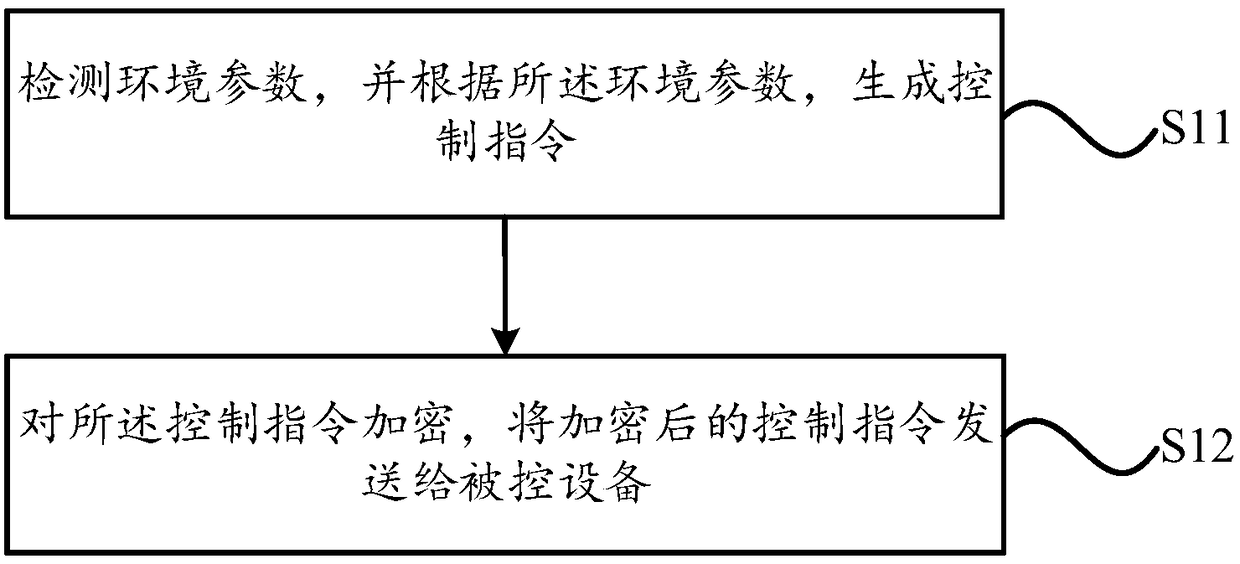
InactiveCN109218328AReduce hijackingReduce the possibility of tamperingKey distribution for secure communicationMeasurement devicesControl systemComputer module
The invention relates to a detection device, an air detection device, a control method and a control system. A processing module, configured to generate a control instruction according to the environmental parameter; an encryption module, configured to encrypt the control instruction; the sending module is used for sending the encrypted control instruction to the controlled equipment. According tothe technical proposal provided by the invention, the device detects an environmental parameter, Simultaneous generation of control instructions, the control instruction can also be encrypted, The encrypted control instruction is sent to the controlled equipment. Because the control instruction is encrypted, the possibility that the control instruction is captured and tampered with by illegal elements is reduced, and the safe transmission of the control instruction is realized. At the same time, the accurate control instruction can be received by the controlled equipment, which greatly improves the safety and reliability of the system.
