Method, device and system for carrying out service access control on third-party application
A technology of service access and corresponding relationship, applied in the field of service access control for third-party applications, can solve problems such as property security threats, and achieve the effects of improving security, ensuring security, and increasing difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
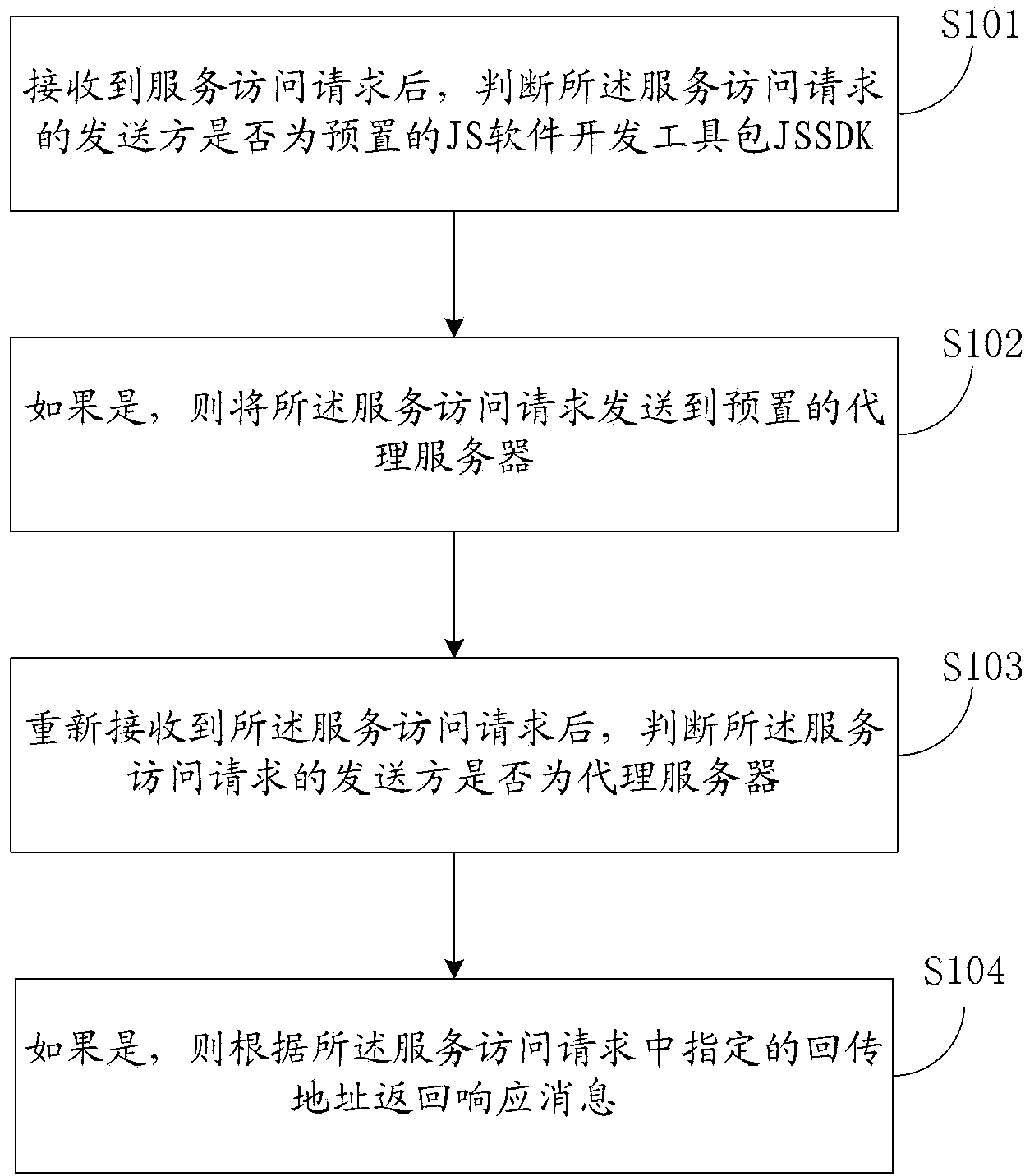
[0053] In the first embodiment, the technical solution of the present application is introduced from the perspective of the first server, that is, in the method involved, the execution subject of each step is the first server, and the first server is still in the form of a JS component Expose some functionality to third-party applications. see figure 1 , the method may include the following steps:
[0054] S101: After receiving the service access request, determine whether the sender of the service access request is the preset JS software development kit JSSDK; wherein, the JSSDK is provided by the first server and is added by the JS The component code automatically downloads the JSSDK to the local third-party application;
[0055] First of all, if a third-party application adds a certain JS component disclosed by the first server, the corresponding interface can be displayed on the webpage of the third-party application. For example, a third-party website adds the "shopping...
