SQL injection prevention method, device and system
An injection time, syntax tree technology, applied in the computer field, can solve problems such as lack of learning flow, difficulty, wrong learning, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0099] Such as Figure 4 As shown, taking the client web client to embed semantic information into SQL statements, and the database server to complete the detection of SQL injection as an example, the method for defending against SQL injection in the embodiment of the present invention will be described in detail. The method includes step 401 - step 411:
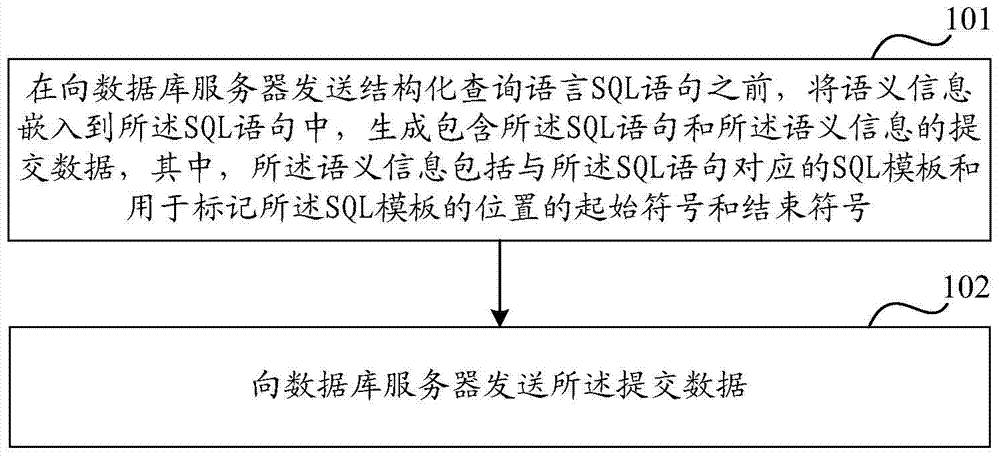
[0100] Step 401: Before sending the SQL statement, the Web client embeds the semantic information into the SQL statement to generate submission data including the SQL statement and the semantic information, wherein the semantic information includes an SQL template corresponding to the SQL statement and are used to mark the start and end symbols of the SQL template.
[0101] Step 402: the web client sends the submitted data to the database server.
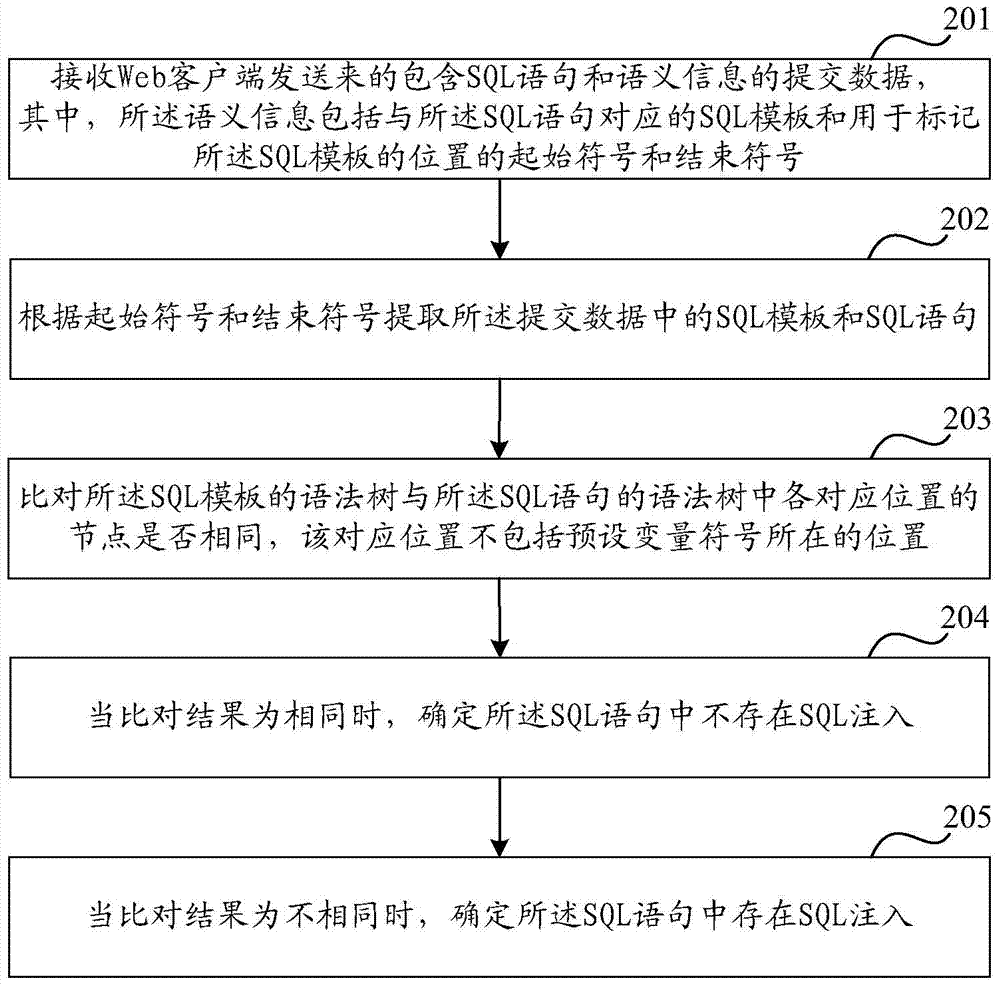
[0102] Step 403: the database server receives the submission data sent by the web client.
