SCADA file encryption method based on AES algorithm
A file encryption and algorithm technology, applied in computing, electrical components, computer security devices, etc., can solve problems such as linear redundancy, replacement box linear redundancy, weak ability to resist algebraic attacks, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
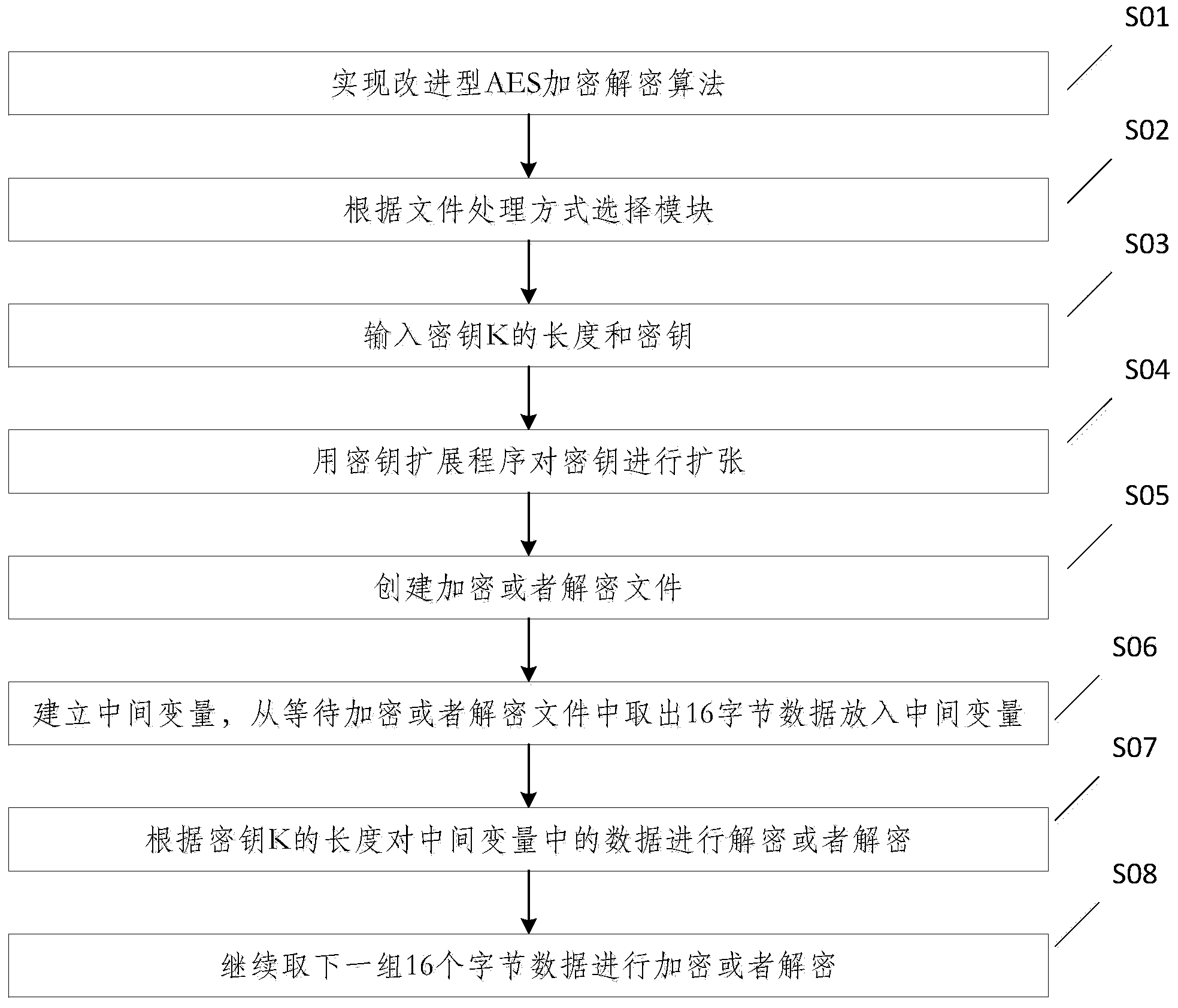
[0047] The present invention will be further described below in conjunction with the accompanying drawings.
