Method of detecting viral sources in cloud storage environment
A detection method and virus source technology, applied in the information field, can solve problems such as incomplete reliability, long log analysis time-consuming, affecting system stability, etc., to achieve accurate detection, reduce time, and realize the effect of automation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The preferred embodiments of the present invention will be described below in conjunction with the accompanying drawings. It should be understood that the preferred embodiments described here are only used to illustrate and explain the present invention, and are not intended to limit the present invention.
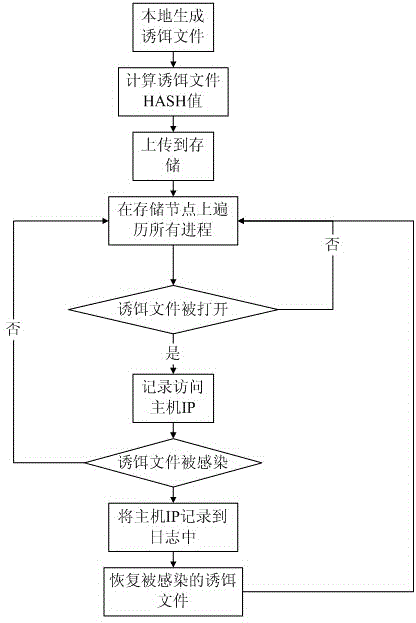
[0026] Such as figure 1 Shown, a kind of cloud storage environment virus source detection method comprises the following steps:
[0027] Step 1. Collect infected file types;
[0028] Step 2, locally create a file of the same type as the infected file in the above step 1, and calculate the HASH value of the file at the same time;
[0029] Step 3. Copy the file created in the above step 2 to the storage as a decoy file;
[0030] Step 4, traversing the files being accessed by all processes on the storage access node;
[0031] Step 5. If the decoy file is found to be opened by a process, immediately record the IP of the accessed host, and display the IP on the termin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com