Database access control method on basis of multi-strategy integration
An access control and database technology, applied in digital data protection, electronic digital data processing, instruments, etc., can solve the problems of autonomous access control, which is difficult to control the security level from the whole, lack of flexibility, etc., to achieve enhanced security and flexibility, Avoid the effects of permission conflicts
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
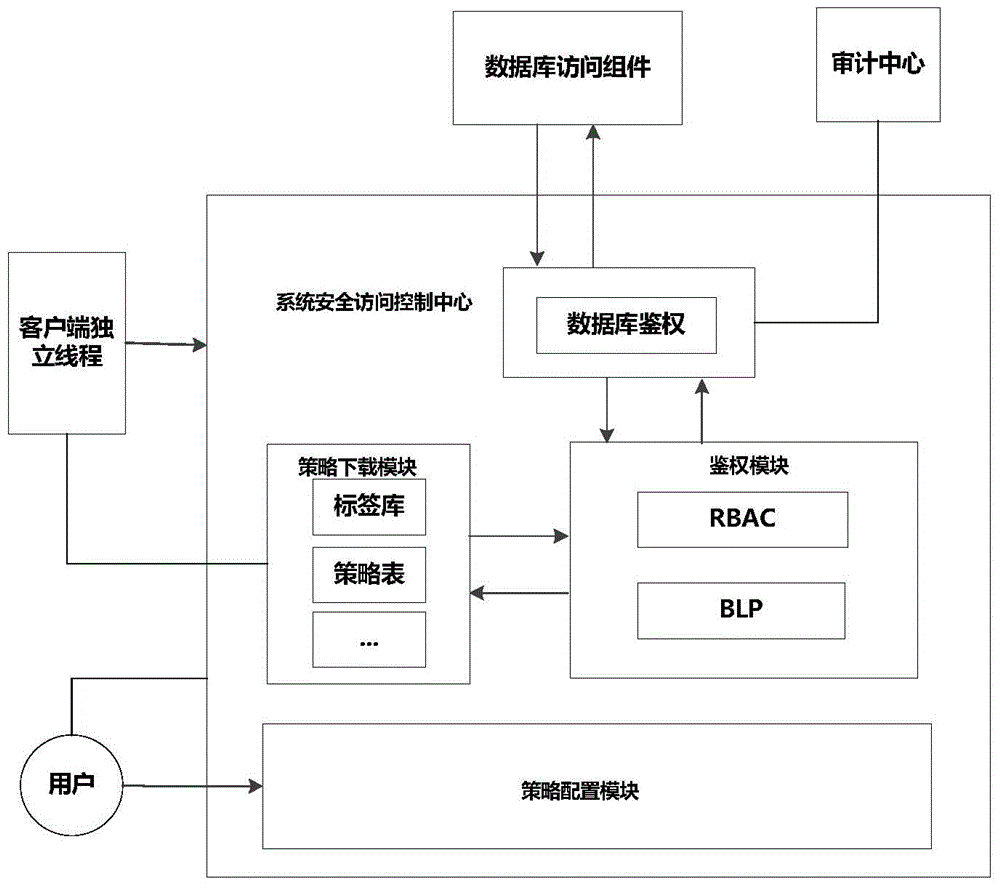
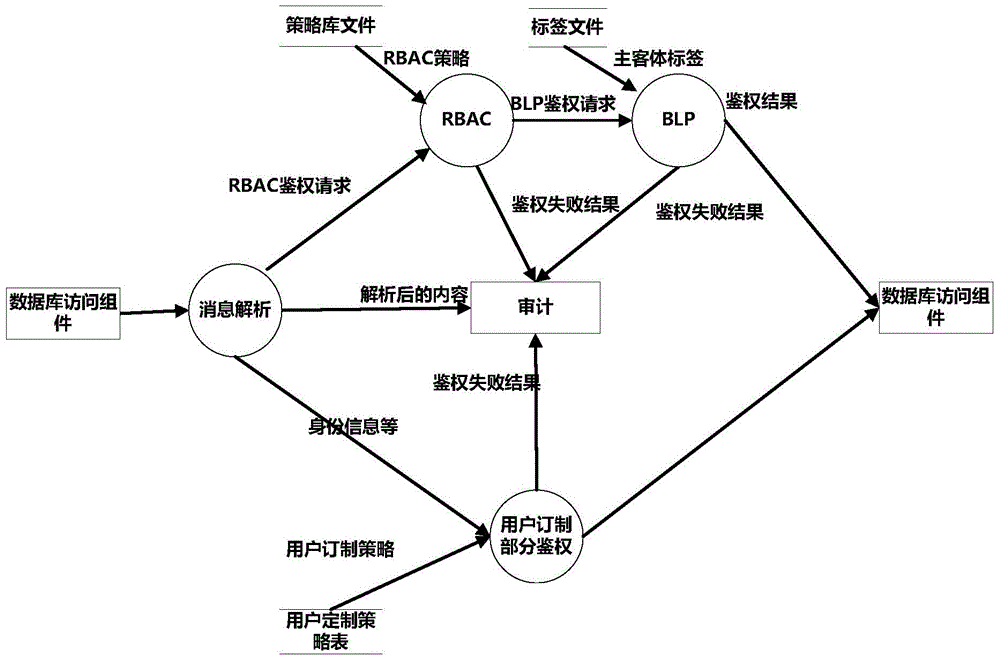
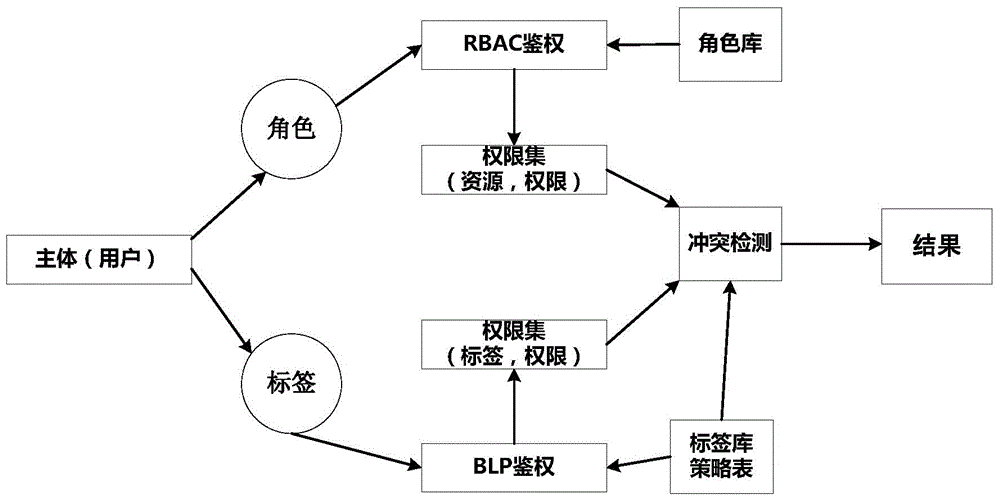
[0030] The invention adopts a role-based security access control (Role Based Access Control, RBAC) and a secret-level-based mandatory access control (BLP) strategy to control the access of a multi-security level database system. System administrators can perform fine-grained configuration based on user identity and role, and divide database object resources into multiple security levels. Any database access operation needs to be authenticated by the system access control center. The system security access control first determines whether the current requesting user has a user subscription. If there is a user subscription, the authentication result is returned by checking the user subscription table. If not For user customization, the RBAC module is used to judge whether the role corresponding to the user has corresponding access rights to the database tables to be accessed. If there is no access rights, the access is denied; The operation permission to access the fields in the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com