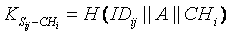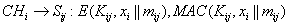A wireless sensor network key distribution method
A wireless sensor and network key technology, which is applied in the field of wireless sensor network key pre-distribution, can solve the problems that common nodes cannot be guaranteed to share keys, and the operation of new nodes is complicated, so as to improve the probability of shared keys and the invulnerability. The effect of improving and reducing storage overhead and computational overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
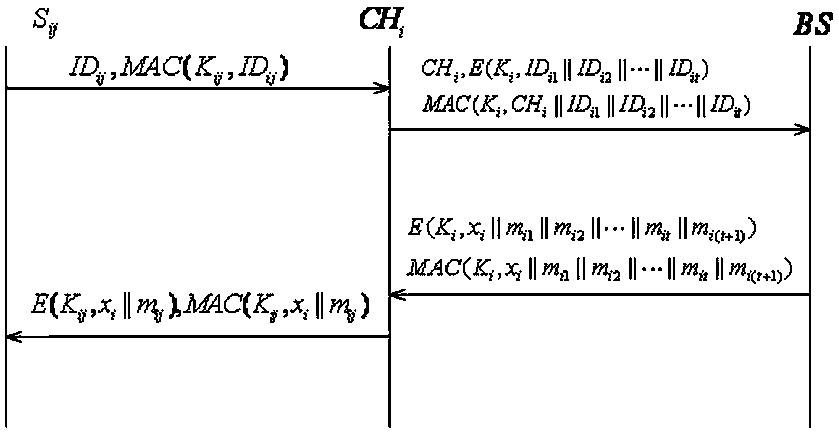
[0037] The invention will be described in further detail below in conjunction with the accompanying drawings.
[0038] In order to enhance the invulnerability of the network, some existing technologies usually assume that the nodes are integrated with tamper-resistant hardware, but this will inevitably increase the cost of the network. In this invention, we use the method of key erasure to improve the security of the network. Suppose the lower limit of time for an attacker to capture a node is , that is, the attacker needs at least The time required to capture a certain node in the network, and once the node is deployed until the key is established, the time required is , and it was proved by experiments that is in line with the actual situation. Therefore, the nodes in the present invention are deployed After the time, some key information stored by the node needs to be erased immediately to prevent the key information from being obtained by the attacker after the n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com