Active mobile terminal malware network traffic data set acquisition method and system
A malicious software and mobile terminal technology, applied in transmission systems, electrical components, etc., can solve the problems of difficulty in obtaining malicious application traffic data, high storage and computing overhead, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] The present invention is described in detail below in conjunction with accompanying drawing:
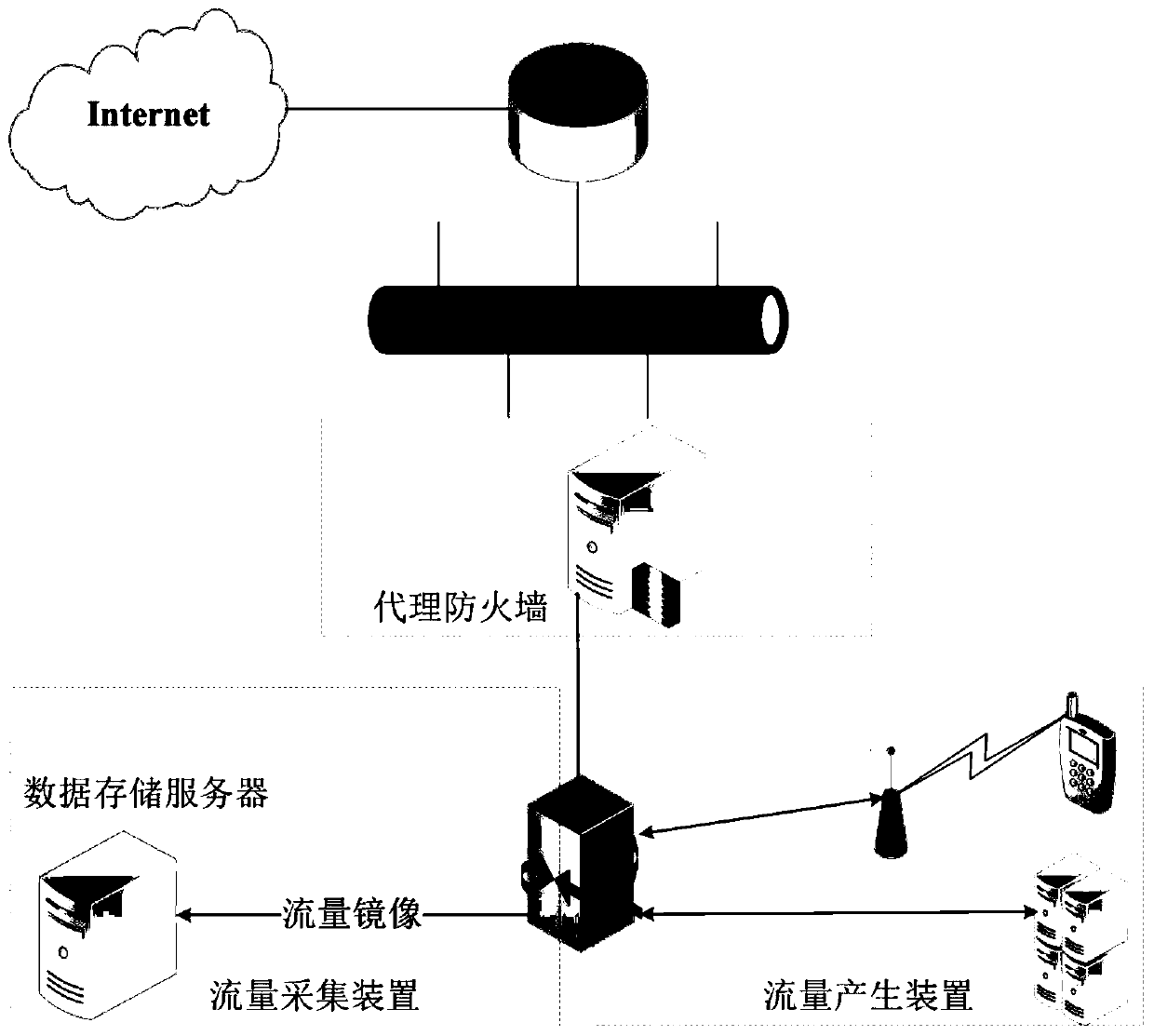
