Implementation method and device of VPN (virtual private network) for edge equipment
An edge device and processing method technology, applied in the field of virtual private network, can solve the problems of complex configuration and table item content, and achieve the effect of reducing configuration and table item capacity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
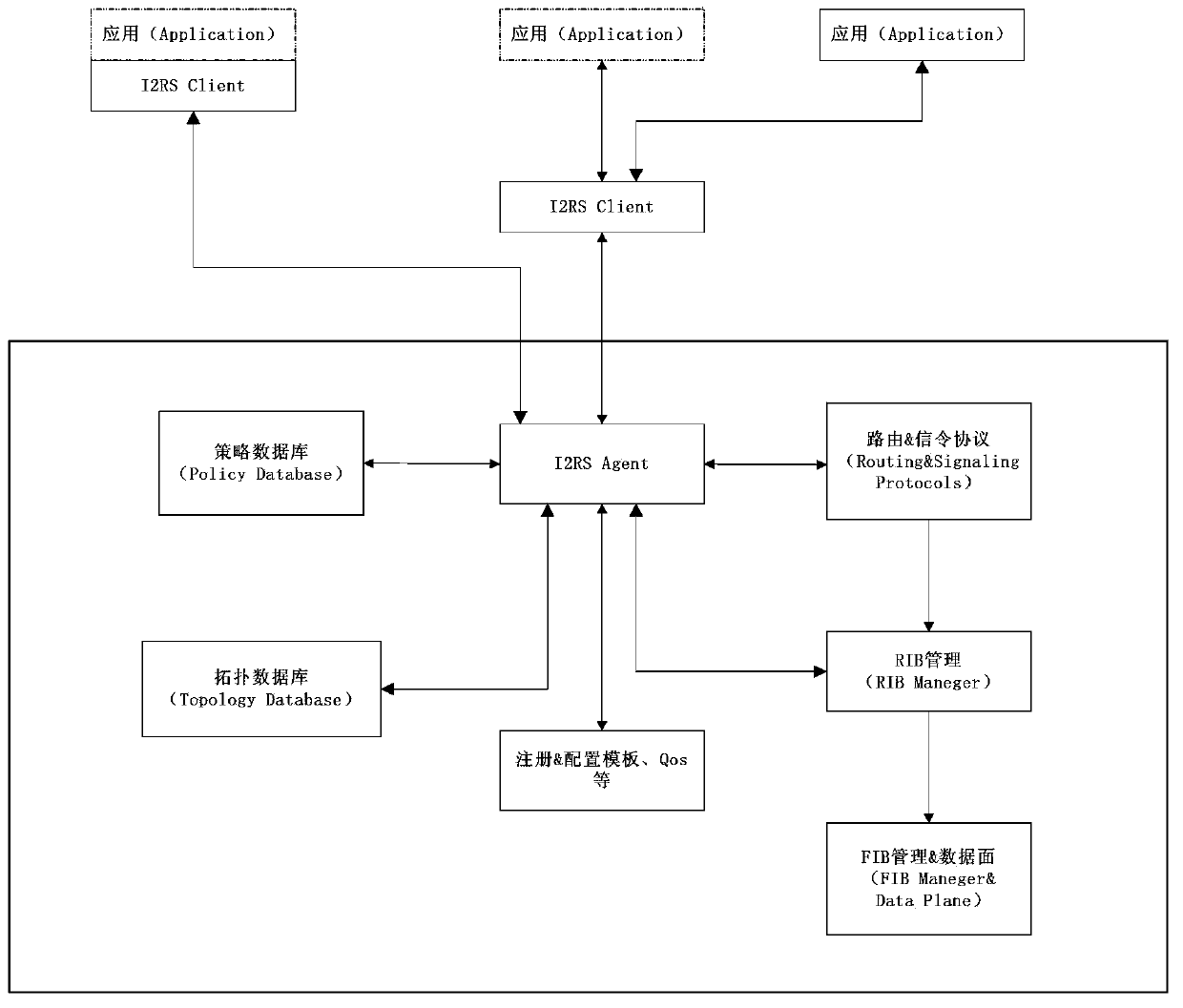
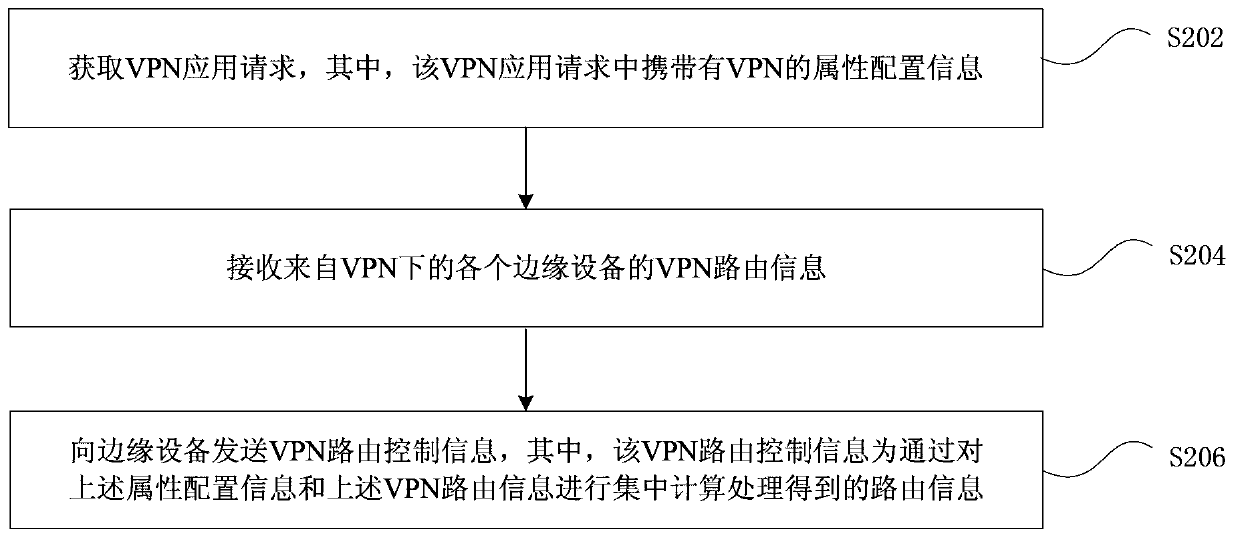
[0107]A method for dynamically establishing and managing VPN services on an IP / MPLS network through a network management system. The network management system receives application requests for VPN services, and performs unified control on table entries of forwarding device services at the operator's edge through interfaces, including:
[0108] After the network management system receives the VPN routing information sent by the operator's edge device, it combines the received information with the application request for centralized calculation and processing, and generates the calculated and processed information and sends it to the forwarding device.
[0109] The VPN routing information includes VPN Table ID, table entry, and the content of the table entry includes but is not limited to: table entry key value, next hop, outgoing interface, VPN identification, VPN forwarding plane identification, protocol type, active and standby Some or all of the items such as logo, load shari...
Embodiment 2
[0122] Example 2: L3VPN automatic control and delivery of related entries
