Virtual machine dispatch algorithm security verification method based on dynamic migration
A technology of scheduling algorithm and verification method, applied in the field of virtual machine and network security, can solve the problems of security threats, threats, lack of implementation methods, etc., to achieve high detection accuracy, promote security improvement, and prevent malicious damage.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
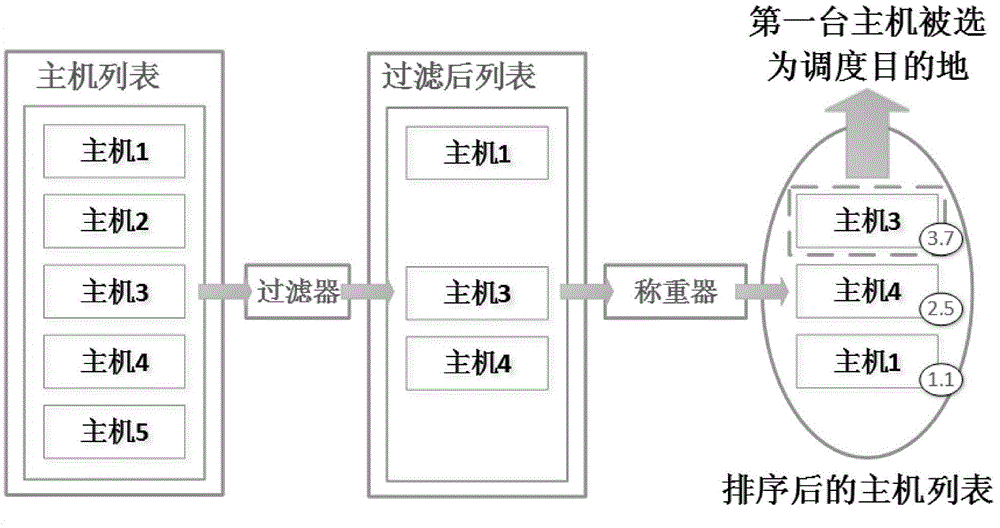
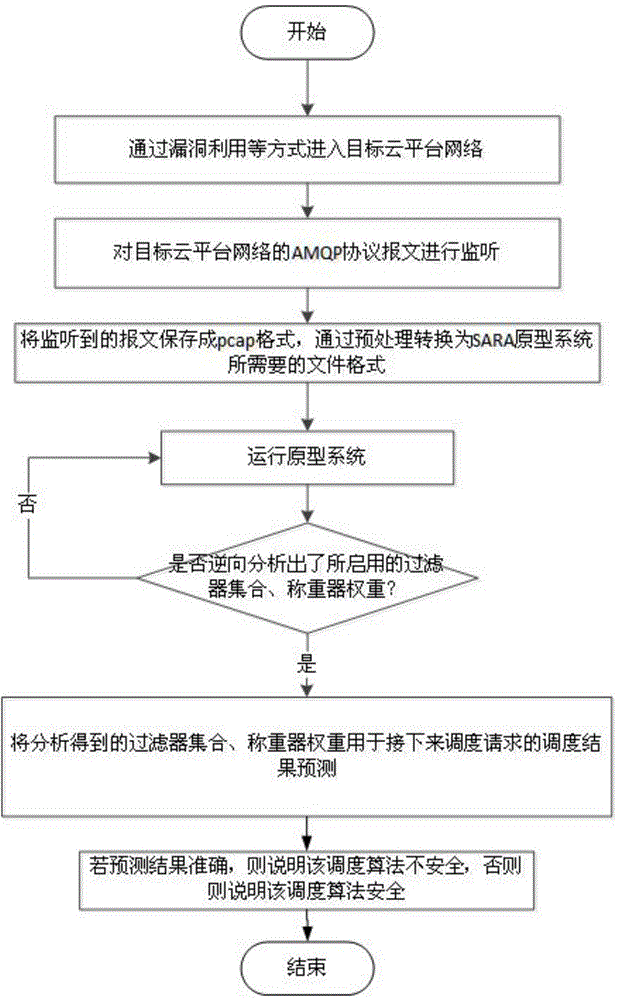
[0054] In actual situations, security researchers need to connect to the internal communication network of the cloud platform through network vulnerability scanning, password brute force cracking, social engineering, etc., and the communication network is the necessary link for the cloud scheduler to issue scheduling instructions . Then use the data packet monitoring software to monitor the data packets sent to the scheduler and the data packets from the scheduler. The format of the data packet is the AMQP protocol, so the monitoring operation can be completed by using the packet interception software Wireshark that supports AMQP protocol analysis. The data packet sent to the scheduler includes 1) real-time basic information of all physical hosts, such as available CPU, available memory resources, etc.; 2) relevant information of each virtual machine scheduling request. The data packets from the scheduler are mainly the scheduling result of the scheduler, that is, the virtual...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com