Malicious software network behavior detection method specific to network service provider and system thereof
A network service and malware technology, which is applied in the field of mobile terminal malware detection, can solve problems such as user loss, and achieve the effect of small loss and avoiding lag
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0059] Below in conjunction with accompanying drawing and embodiment the present invention will be further described:
[0060] The malicious software network behavior detection method for network service providers of the present invention includes:
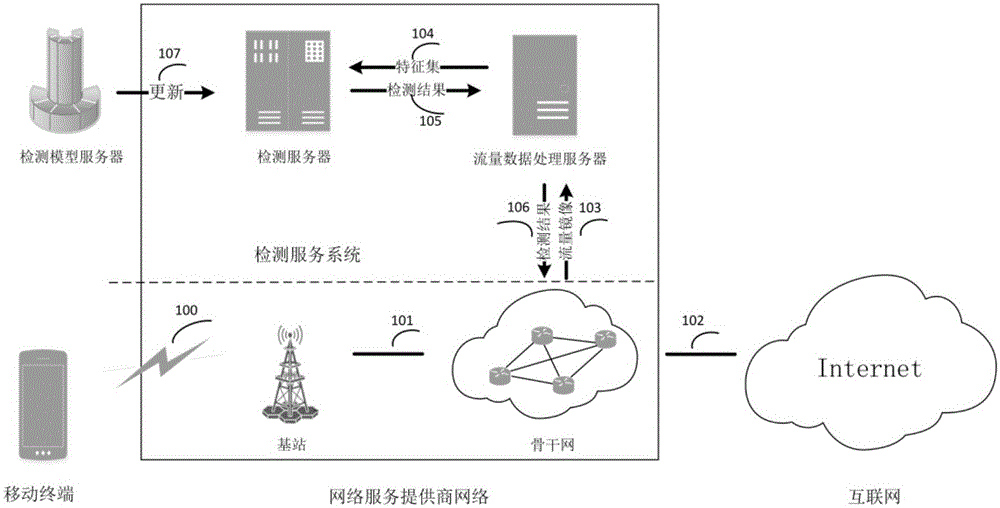
[0061] The mobile terminal of the user is connected to the backbone network of the network service provider through the base station of the network service provider, and the backbone network of the network service provider is connected to the Internet;
[0062] When the user's mobile terminal accesses the Internet, the user's mobile terminal applies to the detection server for authentication;
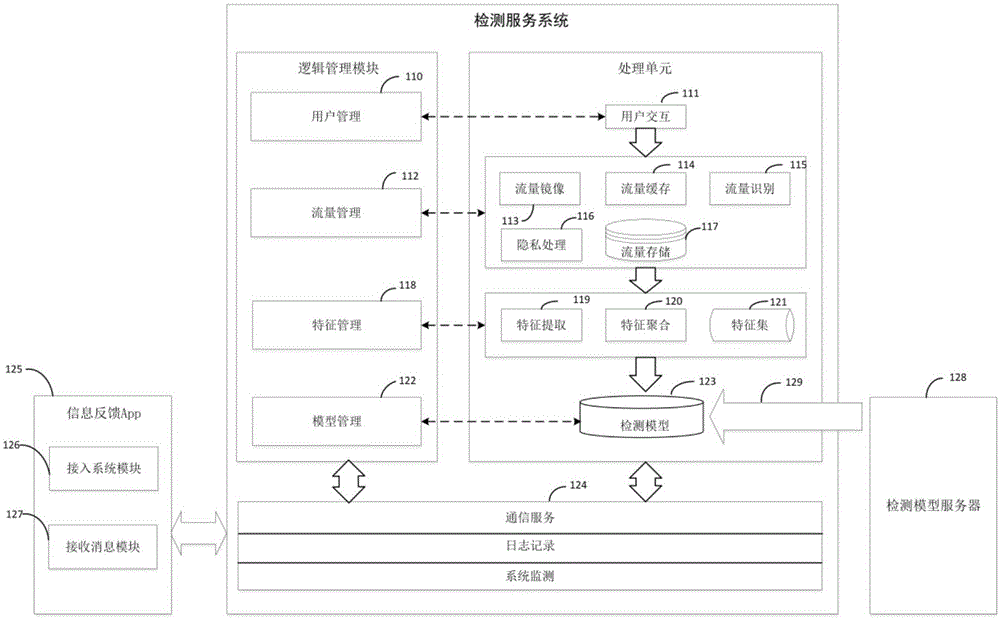
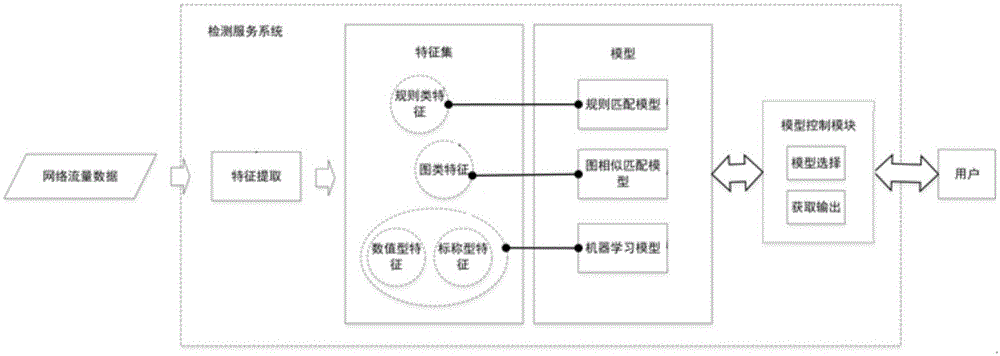
[0063] After authentication processing, collect and cache user mobile terminal network traffic to the traffic data processing server by dynamically assigning traffic mirroring ports, then identify and privacy process the acquired user mobile terminal network traffic, and then extract and aggregate network traffic data features to form Feat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com