Owner:GREE ELECTRIC APPLIANCES INC
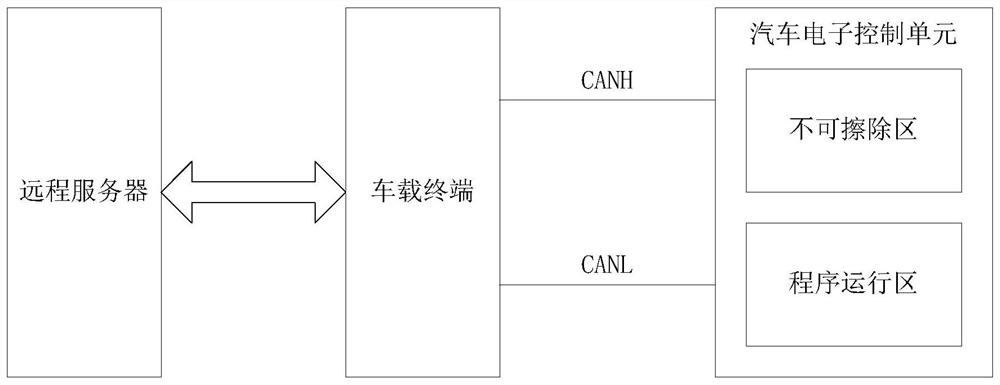
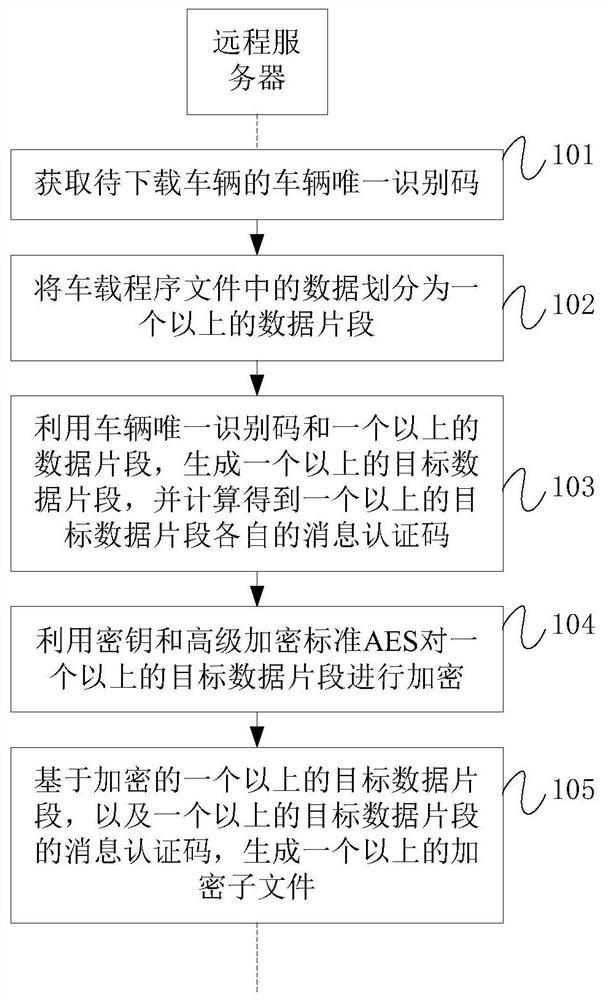
Vehicle-mounted program file encryption method and device
ActiveCN108337234AImprove securityReduce the possibility of tamperingKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwareAdvanced Encryption Standard
The invention provides a vehicle-mounted program file encryption method and device, related to the field of electronic and electrical. The vehicle-mounted program file encryption method comprises thefollowing steps: dividing the data in the vehicle-mounted program file into more than one data fragment; obtaining message authentication codes of the more than one data fragment according to the morethan one data fragment; using a key and the advanced encryption standard AES to encrypt the more than one data fragment; generating more than one encrypted sub-file based on the more than one encrypted data fragment and the message authentication codes of the more than one data fragment, wherein each encrypted sub-file includes one encrypted data fragment and the message authentication code of one data fragment; and combining the more than one encrypted sub-file to obtain the encrypted vehicle-mounted program file according to the more than one encrypted sub-file. The vehicle-mounted programfile encryption method and device provided by the embodiment of the invention can improve the security of vehicle control.
