Invasion detection method and device
An intrusion detection and data point technology, applied in the field of information security, can solve problems such as high computational overhead and affect clustering results, achieve good clustering effect, reduce computational overhead, and enhance ease of use and practicability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
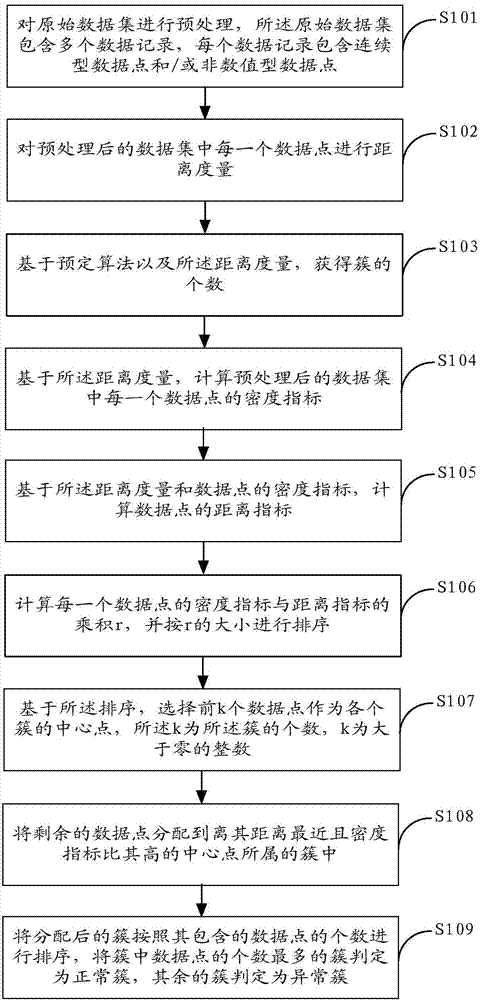
[0033] figure 1 The implementation flow of the intrusion detection method provided by Embodiment 1 of the present invention is shown, and the process of the method is described in detail as follows:
[0034] In step S101, the original data set is preprocessed, and the original data set includes a plurality of data points.
[0035] In the embodiment of the present invention, the original data set contains multiple data records (such as heterogeneous data records), and each data record may contain continuous data points and / or non-numeric data points, which need to be separately Perform data normalization processing, specifically:
[0036] For continuous data points in the original data set, map its data value from [min, max] to an interval whose range is smaller than the preset value (such as [0, 1] interval);
[0037] For the non-numerical data in the original data set, after discretization, it is encoded and mapped into a numerical value, or directly compared in the distanc...
Embodiment 2
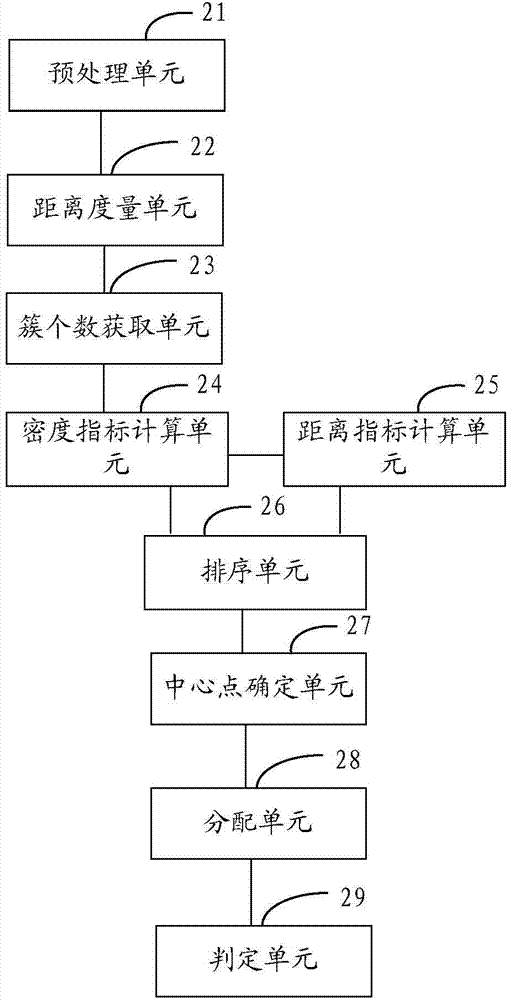
[0064] figure 2 The composition structure of the intrusion detection device provided by the second embodiment of the present invention is shown, and for the convenience of description, only the parts related to the embodiment of the present invention are shown.
[0065] The intrusion detection device can be a software unit, a hardware unit, or a combination of software and hardware running in each terminal device (such as a mobile phone, a tablet computer, etc.), or it can be integrated into the terminal device as an independent pendant or run on the In the application system of the terminal device.
[0066] The intrusion detection device includes:
[0067] The preprocessing unit 21 is used to preprocess the original data set, the original data set includes a plurality of data records, and each data record includes continuous data points and / or non-numeric data points;
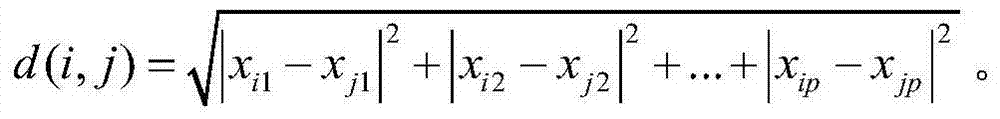
[0068] A distance measurement unit 22, configured to perform distance measurement on each data point in ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com