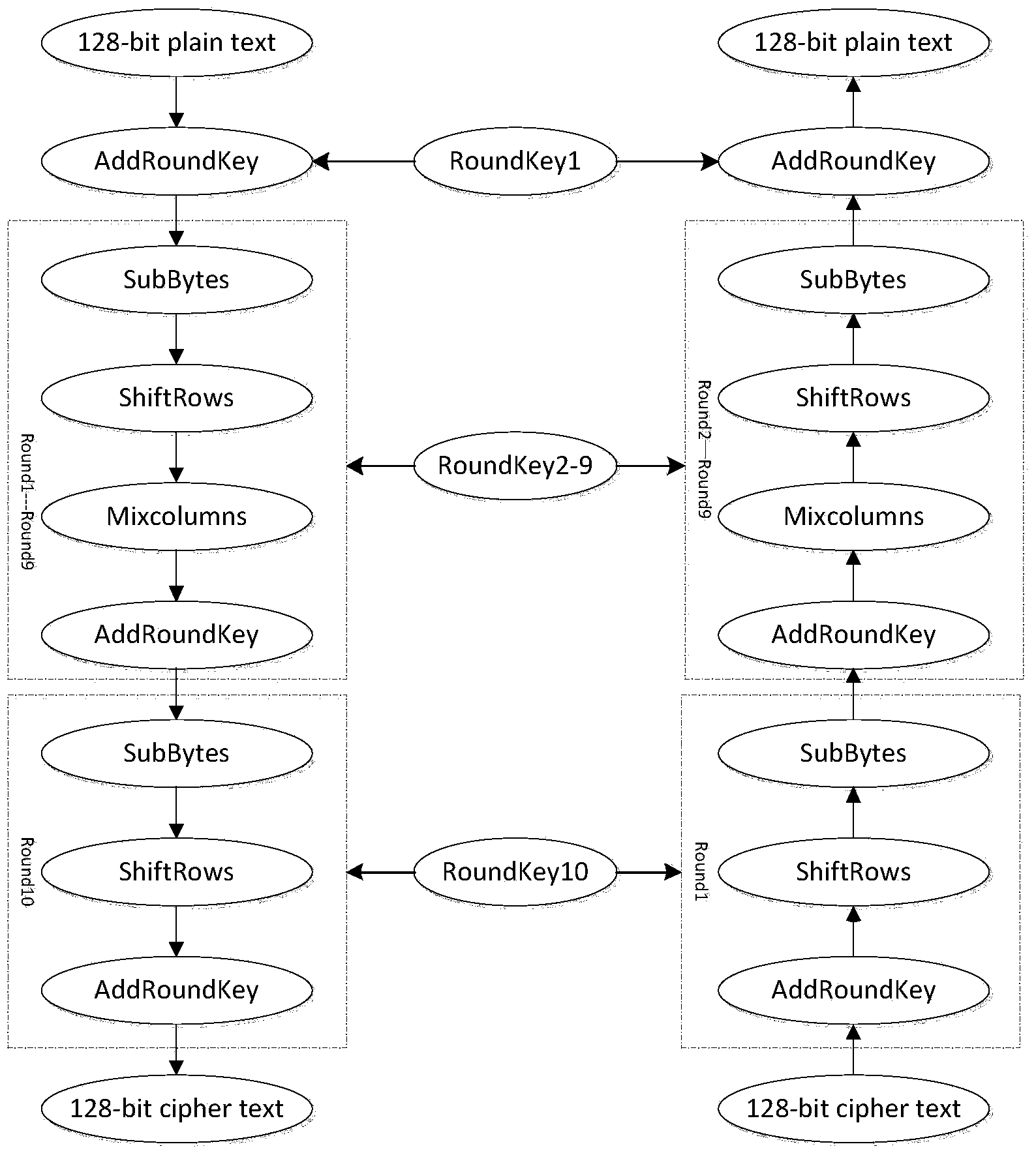
[0048]Realize a kind of SCADA file encryption method based on AES algorithm, at first need to set up AES algorithm transformation module, realize improved AES encryption and decryption algorithm; The improved AES encryption and decryption algorithm of the present invention comprises two parts.