Owner:컨템포러리엠퍼렉스테크놀로지씨오리미티드
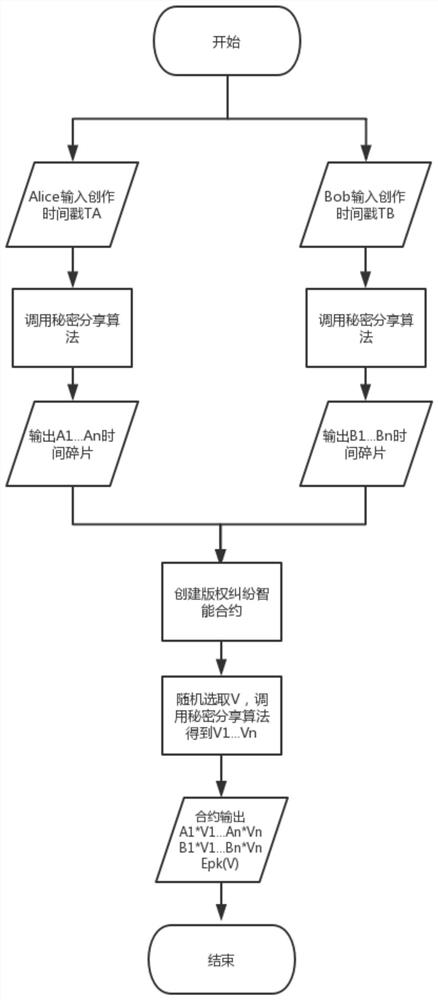
A digital copyright method and system based on secure multi-party computing privacy time stamp
ActiveCN110532734BSolve the problem of privacy protectionGuaranteed anonymityDigital data protectionProgram/content distribution protectionShardPrivacy protection
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI +1
TEE-based federal recommendation method, apparatus and device, and medium
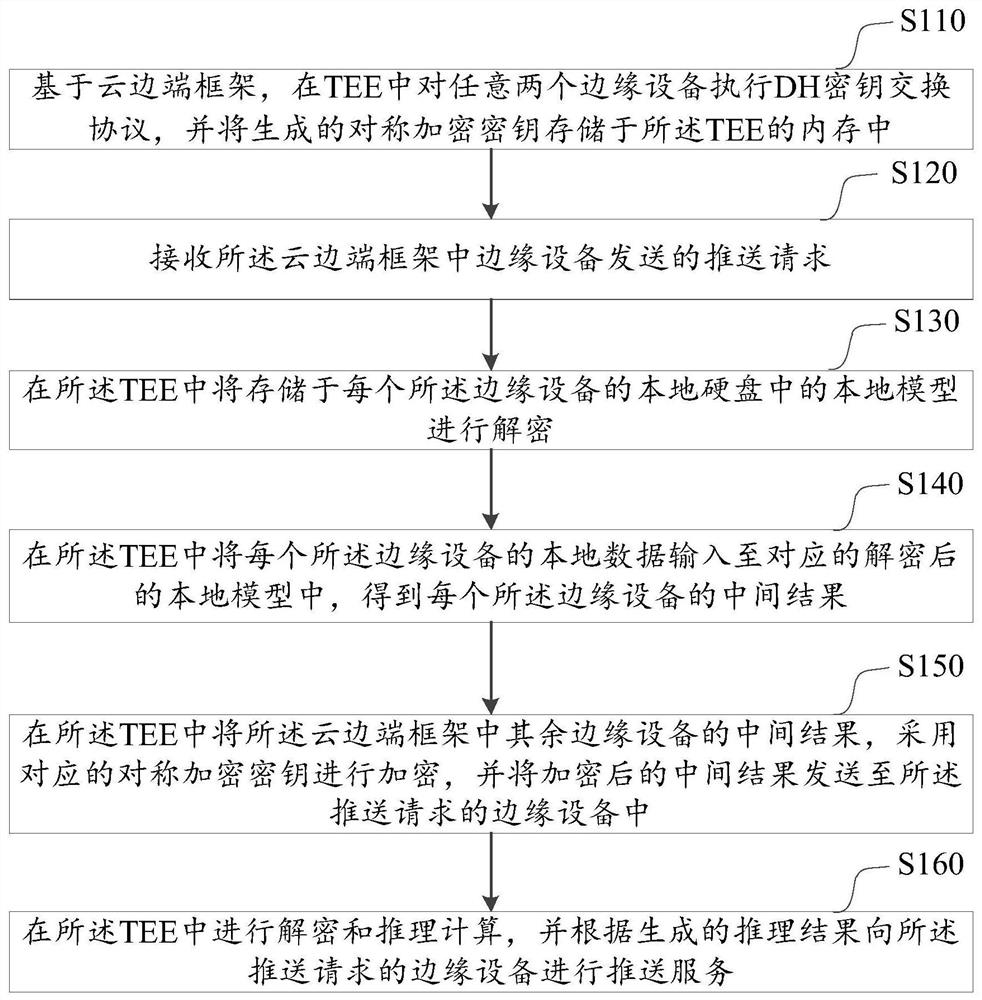
ActiveCN113259100AReduce the possibility of tamperingPrevent leakageKey distribution for secure communicationEnsemble learningEmbedded systemProtocol for Carrying Authentication for Network Access
The embodiment of the invention discloses a TEE-based federal recommendation method, apparatus and device, and a medium. The method comprises the steps of executing a DH key exchange protocol on any two edge devices based on a cloud edge frame, and storing a generated symmetric encryption key in a memory of a TEE; receiving a push request sent by the edge device; decrypting the local model stored in the local hard disk of each edge device in the TEE; and inputting local data of each edge device into the corresponding decrypted local model in the TEE, encrypting a generated intermediate result by using the corresponding symmetric encryption key, and sending the encrypted intermediate result to the edge device corresponding to the push request for decryption and reasoning calculation so as to perform push service. The invention further relates to a block chain technology, and the push request is stored in a block chain. Based on the digital signature technology, the DH protocol is executed in the TEE and encryption and processing of the data in the cloud edge end frame are performed, so that the possibility that the data is tampered in the federated reasoning process is avoided.
