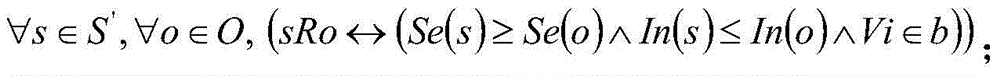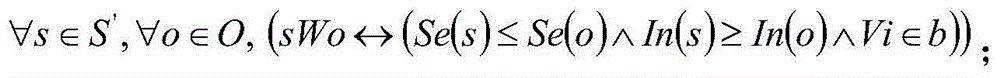Trust access control method for comprehensive avionics system
An avionics system and access control technology, applied in the direction of digital data authentication, platform integrity maintenance, etc., can solve problems such as aircraft safety and reliability hazards, to prevent leakage of sensitive information, ensure controllability and safety, The effect of credibility assurance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
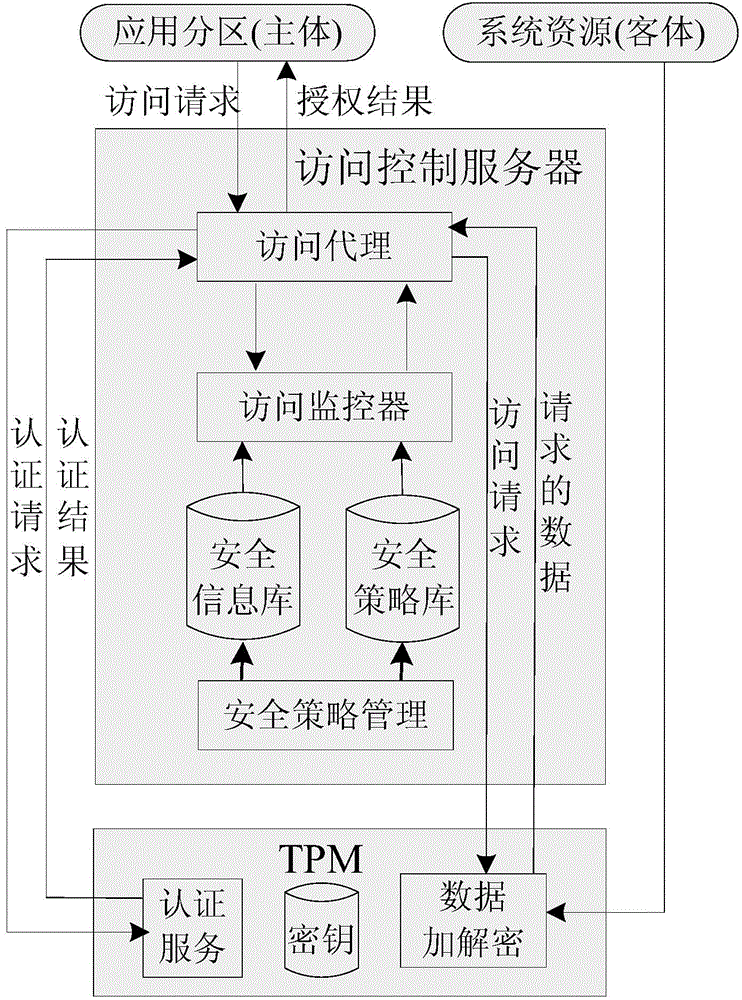
[0032] In the integrated avionics system, each call to system services or access to system resources must be authorized to ensure that only calls or access that comply with the control strategy can be performed. The access control based on the trusted access control system ensures the controllability and security of the application partition's access to system services and system resources, prevents malicious code from leaking sensitive information, and provides a strong guarantee for the credibility of the integrated avionics system. The access control model based on the trusted access control system draws on the ideas of the Bell-LaPadula (BLP) model and the BIBA model, considers the issues of confidentiality and integrity, and establishes a trusted authorization strategy.
[0033] according to figure 1 Concrete method of the present invention is described:
[0034] The steps of the trusted access control method are as follows:
[0035] 1) Build a trusted access control sy...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com