A Dirty Data Propagation Path Discovery Method Based on Complex Network
A complex network and discovery method technology, applied in software testing/debugging, etc., can solve problems such as unsupported binary program discovery
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The present invention will be further described in detail below in conjunction with the accompanying drawings.
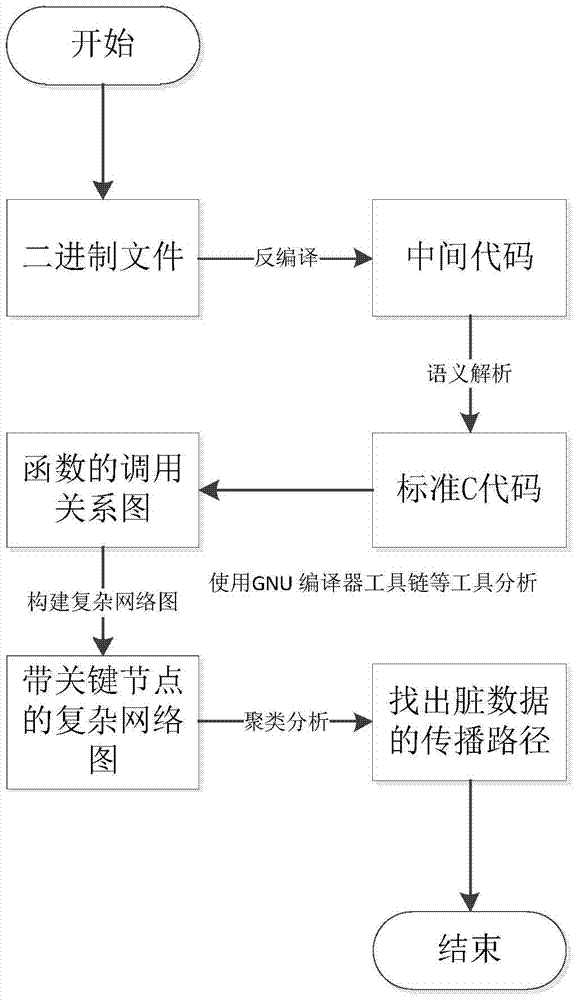
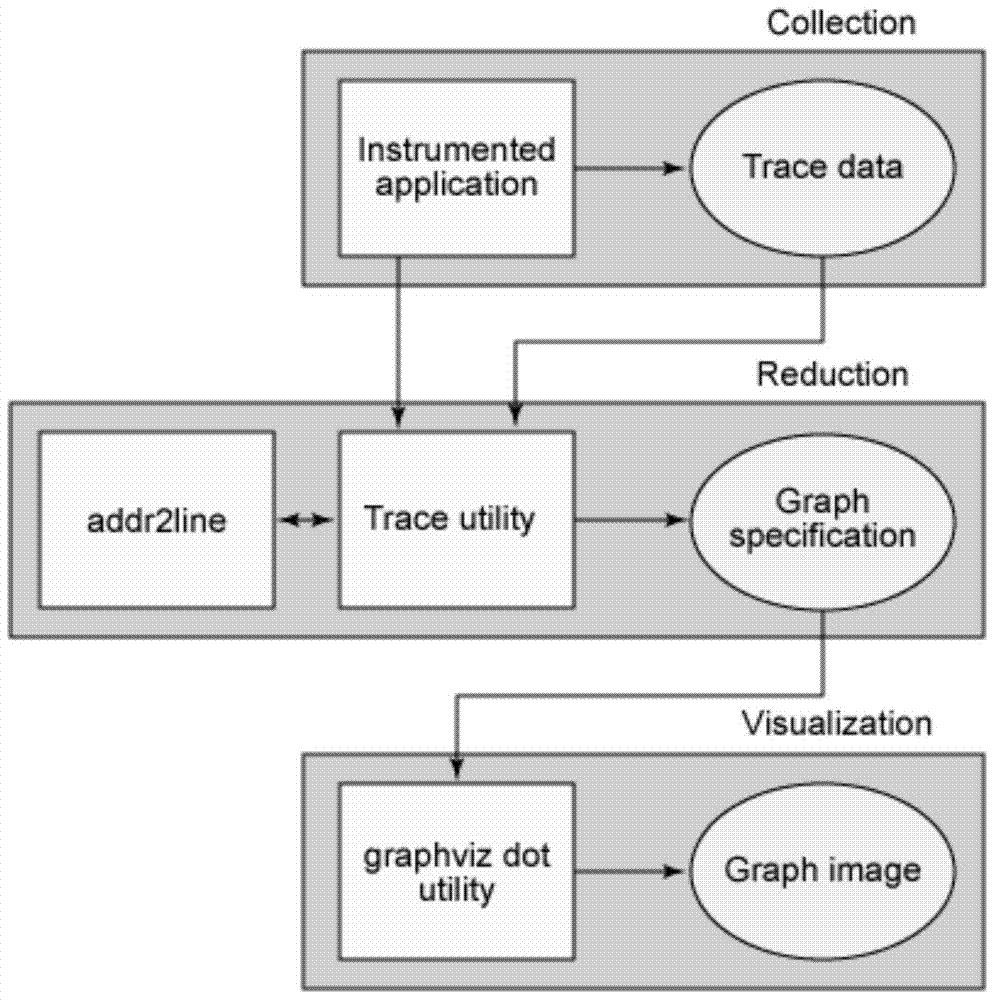
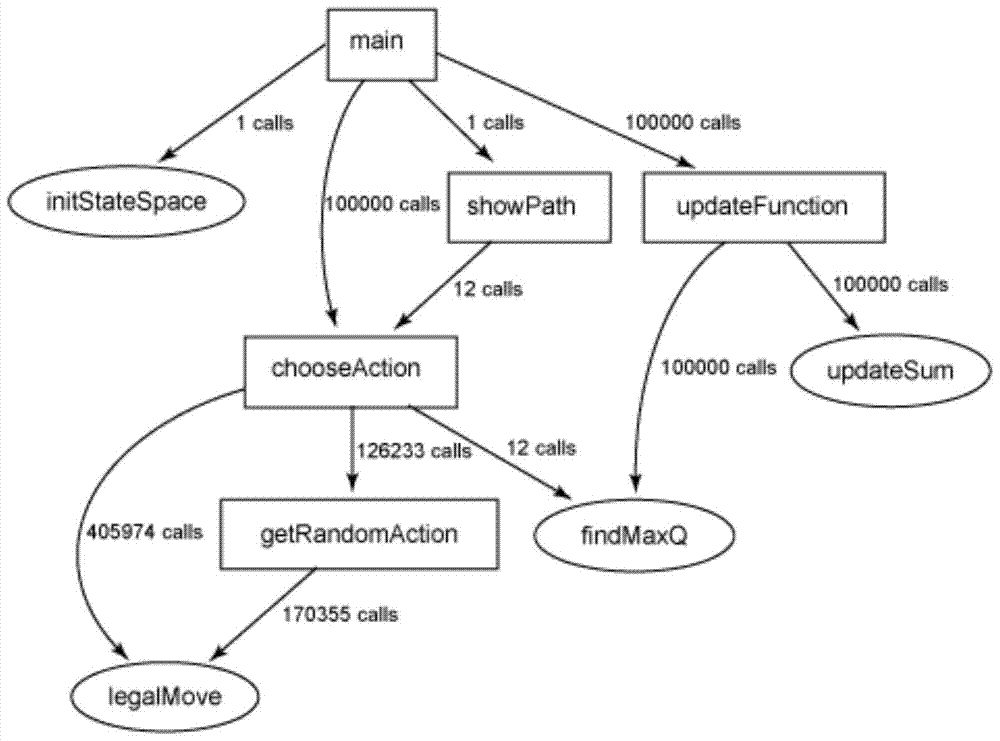
[0026] The embodiment of the present invention is roughly divided into three parts: one is to decompile the binary file to obtain a processable source code or an analyzable intermediate language, which is completed using the IDA plug-in Hex-Rays; the other is to decompile the decompiled result Analyze and give the call relationship diagram of the function. This part is completed using the GNU compiler tool chain, Addr2line tool, and Graphviz tool; the third is to generate a complex network diagram with key nodes based on the relationship diagram, using graph theory and complex network Knowledge to find out the propagation path of dirty data.
[0027] Combine below figure 1 Describe the workflow of the present invention in detail:
[0028] 1. Decompile
[0029] After comparing multiple decompilation tools, the present invention decides to use IDA plug-in He...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com