A Dynamic Detection Method of Buffer Overflow Vulnerabilities Based on Function Call
A buffer overflow and function call technology, applied in the field of information security, can solve the problems of abstract syntax tree occupying memory, inaccurate positioning, high false negative rate, etc., and achieve the effect of reducing dependence, high measurement accuracy and low false positive rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] The present invention will be described in detail below with reference to the accompanying drawings and examples.
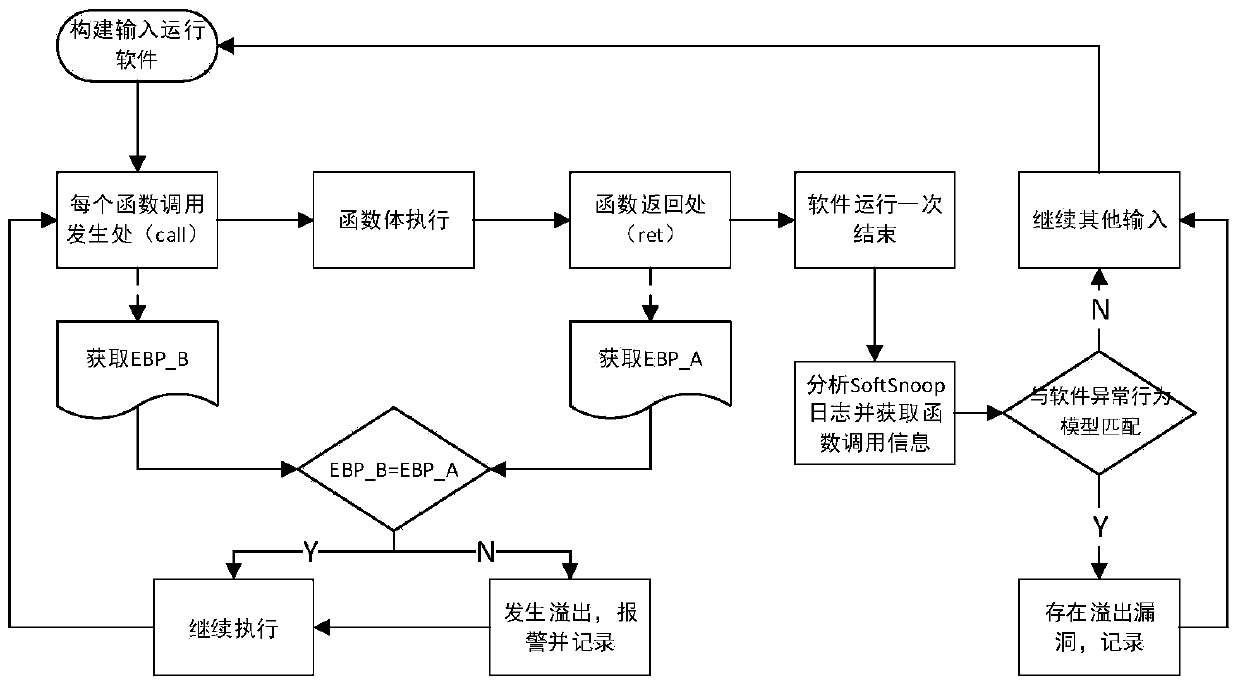
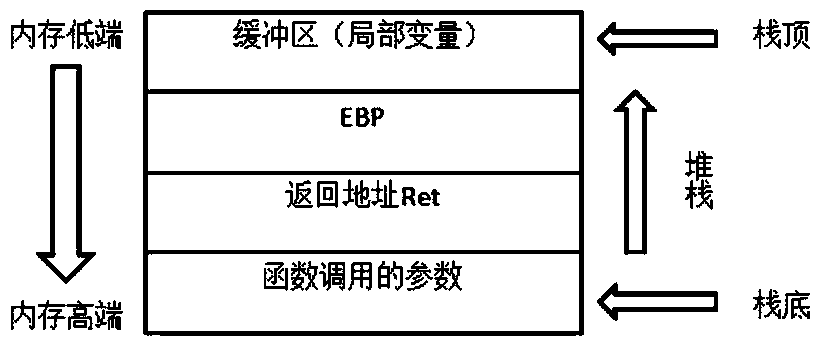
[0032] The object of the present invention is to propose a method for detecting buffer overflow vulnerabilities based on function call sequences in view of the deficiencies in the prior art described above. The basic idea of the present invention is: the stack (or buffer) is closely related to the function call, and when the function call is made, a new local stack related to the function will be generated on the basis of the original process stack to store Variables local to a function; the local stack is destroyed when the function returns. Use the function call as the judgment unit, and use the original EBP value stored in the function stack as the basis for judgment, compare the EBP value when the function call occurs and the EBP value at the end of the function call to judge whether the call has a buffer For overflow, it is judged every time a func...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com