Unattended security protection system of transformer substation
A technology for security systems and substations, applied to instruments, individual input/output port registers, time registers, etc., can solve the problems of employee ID or ID card being easily stolen, poor flexibility, power supply failure, etc., to achieve Save labor costs and resources, and use flexible effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
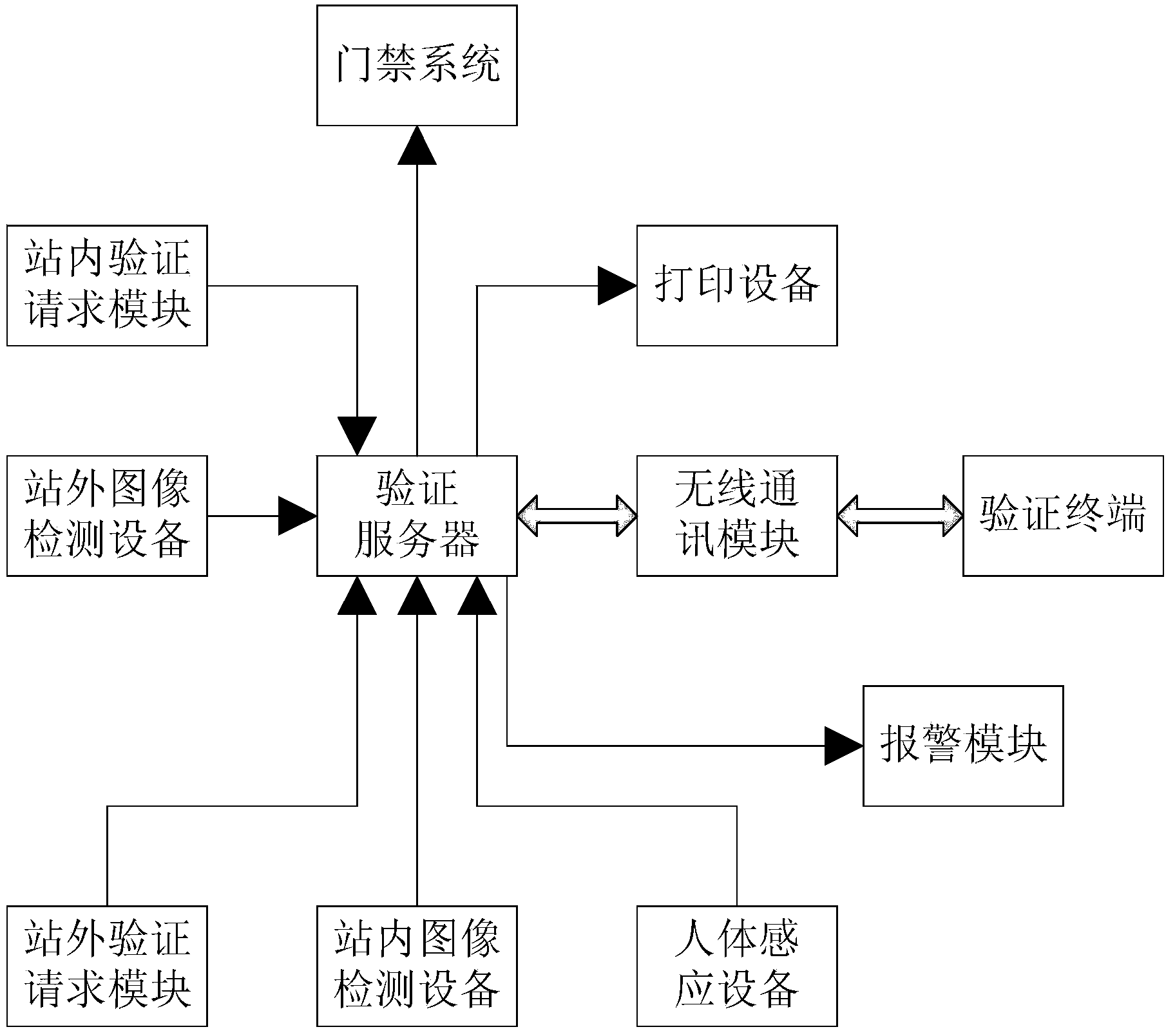
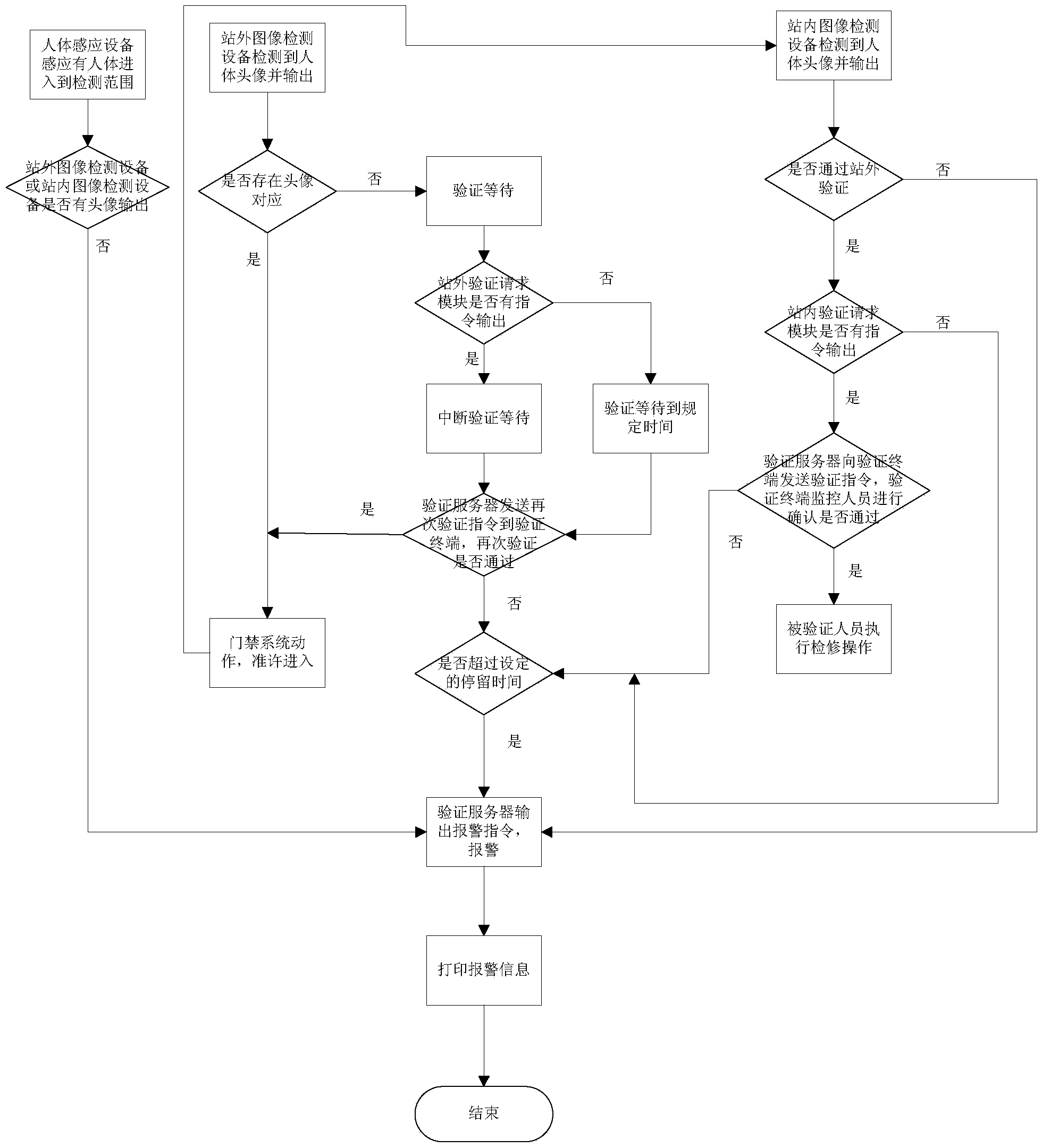
[0028] figure 1 It is a block diagram of the present invention, figure 2 It is the work flow diagram of the present invention, as shown in the figure, a substation unattended security system provided by the present invention includes at least an access control system, and also includes:
[0029] The image detection equipment outside the station is set outside the entrance of the substation to obtain and output the head portrait information of the human body within the detection range. The image detection equipment outside the station uses a camera to obtain the head portrait information of the person entering the detection range. facial information;
[0030] The verification server is used to receive and process the human head portrait information output by the image detection equipment outside the station. The processing includes denoising, grayscale and other processing, so that the acquired human face information is clear and easy to compare, and the pre-stored work The ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com