Owner:PING AN TECH (SHENZHEN) CO LTD
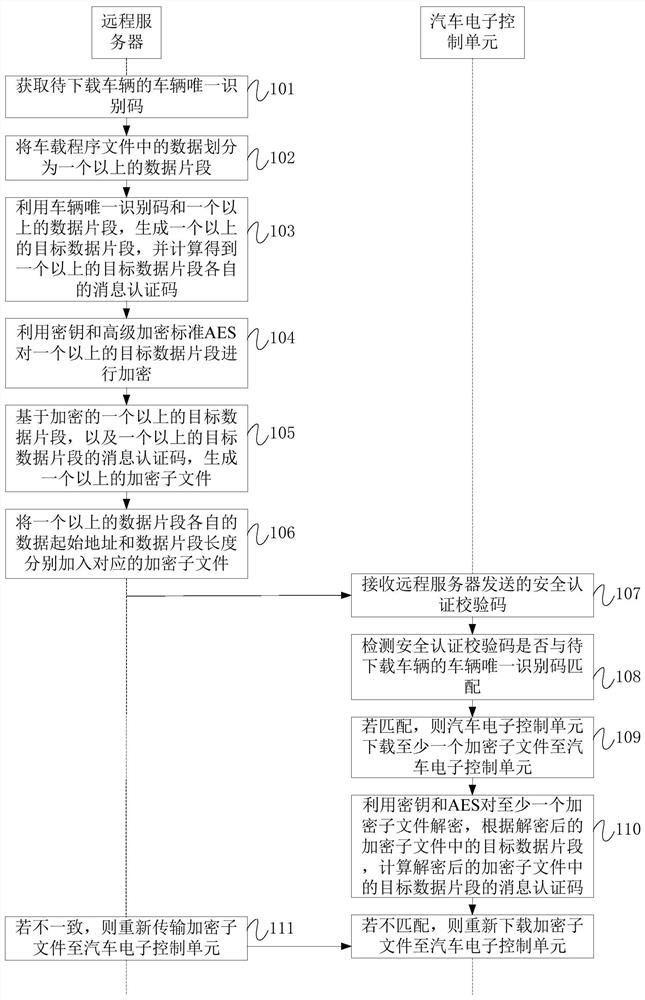
Vehicle program file encryption method and system
ActiveCN108200044BIncrease the difficulty of crackingReduce the possibility of tamperingKey distribution for secure communicationEncryption apparatus with shift registers/memoriesData segmentIn vehicle
The invention provides a vehicle-mounted program file encryption method and system, which relate to the technical field of electronics and electrics. The vehicle program file encryption method includes: the remote server obtains the vehicle unique identification code of the vehicle to be downloaded; divides the data in the vehicle program file into more than one data segment; uses the vehicle unique identification code and more than one data segment to generate more than one target data segments, and calculate the respective message authentication codes of more than one target data segment, at least one target data segment includes a vehicle unique identification code; use a key and Advanced Encryption Standard AES to encrypt more than one target data segment; Based on the encrypted one or more target data segments and the message authentication codes of the one or more target data segments, one or more encrypted sub-files are generated. Utilizing the technical scheme of the invention can improve the safety of automobile control.
