A method of user abnormal behavior detection based on neural network clustering
A neural network and detection method technology, applied in the field of abnormal user behavior detection based on neural network clustering, can solve the problem of high false alarm rate, achieve the effect of improving decomposition speed and signal-to-noise ratio
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
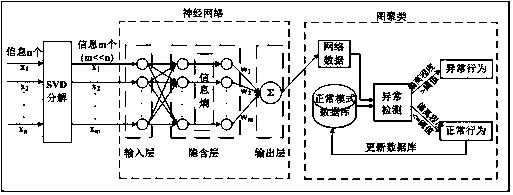
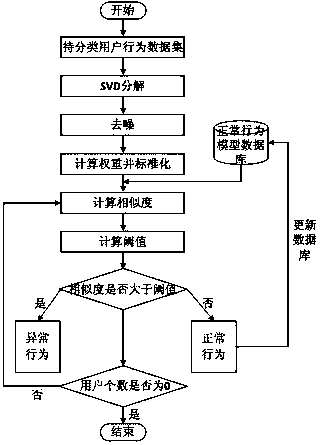
[0031] As shown in the figure, a method for detecting abnormal user behavior based on neural network clustering includes the following steps:
[0032] Step 1. Assuming that each user is an object, the behavior data of the object is used as the attribute of the object, and the matrix real matrix A of n*m dimensions is expressed as an object-attribute structure, and the matrix A is expressed as Among them, X ij Expressed as the j-th attribute of the i-th object; step 2, using the matrix A in step 1 with the formula A=USV T Carry out SVD decomposition, where, U=(u 1 , u 2 ,...,u m ), V=(v 1 ,v 2 ,...,v n ), S=diag(δ 1 ,δ 2 ,...δ r ),δ i >0(i=1,2,...,r), r=rank(A), lambda i 2 (i=1,2,...,r), λ i for A T All the non-zero eigenvalues of A, arranged in descending order, are the singular values of A;
[0033] Step 3. Calculate the order of the effective rank of the decomposed SVD matrix according to the following formulas (1)-(3) to denoise the user behavior infor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com