Virtual safety detecting method and system
A security detection and virtualization technology, applied in the computer field, can solve the problem of high physical machine resource occupation, achieve the effect of reducing resource occupation, improving efficiency, and increasing resource occupation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
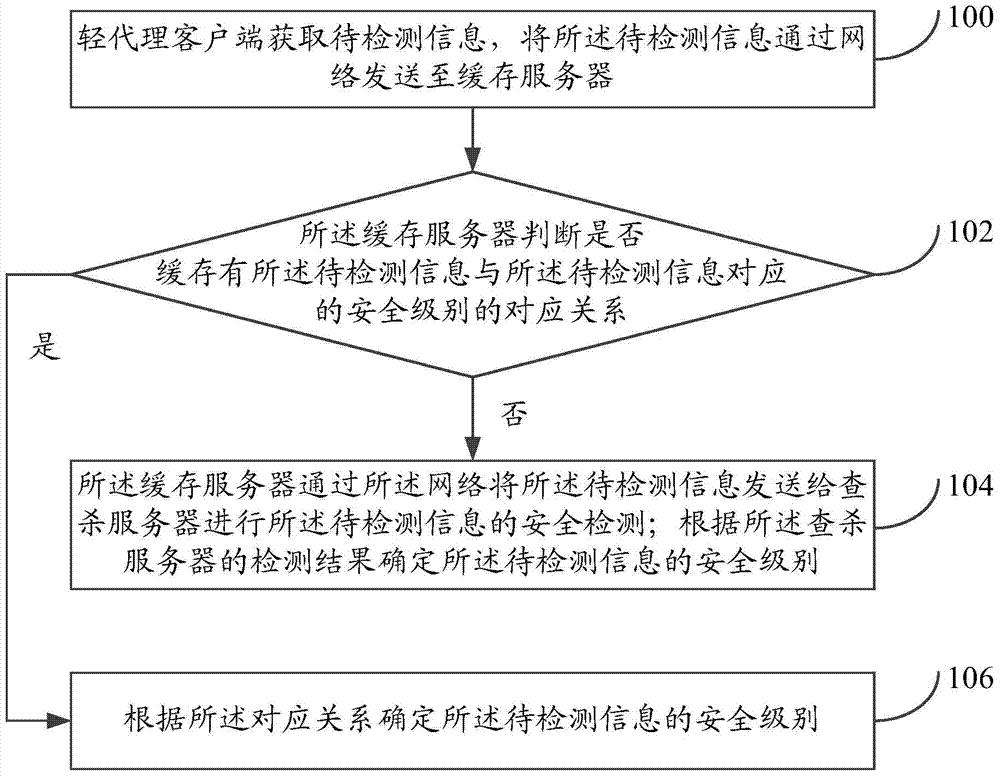
[0063] A virtualization security detection method provided by an embodiment of the present invention is introduced in detail.
[0064] refer to figure 1 , shows a flow chart of steps of a virtualization security detection method in an embodiment of the present invention.
[0065] The virtualization security detection method in the embodiment of the present invention can be applied to a system including a light agent client, a cache server, and an antivirus server.
[0066] Wherein, the light proxy client may be set in a virtual machine, and the cache server and the killing server may be set in a virtual machine or a physical machine. For example, the light proxy client can be set in one virtual machine among multiple virtual machines, and the cache server and the killing server can be set in only one physical machine, or can also be set in one In one virtual machine, optionally, the light proxy client, the cache server and the antivirus server may be set in the same virtual ...
Embodiment 2
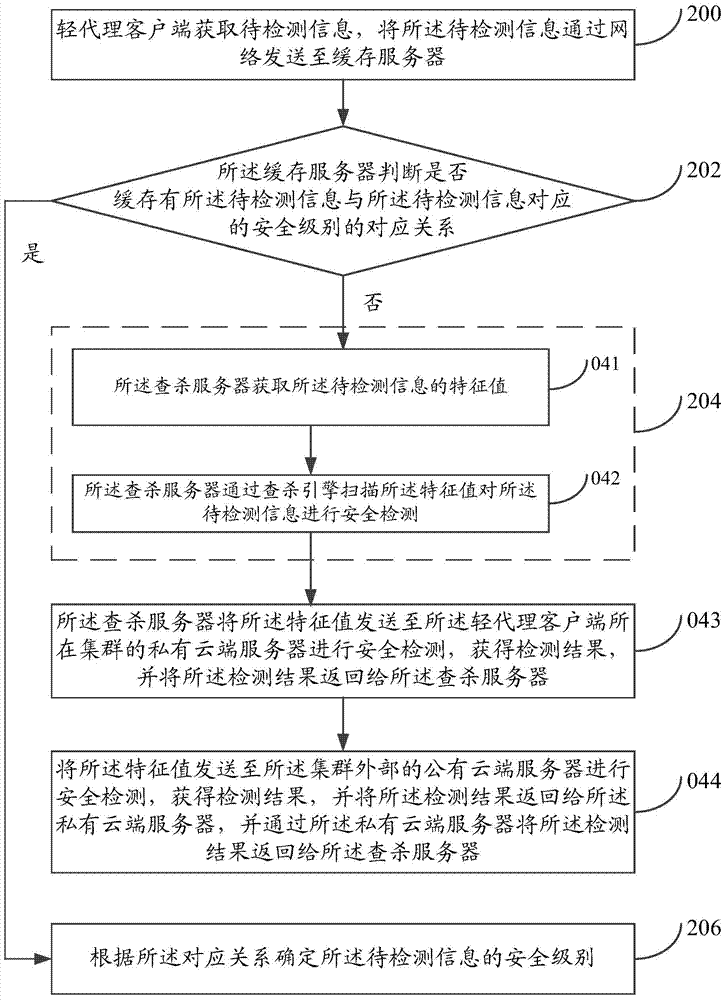
[0081] A virtualization security detection method provided by an embodiment of the present invention is introduced in detail.
