WiFi Internet surfing connecting authentication method and system based on asymmetric full-process encryption
An authentication method and Internet technology, applied in the field of WiFi Internet connection authentication based on asymmetric whole-process encryption, can solve the problems of wireless WiFi network end security risks, phishing, inability to achieve end-end security and whole-process encryption authentication, etc., to avoid website effect of fishing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
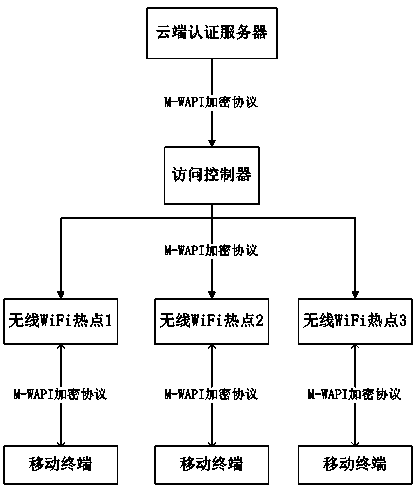
[0039] A method for authenticating a WiFi Internet access connection based on asymmetric full encryption, including: first, the cloud authentication server defines an encrypted access policy for an access controller, and the policy mainly defines an encryption method based on M-WAPI and a mobile terminal accessing the access policy. secondly, the cloud authentication server distributes the encrypted access policy to the designated access controller based on the M-WAPI protocol; thirdly, when the mobile terminal accesses WiFi for the first time, it needs to report its device MAC address to the access controller, and the access controller will This MAC address is reported to the cloud authentication server; then, based on the M-WAPI protocol, the access controller distributes the encrypted access policy to the mobile terminal that accesses WiFi for the first time; then, once the mobile terminal finds a WiFi hotspot, it uses the encrypted access policy to detect the WiFi hotspot. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com