CAPWAP-based shared key using method and device
A technology for sharing keys and keys, applied in secure communication devices and key distribution, can solve problems such as security reduction, and achieve the effects of reducing chip costs, saving storage space, and ensuring secure communication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The technical solutions of the embodiments of the present invention will be clearly and completely described below in conjunction with the accompanying drawings of the present invention.
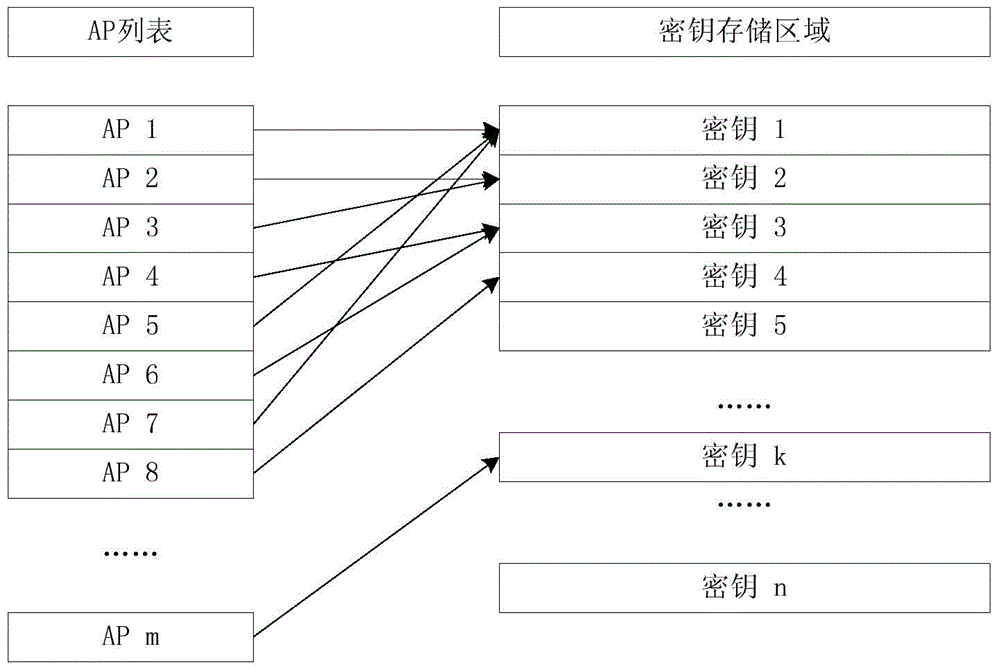
[0023] Such as figure 1 As shown, in the existing technology of dynamically generating DTLS keys through certificates, the keys needed for DTLS encryption and decryption are negotiated by the AP and the AC during the handshake phase of the DTLS session, that is, the key of the AP and the AC Negotiation is decided by steps S101 to S113.
[0024] Specifically, steps S102 and S104 include a 32-byte random number generated by the AC end, steps S101 and S103 include a 32-byte random number generated by the AP end, and step S105 is a digital certificate sent by the AC end to the AP end, On the one hand, it is used for the AP to identify the identity of the AC, and on the other hand, it contains the public key of the AC; in step S108, the AP first randomly generates a 48-byte pre-master key...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com