Embodiment 2
[0081] The first embodiment above introduces the technical solution provided by the embodiment of the present application from the perspective of the first server, and in the second embodiment, the technical solution provided by the embodiment of the present application is introduced from the perspective of the proxy server. see figure 2 The method for performing service access control on a third-party application from the perspective of a proxy server may include the following steps:
[0082] S201: Receive a service access request sent by the first server; the service access request is a service access request sent by a third-party application to the first server through JSSDK; wherein, the JSSDK is provided by the first server and is provided by the third-party application The added JS component code automatically downloads the JSSDK to the local third-party application;
[0083] S202: Perform a security check on the service access request according to the information carr...
Embodiment 3
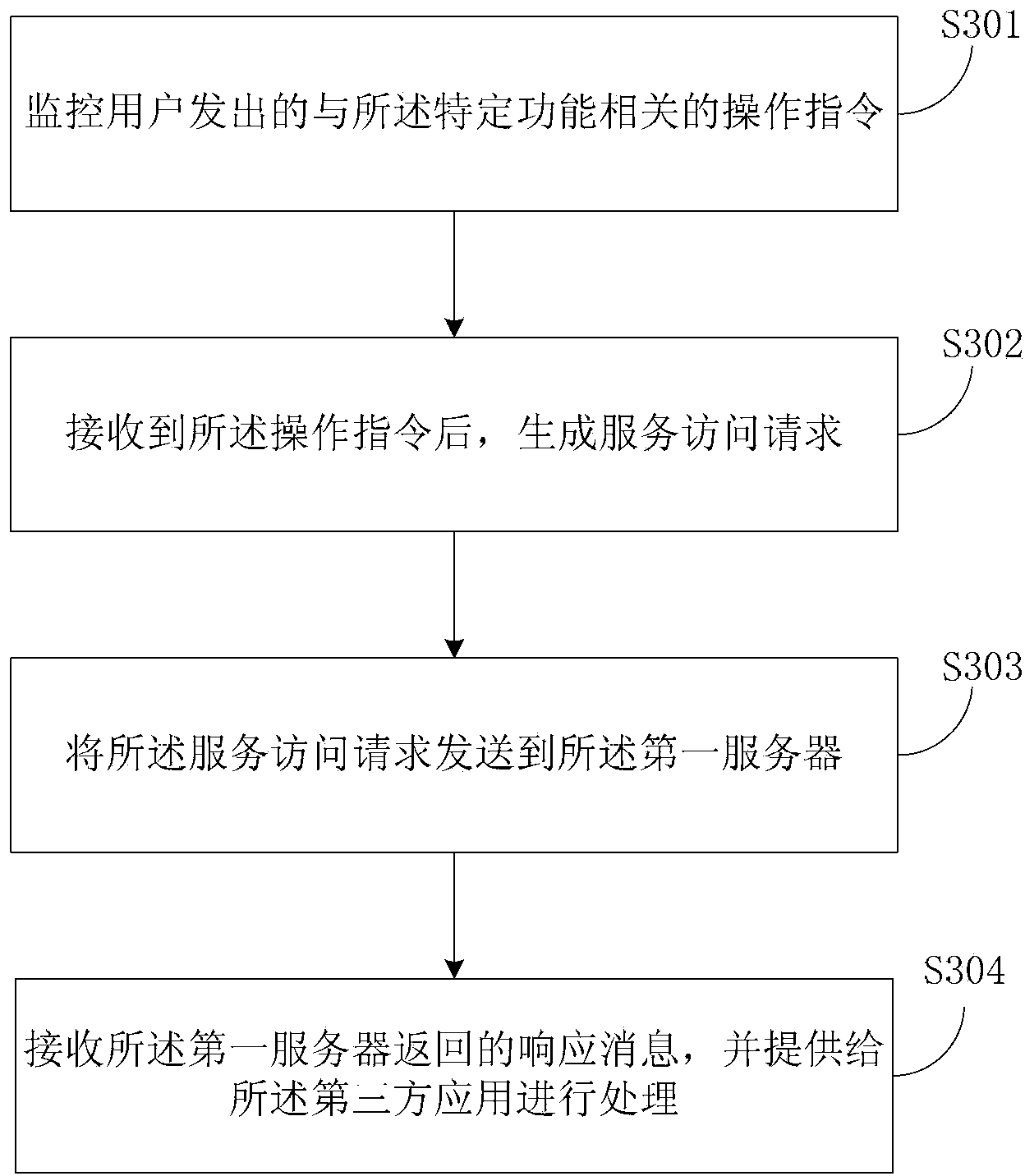
[0089] The third embodiment introduces the technical solution provided by the embodiment of the present application from the perspective of JSSDK. Among them, JS components corresponding to specific functions in the first server are added to the third-party application, and the code of the JS component automatically downloads the JSSDK provided by the first server to the third-party application, see image 3 The method for controlling service access to third-party applications from the perspective of JSSDK may include the following steps:
[0090] S301: Monitor an operation instruction related to the specific function issued by a user;
[0091] S302: After receiving the operation instruction, generate a service access request;
[0092] Specifically, when generating a service access request, an API to be called may be determined, API parameters are assembled, and a request for calling the API is generated. Wherein, when assembling the API parameters, information for performing ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com