Malicious short message processing method and client based on false base station
An information processing method and short message technology, which are applied in the malicious short message processing method and client field based on pseudo-base stations, can solve the problems of user property loss, ensure user information and property security, and cannot process malicious short messages
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
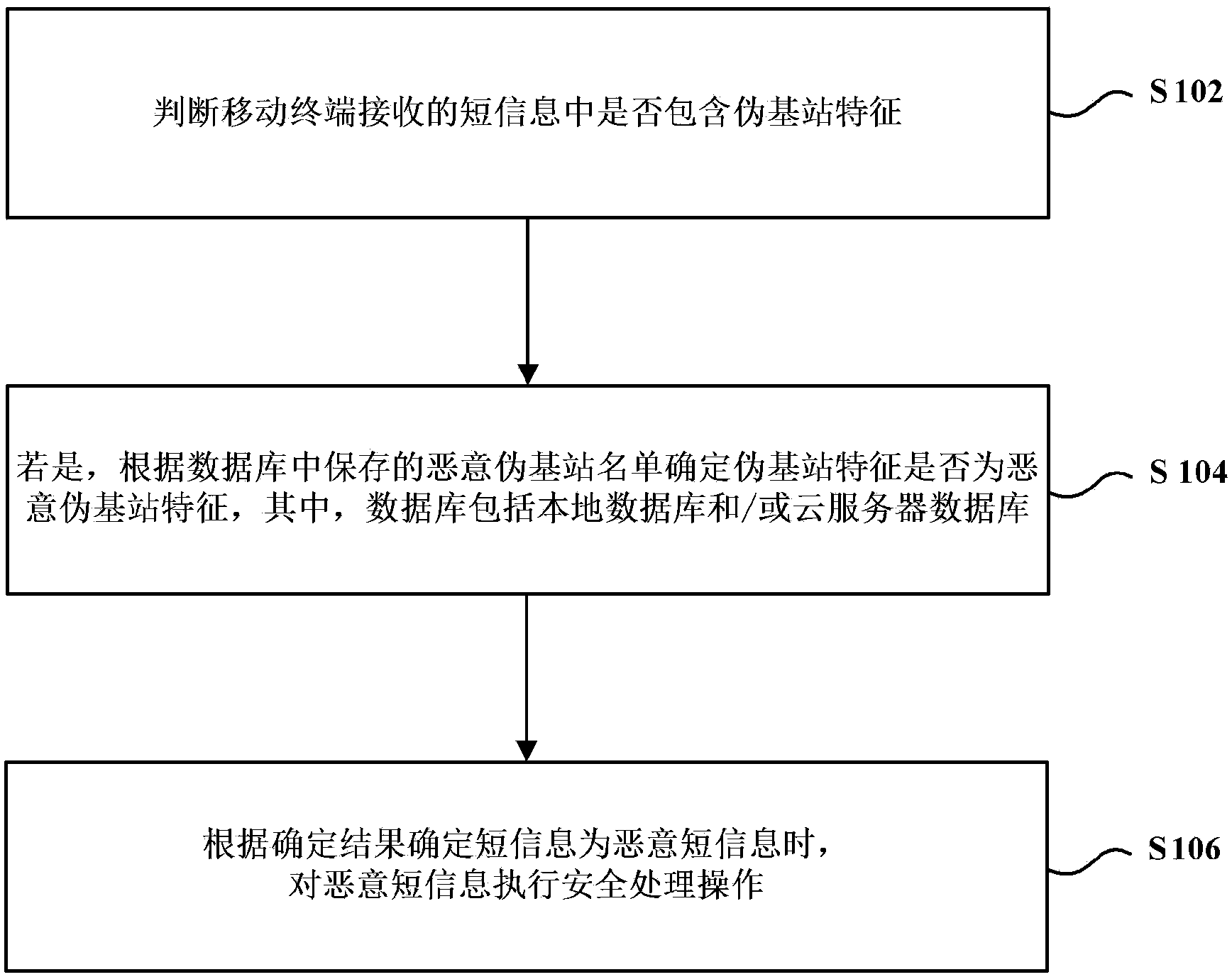
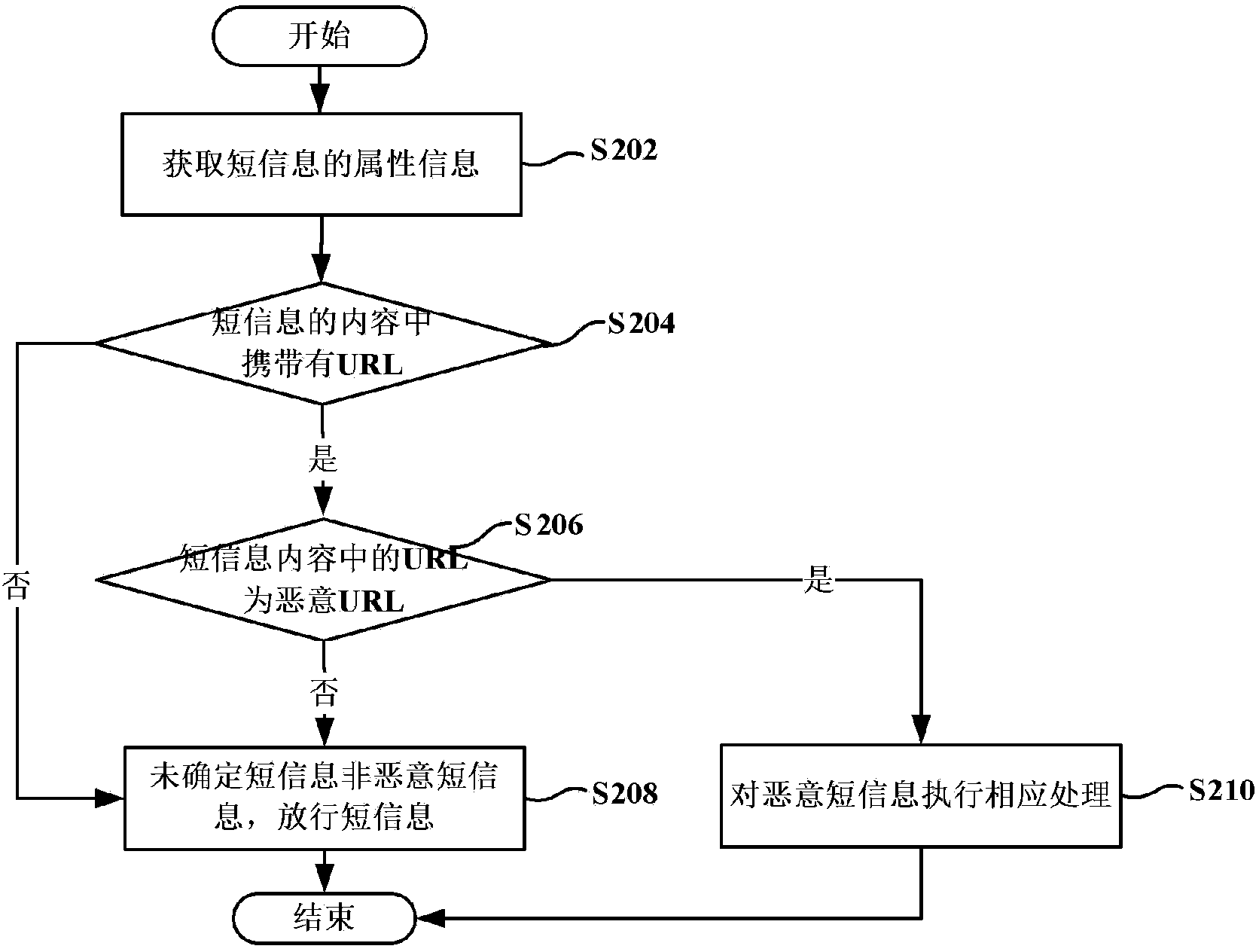
[0066] In order to clarify the methods for processing malicious short messages based on pseudo-base stations in the above embodiments, a preferred embodiment is now provided to receive the method for processing malicious short messages based on pseudo-base stations provided by the embodiments of the present invention. It should be noted that, in order to illustrate this preferred embodiment more clearly, in this example, the mobile terminal is set to be a mobile phone.
[0067] Figure 5 A processing flowchart of a method for processing malicious short messages based on a pseudo base station according to a preferred embodiment of the present invention is shown. see Figure 5 , the process includes at least step S502 to step S516.
[0068] Step S502, judging whether the sending number of the short message exists in the sending number whitelist. If yes, execute step S504; if not, execute step S516.
[0069] Specifically, in order to ensure high accuracy when determining whet...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com