Owner:CONTEMPORARY AMPEREX RUNZHI SOFTWARE TECH LTD NINGDE CITY
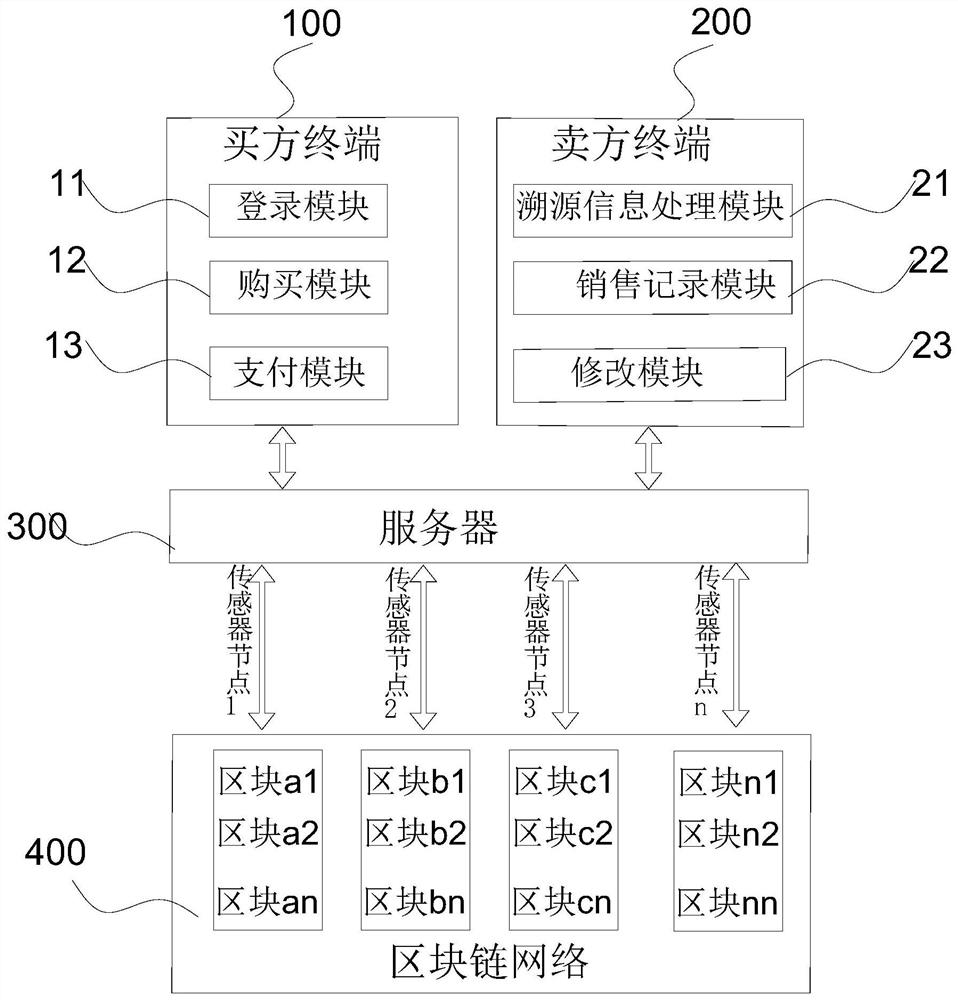
Food mall safety operation and maintenance system
PendingCN112132297AReduce lossReduce tamperingFinancePayment architectureTerminal serverFinancial transaction
The invention discloses a food mall safety operation and maintenance system comprising a buyer terminal, a seller terminal, a server and a block chain network, the buyer terminal and the seller terminal are both connected to the server and are in bidirectional communication connection with the server, and the buyer terminal comprises a login module, a purchase module and a payment module; the seller terminal comprises a traceability information processing module, a sales recording module and a modification module, wherein the server is used for receiving and processing data sent by the buyer terminal and the seller terminal and storing the data into the blockchain network, the blockchain network and the server are in two-way communication through the sensor node, and the blockchain networkis used for verifying, storing and outputting the server data. Tamper resistance of the blockchain network is utilized to realize food safety traceability and accurate recording of transaction, and safety and stability of the whole operation and maintenance system are ensured.
Owner:SUZHOU BAMMIT INFORMATION TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com