Method and system for injecting DLL into target process
A target process and target program technology, which is applied in the field of injecting DLL into the target process, can solve the problems of non-dynamic cancellation, anti-virus software interception, heavy workload, etc., and achieve the effect of enhanced level, comprehensive control and high flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment 1
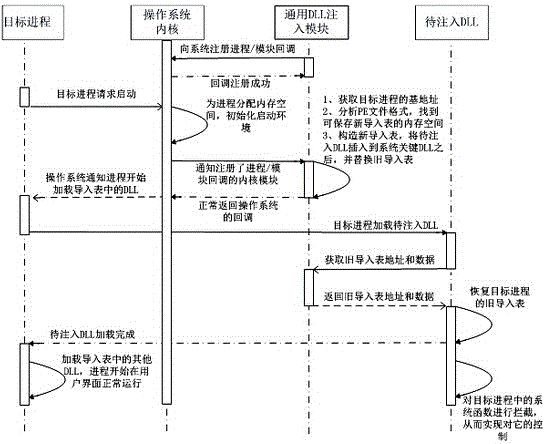
[0040] The system for injecting the DLL into the target process includes: a DLL injection module, which monitors the start request of the target process through the operating system kernel, and injects the target DLL into the target process to respond to the operating system kernel; the target process setting module, which sets the target process to be injected; The system kernel notifies the DLL injection module after receiving the process start request, and waits for the response of the DLL injection module, and notifies the process to start loading the DLL in the import list after receiving the response; the DLL injection module also includes a judgment module, which judges whether the process requested to start is for the target process.
[0041] The method of injecting the DLL into the target process is as follows: the kernel modifies the process PE memory mechanism, and injects the target DLL with the control function into the target process import table. In this way, th...
specific Embodiment 2
[0048] Based on the first embodiment, the system further includes: an old import table recovery module of the target process, which restores the address and data of the old import table after the DLL of the target process is loaded.
[0049] If the startup process is the target process, after the target process finishes loading the DLL in the import table, restore the old import table of the target process. Find a suitable memory space for saving the new import table, construct a new import table to replace the old import table, and restore the old import table after the DLL is injected into the target process, so that the process verification can be fooled and the initial environment of the target process is not Change.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com