[0049] In the first part, the new S replacement box is proposed.
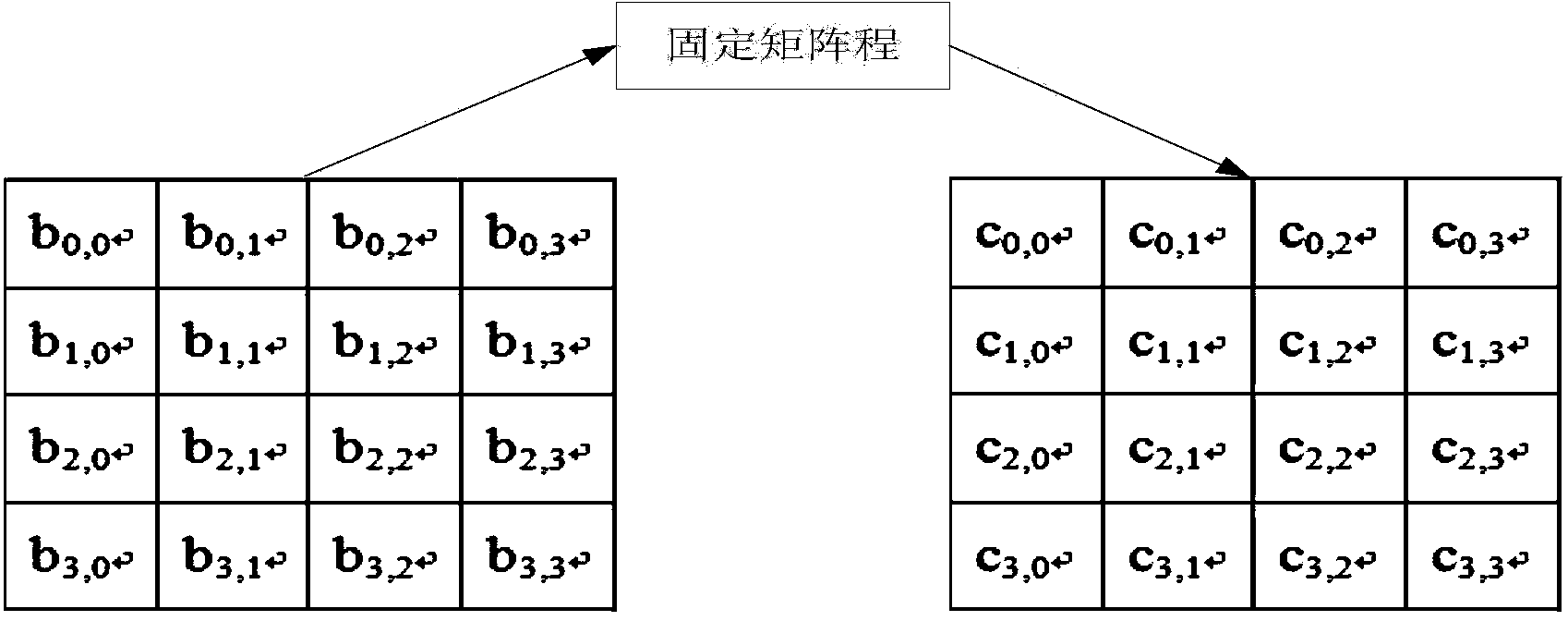
[0050] The AES algorithm is a block cipher algorithm. One of the cores of the block cipher algorithm is the S substitution box it uses. The S substitution box is the only non-linear place in the block cipher algorithm, and its strength determines the strength of the encryption algorithm. The cryptographic characteristics of the S-box are: differential uniformity, nonlinearity and autocorrelation; to improve the performance of the S-box, it is necessary to increase the nonlinearity and differential uniformity t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com