[0044] A kind of active mobile terminal malicious software network traffic data set acquisition method, the following all take the Android system as an embodiment, and the specific working process is:
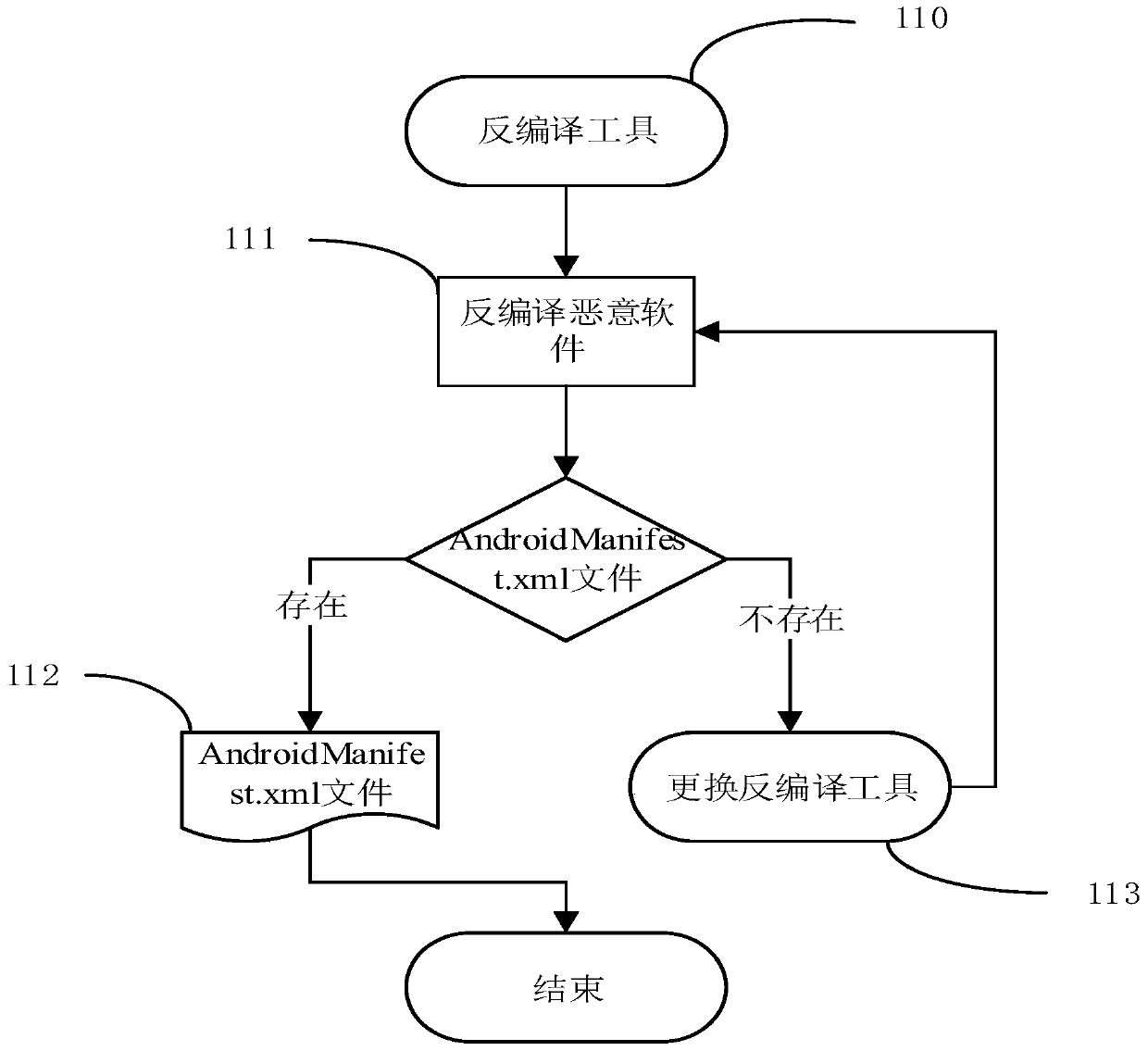
[0045] 1) Decompilation of mobile terminal malware. For the original files of large-scale Android malware, through the automatic script program to control the execution of the decompilation tool APKTool, you can get all the decompiled files of the malware. At the same time, in the decompiled file of each malware sample, there is an Android system configuration file AndroidManifest.xml.