[0082] refer to figure 2 , shows a flow chart of steps of a virtualization security detection method in an embodiment of the present invention.
[0083] The virtualization security detection method in the embodiment of the present invention can be applied to a system including a light agent client, a cache server, and an antivirus server.
[0084] Wherein, the light proxy client may be set in a virtual machine, and the cache server and the killing server may be set in a virtual machine or a physical machine. For example, the light proxy client can be set in one virtual machine among multiple virtual machines, and the cache server and the killing server can be set in only one physical machine, or can also be set in one In one virtual machine, optionally, the light proxy client, the cache server and the antivirus server may be set in the same virtual...
Embodiment 3
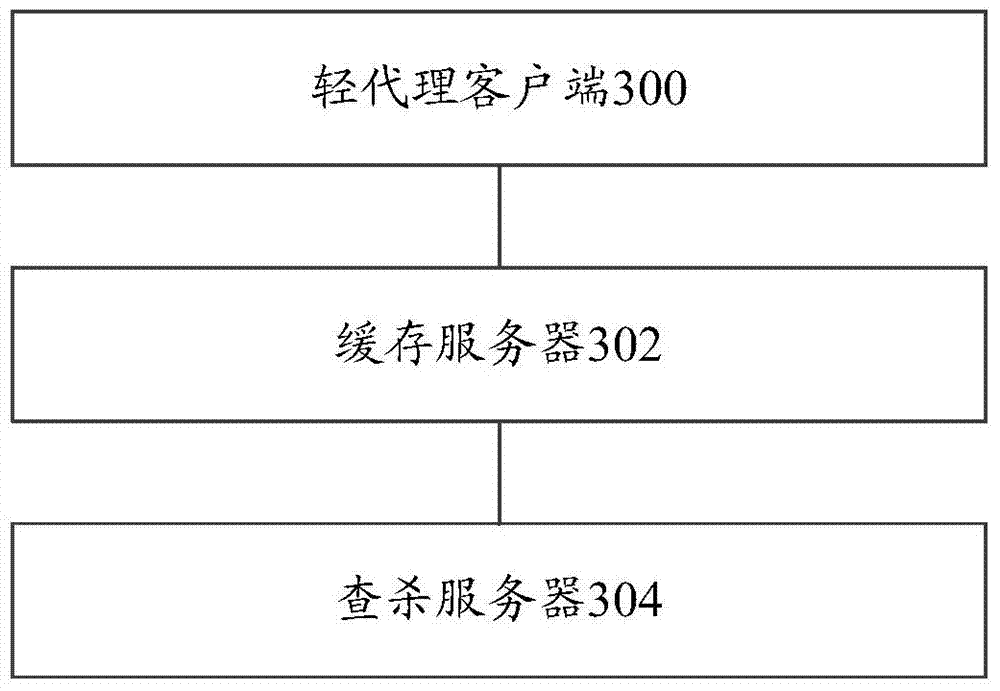
[0125] A virtualization security detection system provided by an embodiment of the present invention is introduced in detail.
[0126] refer to image 3 , shows a structural block diagram of a virtualization security detection system in an embodiment of the present invention.
[0127] The system may include: a light proxy client 300 set in a virtual machine, a cache server 302 and an killing server 304;
[0128] Wherein, the cache server 302 and the killing server 304 can be set in a physical machine or a virtual machine. For example, the light proxy client 300 can be set in one virtual machine among multiple virtual machines, and the cache server 302 and the killing server 304 can be set in only one physical machine, or Set in a virtual machine, optionally, the light proxy client 300, the cache server 302 and the killing server 304 can be set in the same virtual machine among multiple virtual machines, while other virtual machines There is no need to set it in the machine....
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com