Transmission encryption method taking flows as granularity
An encryption method and granular technology, which is applied in the field of transmission encryption with flow as the granularity, can solve the problems of video and text encryption, which does not involve encryption methods, and reduces transmission efficiency, so as to achieve data security, flexible encryption methods, and improved transmission efficiency effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific example
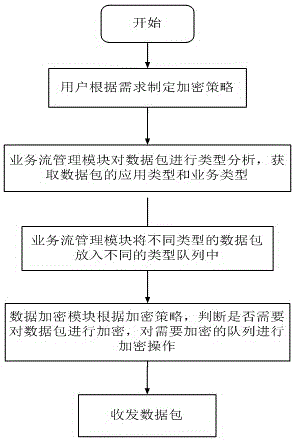
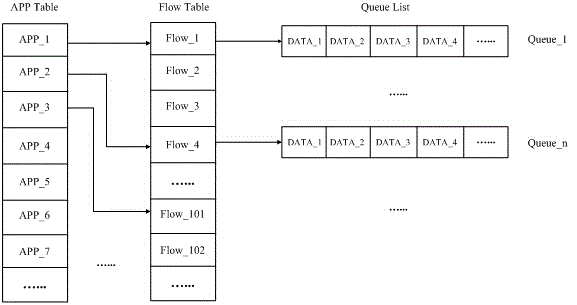
[0036] For example, various Internet devices such as mobile phones and computers are communicating with each other. The application includes multiple video, audio, text, etc. business types. The type identification unit of the business flow management module identifies the type of the application, and the queue maintenance unit will Different data packets are mounted on different data type queues, and then the data encryption module judges whether the business flow type needs to be encrypted according to the encryption strategy set by the user. If necessary, the data packet is encrypted by the data encryption unit, otherwise it is not Required; finally send and receive data packets.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com