Authentication system suitable for distributed storage
A distributed storage and authentication system technology, applied in transmission systems, electrical components, etc., can solve unresolved leaks and other issues, and achieve the effects of protecting independence, improving security, and strong fault tolerance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] Embodiments of the present invention will be described below with reference to the drawings. Elements and features described in one drawing or one embodiment of the present invention may be combined with elements and features shown in one or more other drawings or embodiments. It should be noted that representation and description of components and processes that are not related to the present invention and known to those of ordinary skill in the art are omitted from the drawings and descriptions for the purpose of clarity.
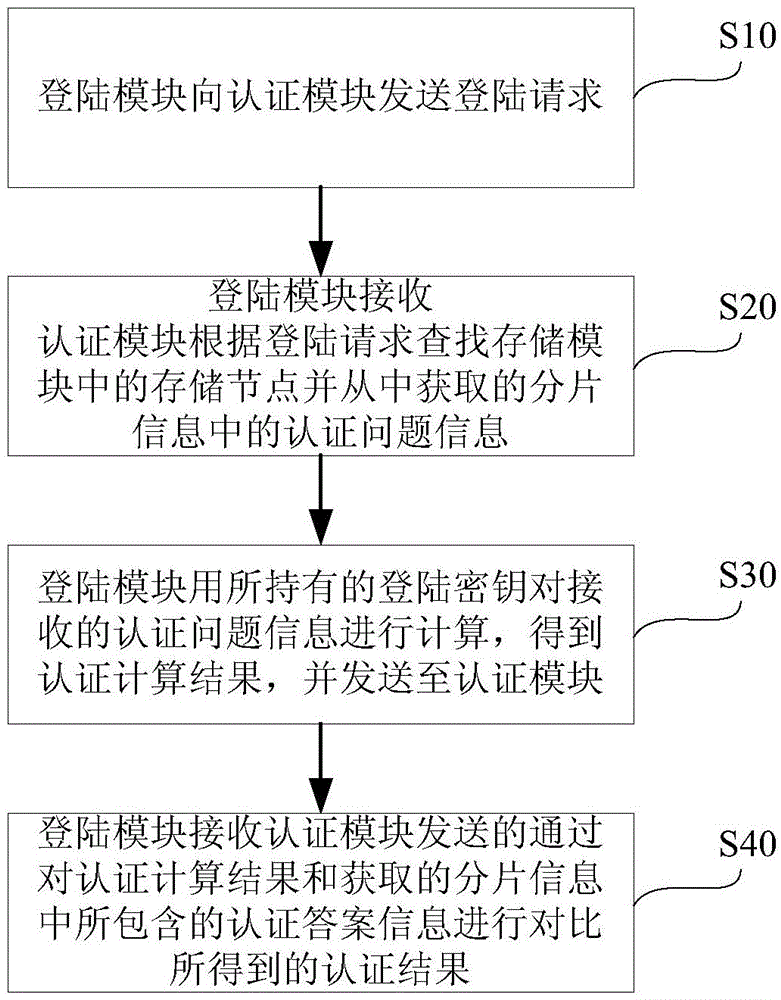
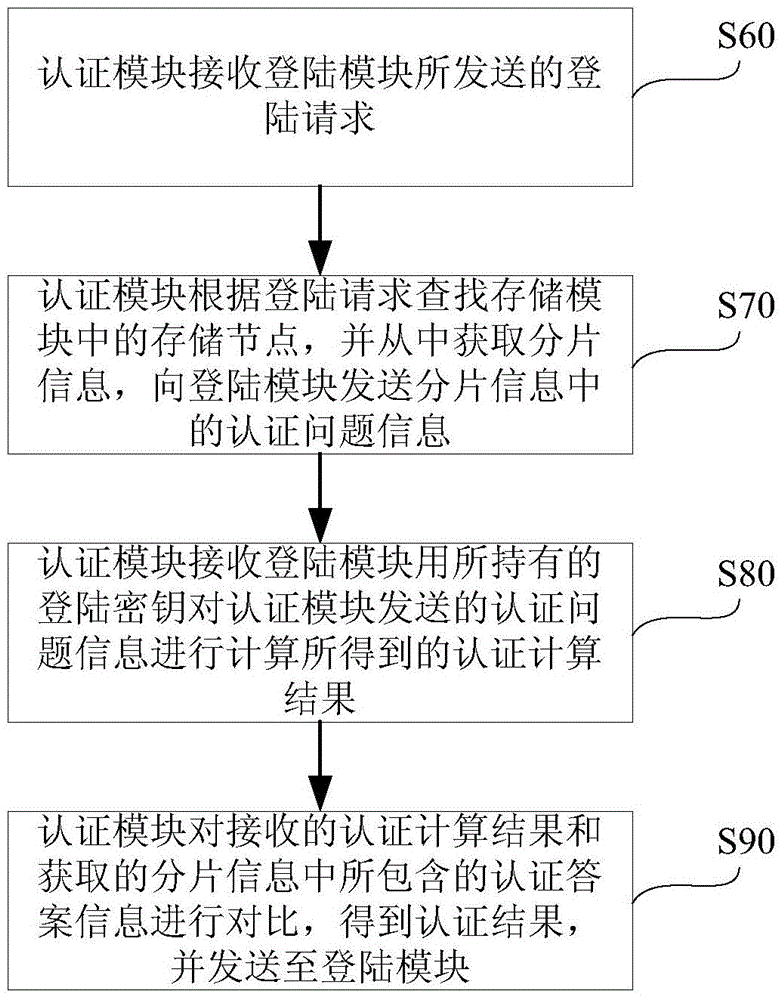
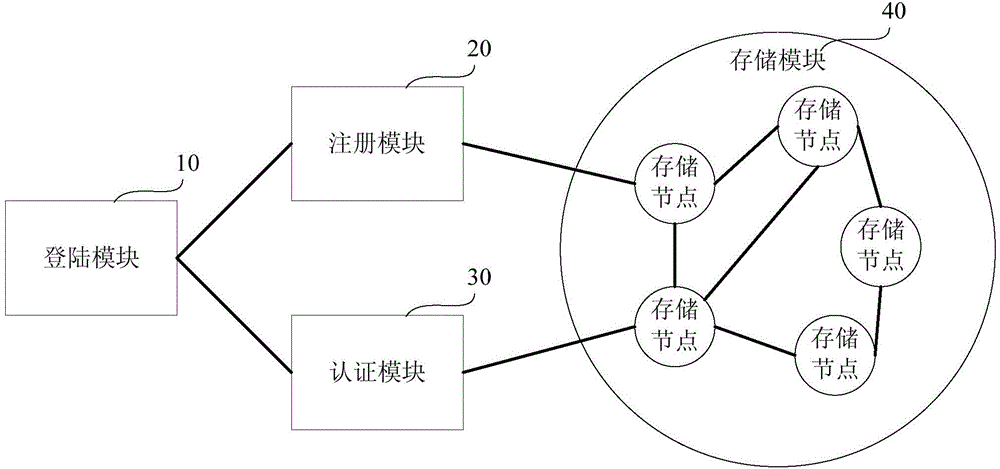
[0017] figure 1 It is a flow chart of the working principle of an implementation mode of the authentication system applicable to distributed storage of the present invention.
[0018] like figure 1 As shown, in this embodiment, the working principle flow of the authentication system applicable to distributed storage includes:
[0019] S10: The login module sends a login request to the authentication module. Specifically, the login module sends ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com