Web site access security audit method for MIPS (Million Instructions Per Second) platform
A security audit and security technology, applied in special data processing applications, digital transmission systems, electrical components, etc., can solve the problem of increasing the controllability of network security faults, affecting system administrator decision revision and task deployment, and inability to effectively capture events References and other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
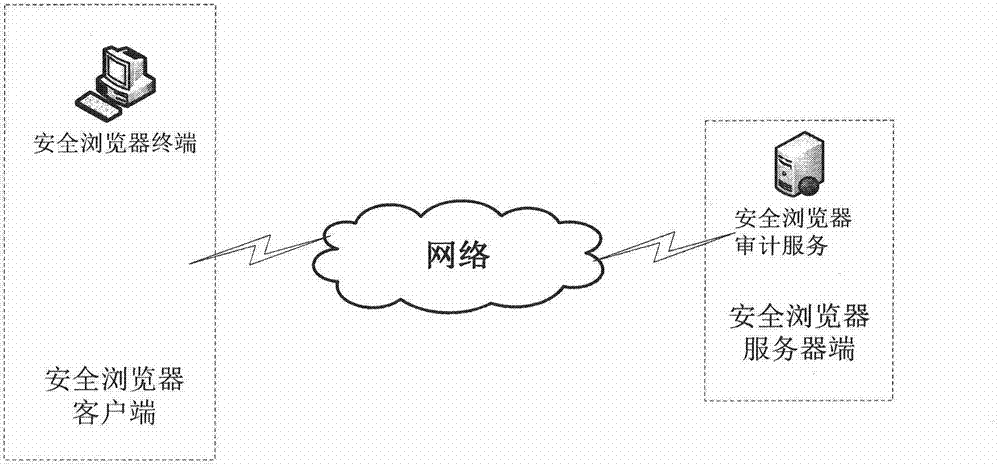
[0016] Such as Figure 1-2 Shown, a kind of MIPS platform Web site access security audit method, described MIPS platform comprises safe browser client and safe browser server end, and described client is provided with the safe browser that has system access auditing function, and described safe The browser server is provided with a security browser audit server, and the security audit method specifically includes the following steps:
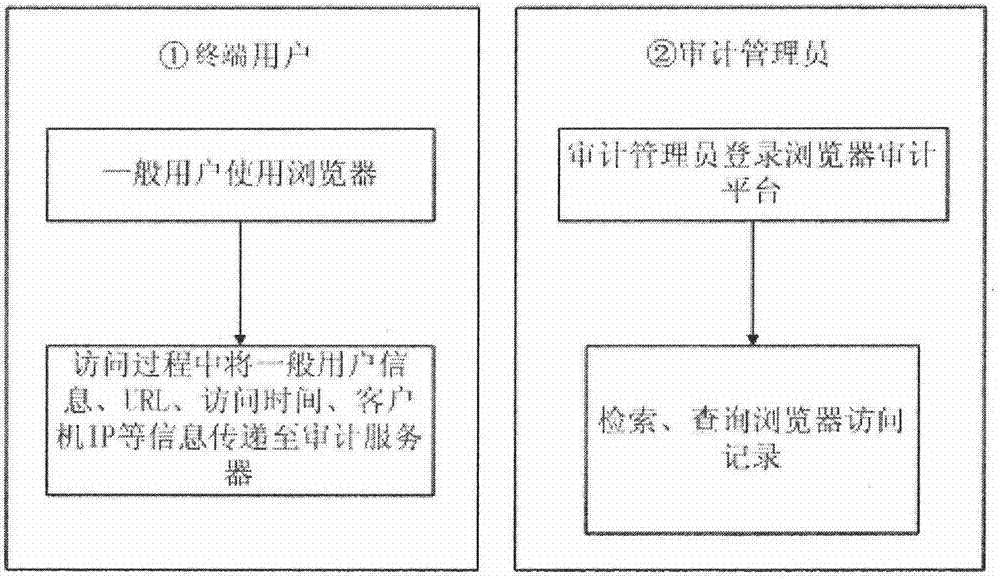
[0017] (1) Terminal user such as A opens a browser on a secure browser terminal and enters a URL address to visit a certain website;
[0018] (2) Information such as the URL access address, user name, access time, and IP of the computer used by the terminal user such as A is sent to the security browser audit server through the network, and is recorded and stored by the security browser audit server;
[0019] (3) The audit system administrator opens the audit management system of the full-browser audit server on the secure browser server side t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com