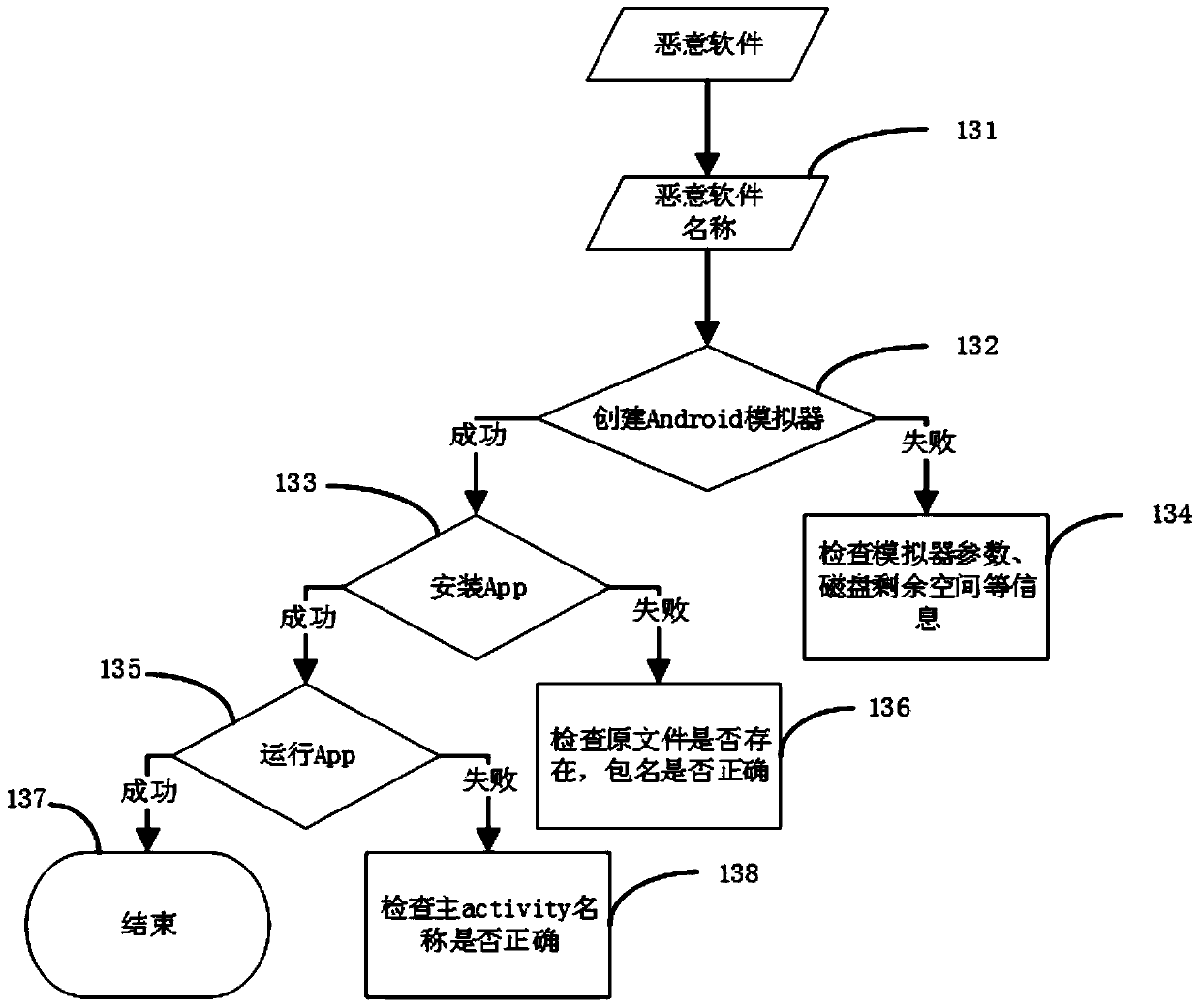
[0046] 2) Extracting the parameters needed for the automatic installation and operation of mobile terminal malware. For every Android malware, if the decompilation is successful, the package name and main activity name of the malware can be extracted from its AndroidManifest.xml file, as the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com