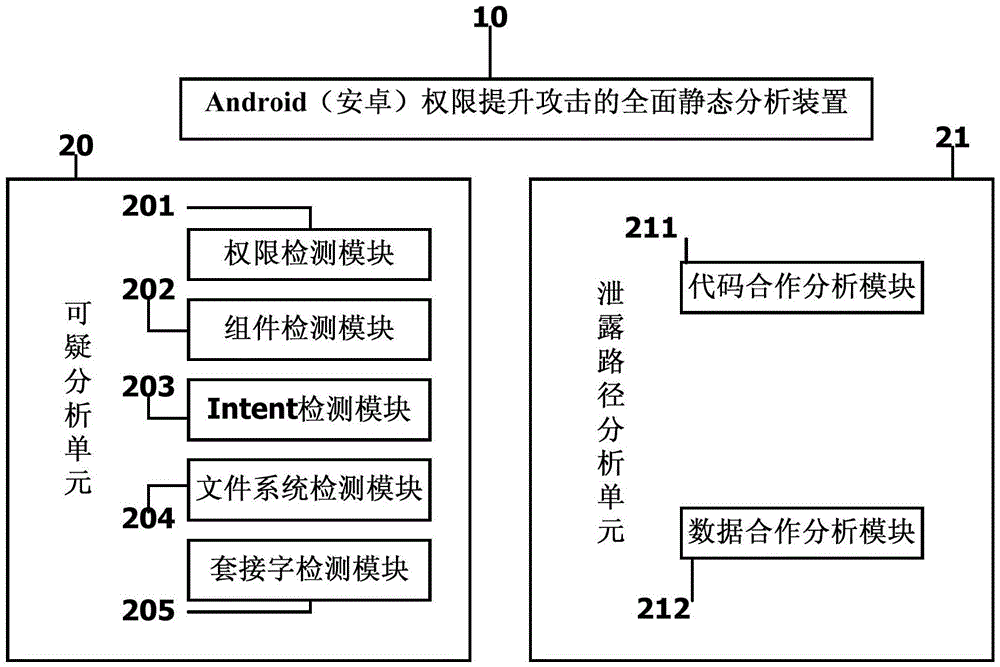
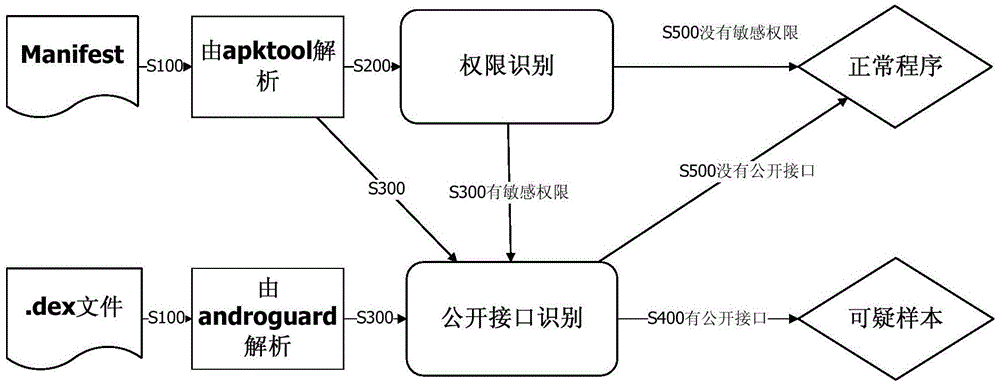
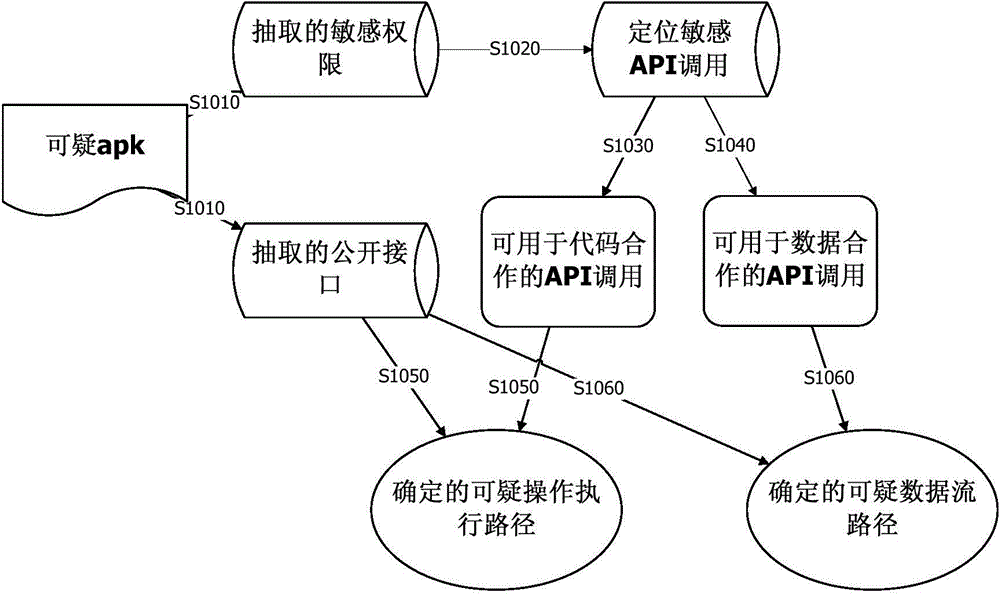
Overall static analysis system for Android authority-escalated attack
A technology of privilege escalation and static analysis, applied in the system field of capability disclosure vulnerabilities, can solve problems such as poor decompilation result obfuscation technology, and achieve the effect of low false negative rate and low false positive.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0076] The present invention selects some representative malicious software and constructs some malicious software variants to test the present invention. The main purpose of the experiment is to evaluate the effectiveness of the present invention in detecting the power leakage problem in privilege escalation attacks. experiment platform:
[0077] Ubuntu 10.04 with 512MB of RAM. The tested malware comes from the Android Malware Genome project.
[0078] The present invention constructs the variants of the following malicious software to evaluate the effectiveness of detecting the power leakage problem in the privilege escalation attack:
[0079] DroidDream, FakePlayer, GamSMS, GPSSMSSpy, etc. In the experiment, although the existing malicious software has the appearance of power leakage, the attack technology of privilege escalation has not been widely accepted. According to the existing results, the present invention finds that only three types of malicious software contai...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com