[0103] Step 404: The database server judges whether the submitted data includes the ...
Embodiment 2
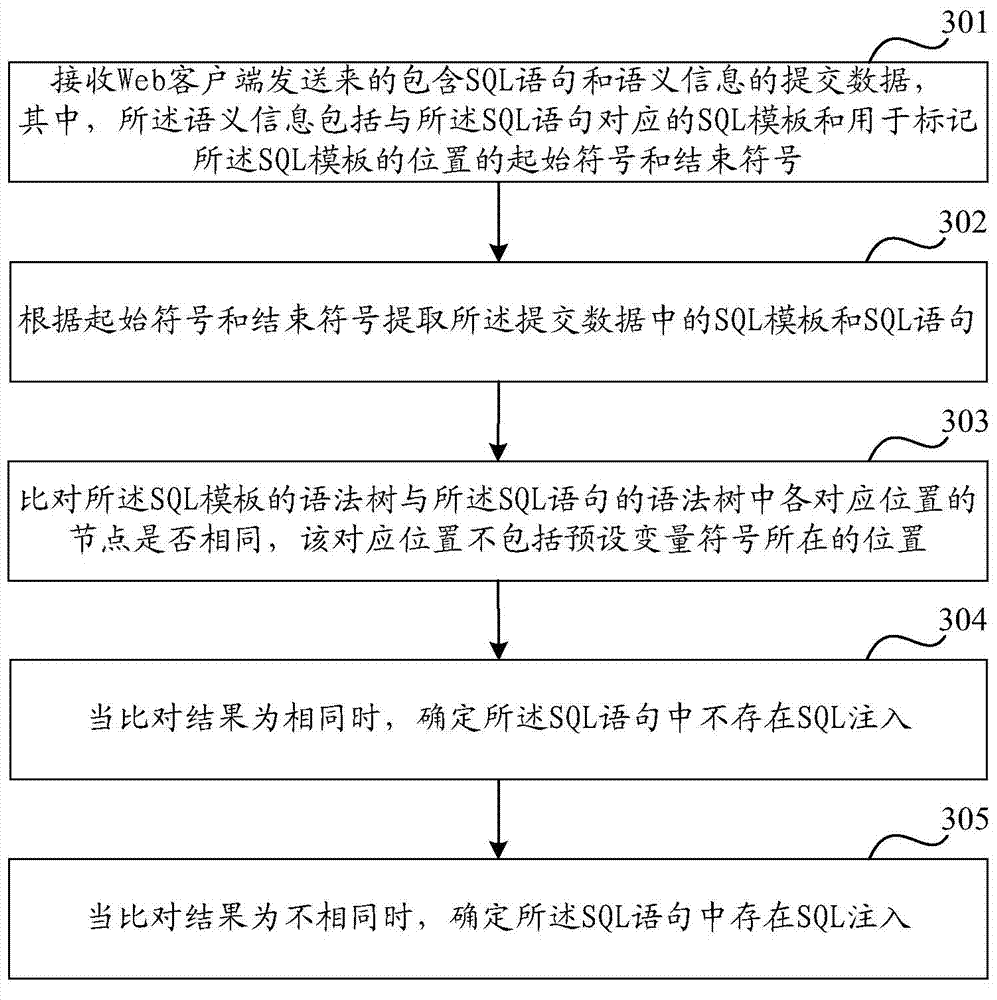
[0114] Such as Figure 5 As shown, taking the detection of user login statements that do not include SQL injection as an example, the method for defending against SQL injection in the embodiment of the present invention will be described in detail. The method includes steps 501-step 508:
[0115] Step 501: The web client receives the data input by the user, wherein the user name is admin, and the password is 123456.
[0116] Among them, the source code snippet of the SQL statement generated by the Web client:
[0117] "SELECT*FROM users WHERE user='"+name+"'AND passwd='"+pass+"'"
[0118] The SQL template corresponding to the SQL statement generated by this source code fragment is:
[0119] SELECT * FROM users WHERE name=$ AND passwd=$
[0120] Step 502: the Web client generates submitted data including SQL statements and semantic information.
[0121] Among them, the submitted data is:
[0122] [SELECT*FROM users WHERE name=$AND passwd=$]SELECT*FROM users WHERE name='adm...
Embodiment 3
[0133] Such as Figure 8 As shown, taking the detection of a user login statement including SQL injection as an example, the method for defending against SQL injection in the embodiment of the present invention will be described in detail. The method includes steps 801-808:
[0134] Step 801: The web client receives the data input by the user, wherein the user name is admin, and the password password is 'or1='1.
[0135] Among them, the source code fragment of the SQL statement generated by the Web client is:
[0136] "SELECT*FROM users WHERE user='"+name+"'AND passwd='"+pass+"'"
[0137] The SQL template corresponding to the SQL statement generated by the source code fragment is:
[0138] SELECT * FROM users WHERE name=$ AND passwd=$
[0139] Step 802: the Web client generates submitted data including SQL statements and semantic information.
[0140] Among them, the submitted data is:
[0141] [SELECT*FROM users WHERE name=$AND passwd=$]SELECT*FROM users WHERE name='admi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com