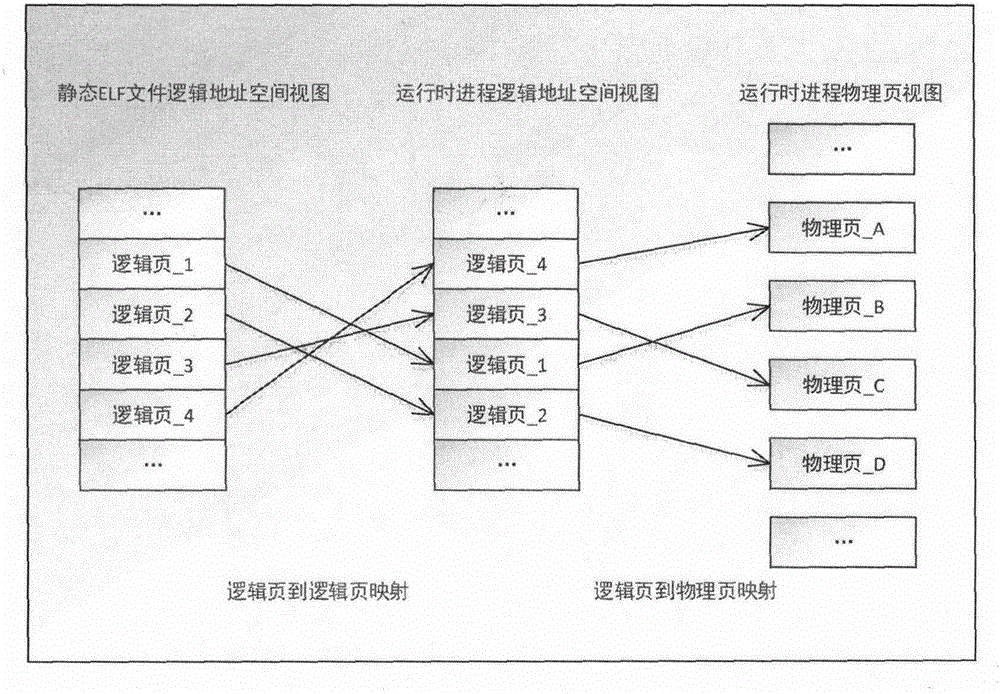
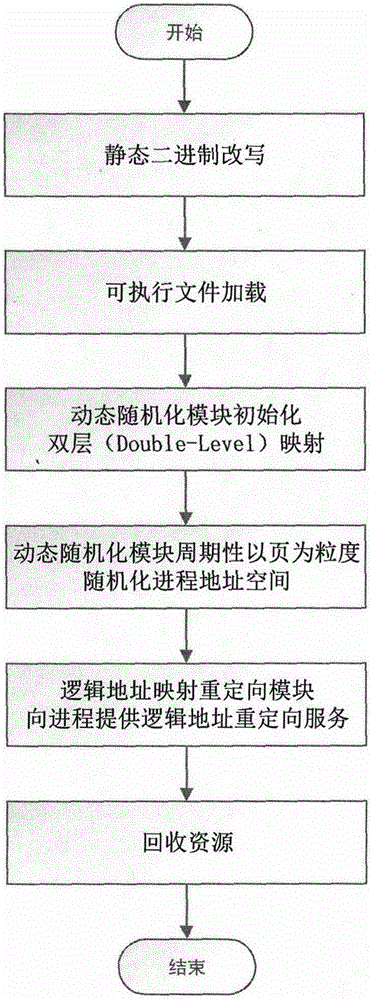
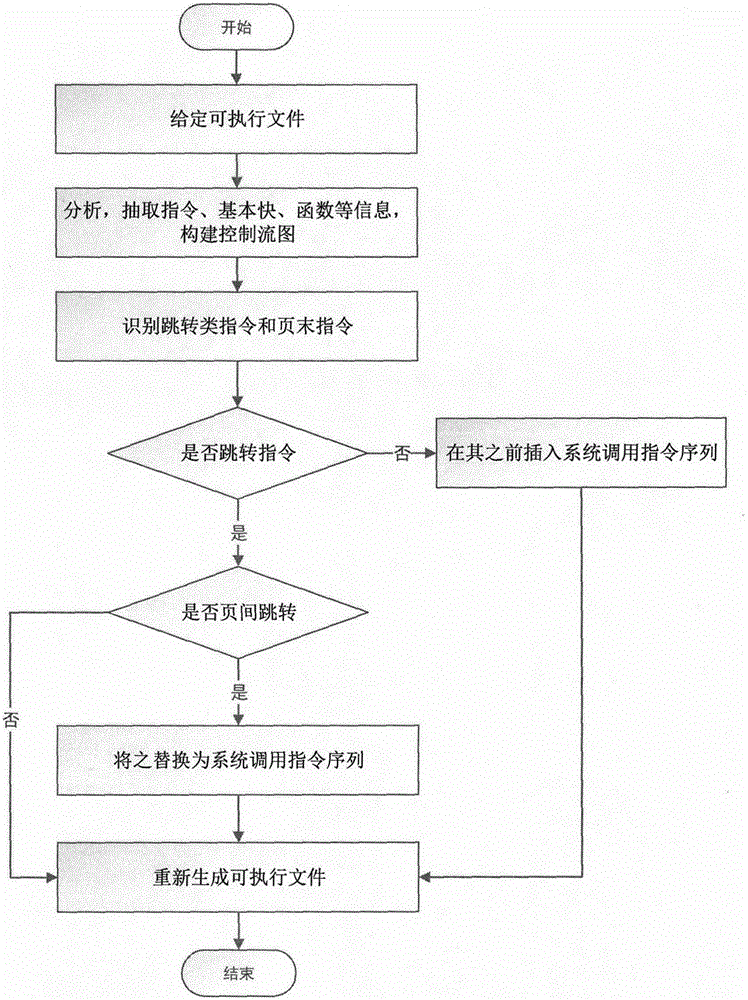
Software security enhancing method based on binary rewrite and dynamic randomization
A dynamic randomization and software security technology, applied in computer security devices, instruments, electronic digital data processing, etc., can solve the problems of inability to defend against information leakage attacks, coarse randomization granularity, etc., to reduce the probability of successful attacks and randomize granularity. Refinement, randomization effect of entropy increase
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment
[0069] Further description will be given below in conjunction with relevant explanatory diagrams and specific embodiments of the present invention: the realization of the software security enhancement method based on binary rewriting and dynamic randomization on the Intel-x86 architecture and Linux system.
[0070] Step 1: Refactor the ELF binary file that requires dynamic randomization into a format suitable for running under the dynamic randomization mechanism by using existing mature binary rewriting tools. In the present invention, the binary rewriting operation mainly relates to the jump instruction and the end-of-page instruction in the code segment of the ELF file; The transfer instruction is replaced by a specific system call instruction sequence, and the corresponding system call instruction sequence is inserted before the end-of-page instruction. Among them, a feasible rewriting rule is as follows (but not limited to this rewriting rule):
[0071]
[0072]
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com