IP black hole discovery method based on traffic analysis
A discovery method and traffic analysis technology, applied in the field of network IP traffic analysis, can solve problems such as heavy workload, failure of ping method, failure of ping method, etc., and achieve the effect of low cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
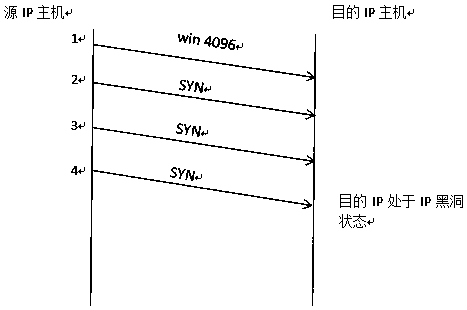
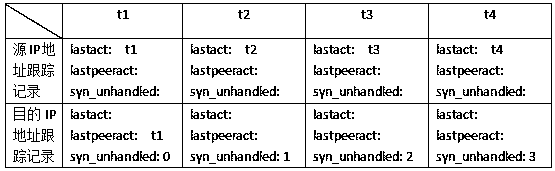
[0030] The main technical basis of the present invention: in the communication process using TCP protocol at the transport layer, before sending data, a connection must be established between the two parties: the requester sends a SYN segment; the server sends back an ACK confirmation The SYN segment is used as a response; the requesting end must send an ACK packet to confirm the SYN segment of the server. The establishment of the connection is completed through these three segments. This process is called a three-way handshake. We can accurately analyze the online activity of each IP host through the statistics of the number of request packets that have not responded to the SYN request message and the analysis of the IP status tracking record, and timely discover those IP hosts that are in a black hole state. , To remind the network administrator to deal with this network failure.
[0031] SYN (synchronous) is the handshake signal used when TCP / IP establishes a connection. Whe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com