Modular computer forensic system and method based on hardware virtualization
A hardware virtualization and computer forensics technology, applied in hardware monitoring, software emulation/interpretation/simulation, program control devices, etc., it can solve the problem that the intrusion behavior cannot be reconstructed, the image cannot be guaranteed to contain the intrusion evidence, and it is time-consuming and difficult to implement. And other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0073] The present invention will be further described below in conjunction with the accompanying drawings.
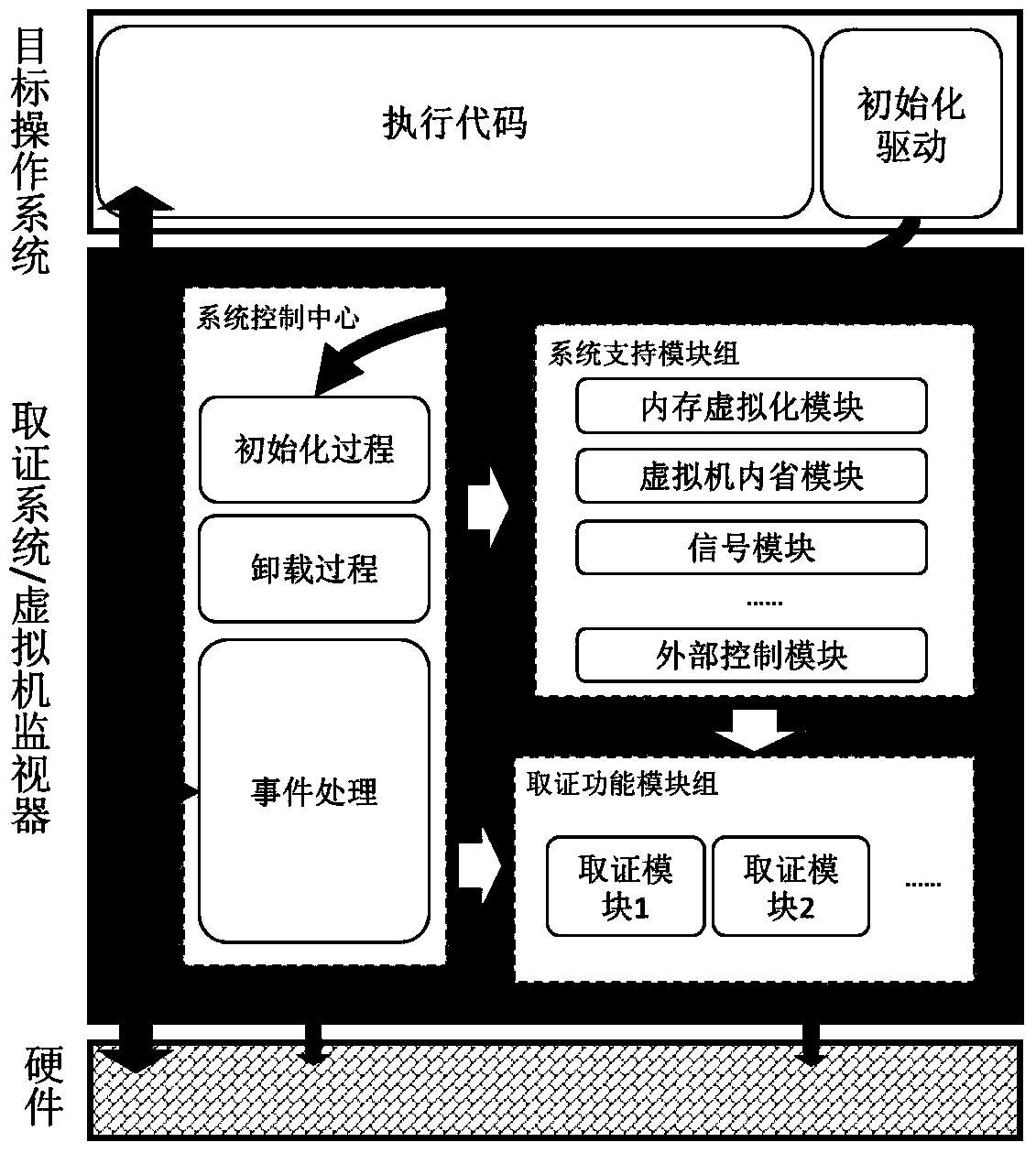
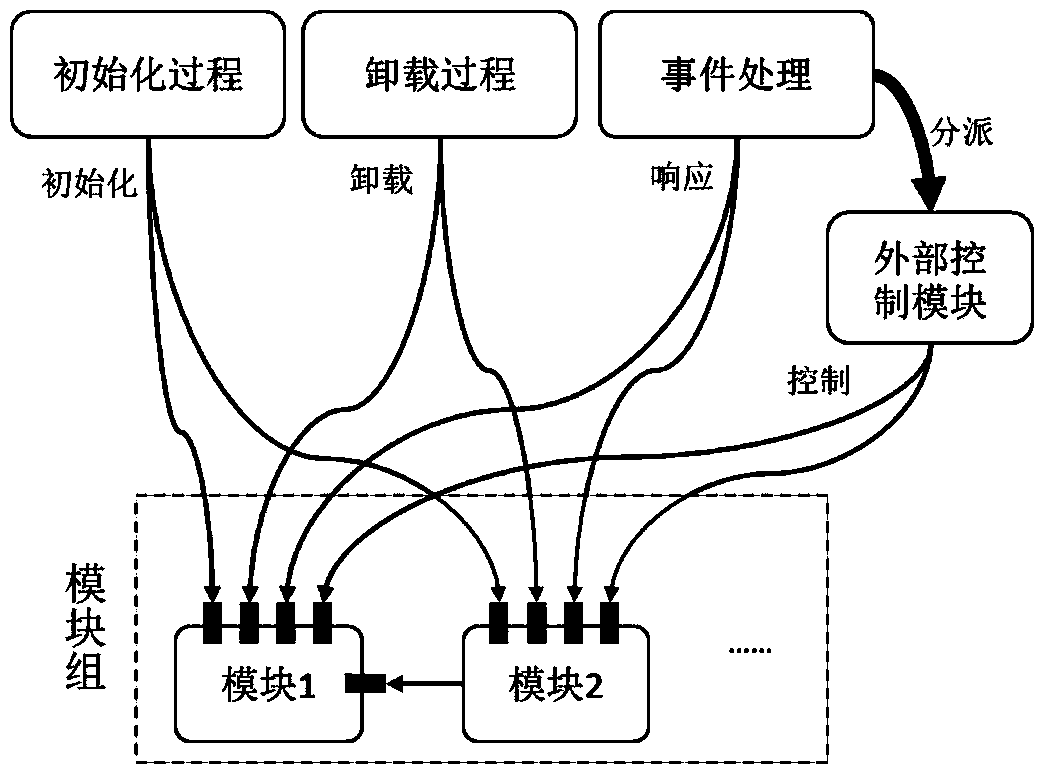
[0074] The detailed operation process of this method is as follows: Figure 1-Figure 5 shown.
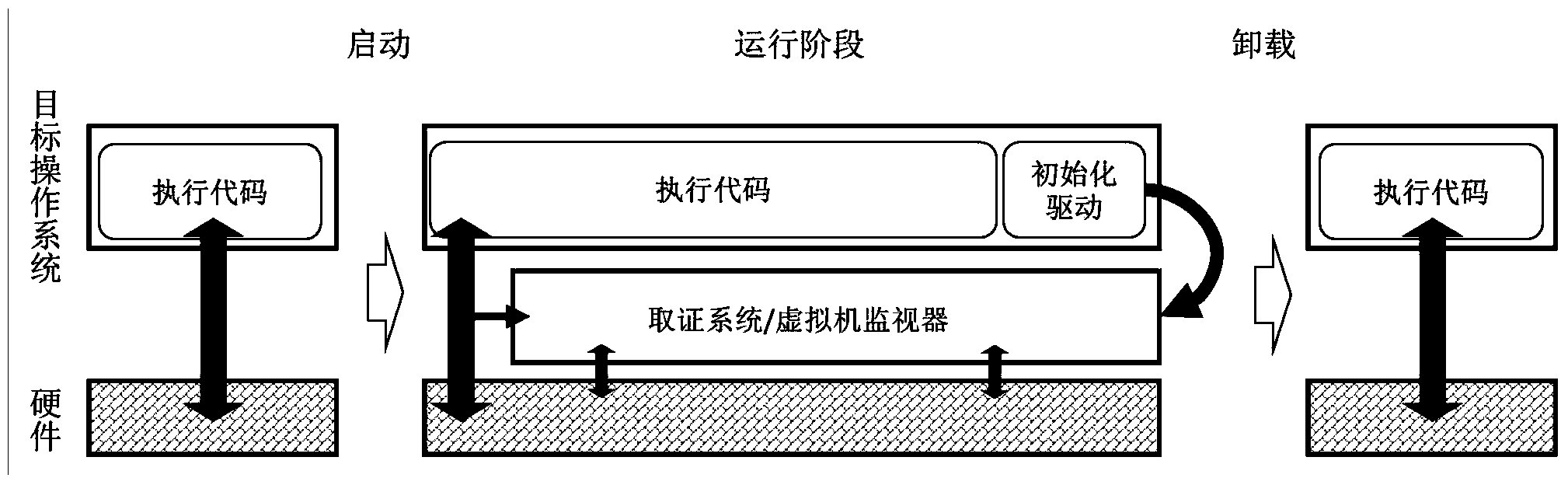
[0075] figure 1 Shown are the three life cycles of this method, including the startup phase, the running phase and the unloading phase. The initialization driver is used to deploy and uninstall the Forensics Platform in a running operating system.
[0076] This embodiment adopts the Intel VT technology, obtains the kernel authority of the operating system by initializing the driver at startup, calls the memory allocation function to allocate enough space for the operation of the virtual machine, and configures the VMCS structure to set the entire virtual machine. Then copy the running state of the current operating system to the Guest-State Area, and configure the event processing function of the forensics platform, each descriptor table, stack and registers in the Host-S...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com