User identification method and system
A user identification and user information technology, applied in the user identification system, user identification field, can solve problems such as inability to distinguish users
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
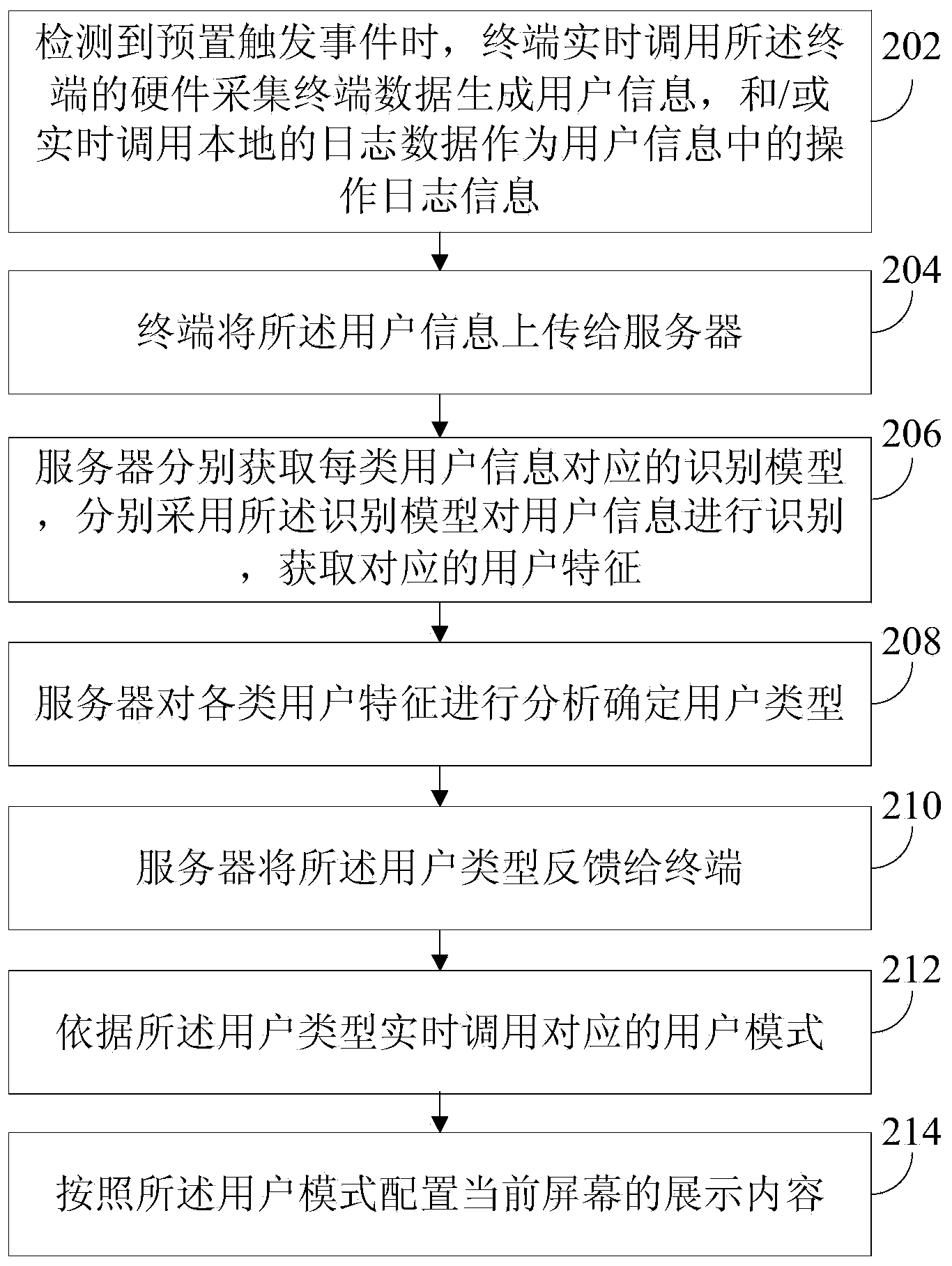
[0032] refer to figure 1 , which shows a flow chart of the steps of an embodiment of a user identification method in the present invention, which may specifically include the following steps:
[0033] Step 102, when a preset trigger event is detected, terminal data is collected in real time to generate user information.
[0034] Because different users can use the video playback application of the same terminal device to play videos, such as players and other devices, and different users have different requirements for video and other playback content. For example, some content is not suitable for children to watch, and some content is more interesting to the elderly. Therefore, it is necessary to distinguish between different users and provide different playback contents.
[0035] In order to distinguish users in real time and provide accurate playback content after changing users, it is necessary to collect terminal data when a preset trigger event is detected. Terminal dat...
Embodiment 2
[0046] On the basis of the above embodiments, this embodiment further discusses the user identification method.
[0047] Taking the mobile terminal as an example, identification may be performed only in the mobile terminal, or cooperative identification between the mobile terminal and the server may be used. This embodiment discusses using the cooperative identification between the mobile terminal and the server as an example.