[0123] Such as Figure 6 As shown, site 1 and site 3 belong to VPN1, and site 2 and site 4 belong to the same VPN2. When performing VPN access on each PE, the existing implementation needs to manually configure VPN1 on each PE. After the configuration is complete, the routes of VPN1 and VPN2 are maintained through different entries on each PE, and the RTs with matching attributes are imported and exported to the corresponding VPN forwarding table to realize VPN isolation. . In this way, PE1, PE2, and PE3 will be isolated on PE1, PE2, and PE3, and all effective local virtual routing / forwarding (virtual routing & forwarding instance, VRF for short) routes will be published in the VPN message carried by BGP. For example, the VPN1 message on PE1 is in PE2 will also receive it, but this message is completely invalid for PE2 and takes up bandwidth transmission and protocol packet filtering time.
[0124] ...
Embodiment 3
[0158] Embodiment 3: On the basis of Embodiment 1, the customer proposes a policy application process with traffic filtering and time period requirements
[0159] Such as Figure 6 As shown, on the basis of the description in Embodiment 1, when a user submits an application for opening a VPN service with a traffic filtering request. Specifically, users of VPN1 require some clients between different sites to provide direct access, and some clients cannot access across sites. For example, there are three client-side terminals accessing in site 1, and their IPs are IP1, IP2, and IP3, and there are only two terminals accessing in site 3, and their IPs are IP5 and IP6 respectively. It is required that IP1 and IP2 can communicate with IP5. IP3 and IP6 can only communicate with members in the same site. Then, according to the traffic filtering request, the relevant VPN entries are issued through the Client, so that IP1 and IP2 in Site 1 can issue entries on PE3, so that PE3 can only...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com