Identity authentication method and system based on touch screen equipment and security and privacy encryption method
A technology of identity authentication and encryption method, which is applied in the field of security and privacy encryption, can solve the problems of limited application range of identity authentication and security privacy encryption, passwords are easy to be stolen, and complex operations, so as to improve information security and reduce the cost of acquisition and copying risk effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
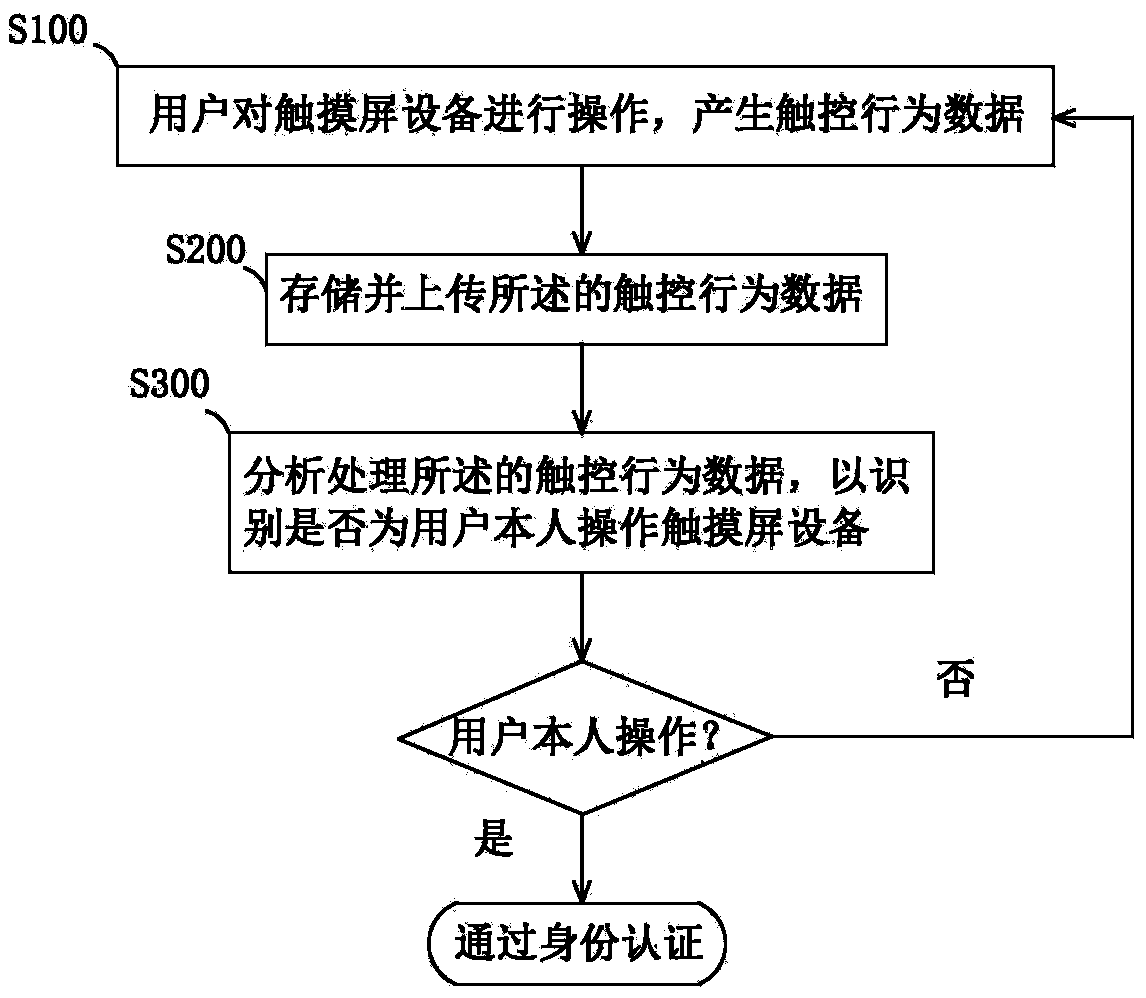
[0023] Please refer to figure 1 , the identity authentication method based on the touch screen device of the present invention includes: S100, the user operates the touch screen device to generate touch behavior data; S200, stores and uploads the touch behavior data; S300, analyzes and processes the touch Control behavior data to identify whether the touch screen device is operated by the user himself. If it is verified that the user operates the touch screen device, the identity authentication is passed; otherwise, the above steps are repeated until the user passes the identity authentication.
[0024] Preferably, the touch behavior data includes: touch coordinates, touch area, touch angle, touch force, and / or click time.
[0025] Preferably, said storing and uploading said touch behavior data includes: storing said touch behavior data locally, and / or uploading and storing said touch behavior data to a server.
[0026] Preferably, the analysis and processing of the touch beh...
Embodiment 2
[0031] The identity authentication method based on the touch screen device in this embodiment includes: the user operates the touch screen device to generate touch behavior data; stores and uploads the touch behavior data; analyzes and processes the touch behavior data to identify Whether the touch screen device is operated by the user himself or not, if it is verified that the user himself operates the touch screen device, the identity authentication is passed; otherwise, the above steps are repeated until the user passes the identity authentication.
[0032] Preferably, the touch behavior data includes: touch coordinates.
[0033] Preferably, the touch coordinate data is stored locally, and / or the touch coordinate data is uploaded and stored to the server.
[0034] Preferably, the touch coordinate data is subjected to algorithmic analysis to verify whether the touch coordinate data is within the range of data analyzed by the algorithm, and the algorithm analysis is as follows:...
Embodiment 3
[0036] The identity authentication method based on the touch screen device in this embodiment includes: the user operates the touch screen device to generate touch behavior data; stores and uploads the touch behavior data; analyzes and processes the touch behavior data to identify Whether the touch screen device is operated by the user himself or not, if it is verified that the user himself operates the touch screen device, the identity authentication is passed; otherwise, the above steps are repeated until the user passes the identity authentication.
[0037] Preferably, the touch behavior data includes: touch area.
[0038] Preferably, the touch area data is stored locally, and / or the touch area data is uploaded and stored to the server.
[0039] Preferably, the touch area data is subjected to algorithmic analysis to verify whether the touch area data is within the range of data analyzed by the algorithm, and the algorithm analysis is as follows: after setting the initial ar...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com