[0048] refer to figure 2 , which shows a flow chart of steps in an optional embodiment of a user identification method of the present invention, which may specifically include the following steps:
[0049] Step 202, when a preset trigger event is detected, the terminal calls the terminal hardware in real time to collect terminal data to generate user information, and / or calls local log data in real time as operation log information in the user information.
[0050] When a preset trigger event is detected, for example, the operation of collecting user...
Embodiment 3
[0086] On the basis of the above embodiments, this embodiment also provides a user identification system.
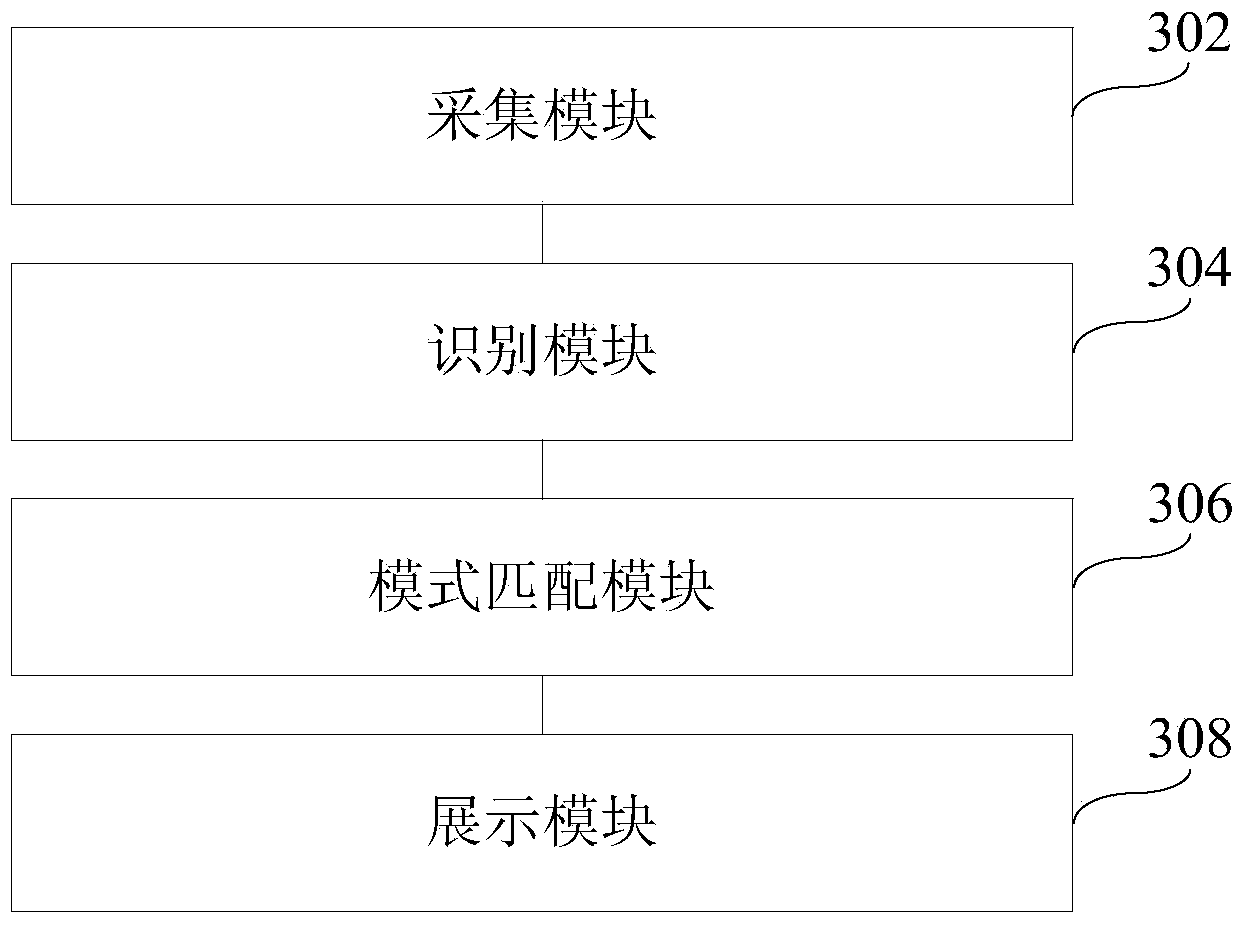
[0087] refer to image 3 , which shows a structural block diagram of an embodiment of a user identification system of the present invention, which may specifically include the following modules:
[0088] The collection module 302 is configured to collect terminal data to generate user information when a preset trigger event is detected, and the user information includes at least one of the following types: shooting information, device shaking information, screen touch information, and operation log information;
[0089] An identification module 304, configured to perform identification processing based on each type of user information, and determine the user type according to the identification result;
[0090] A pattern matching module 306, configured to invoke a corresponding user pattern in real time according to the user type;
[0091] The display module 308 is con...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com