Software key function identification method based on complex network fault propagation
A technology of key functions and identification methods, applied in the direction of program control devices, etc., can solve problems such as too simple evaluation criteria, software system collapse, and inappropriate software system dynamic execution process.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
[0038] The concrete example that the embodiment of the present invention is applied is a certain simple embedded program, for ease of use, only listed the statement that only includes sub-function in the program, as image 3 shown.
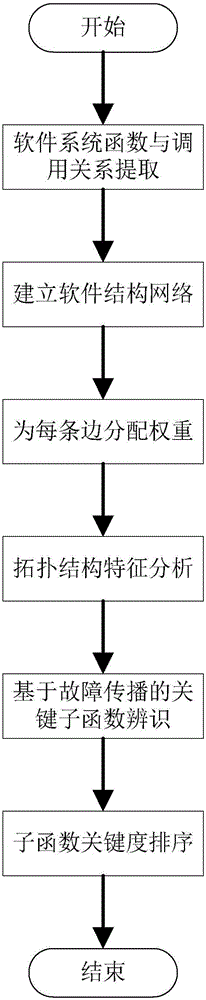
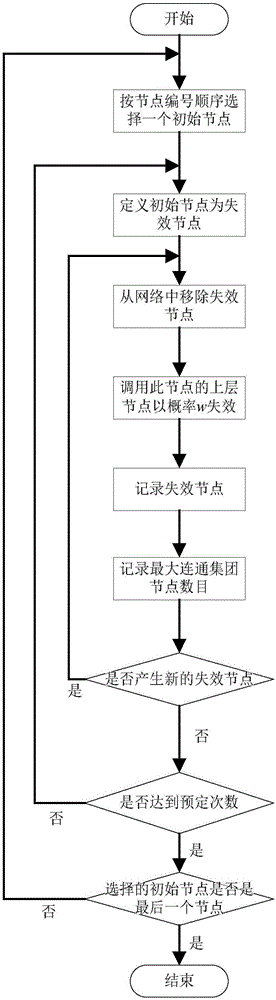
[0039] The software key function identification method based on the complex network of the present invention comprises the following steps:
[0040] Step 1, extract the sub-functions and calling relations of the program according to the source code, and abstract it into a structural network diagram of the software system, such as Figure 4 shown.
[0041] Figure 4 contains 15 nodes and 17 directed edges, where the nodes represent the sub-functions in the embedded software program, and the directed edges represent the calling relationship between the sub-functions, where the function pointed by the arr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com