A Method of Abnormal Traffic Detection
An abnormal flow and abnormal technology, applied in the direction of electrical components, transmission systems, etc., can solve the problems of uncleanness, performance reduction, manslaughter cleaning, etc., to achieve the effect of improving the effect and improving the performance.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
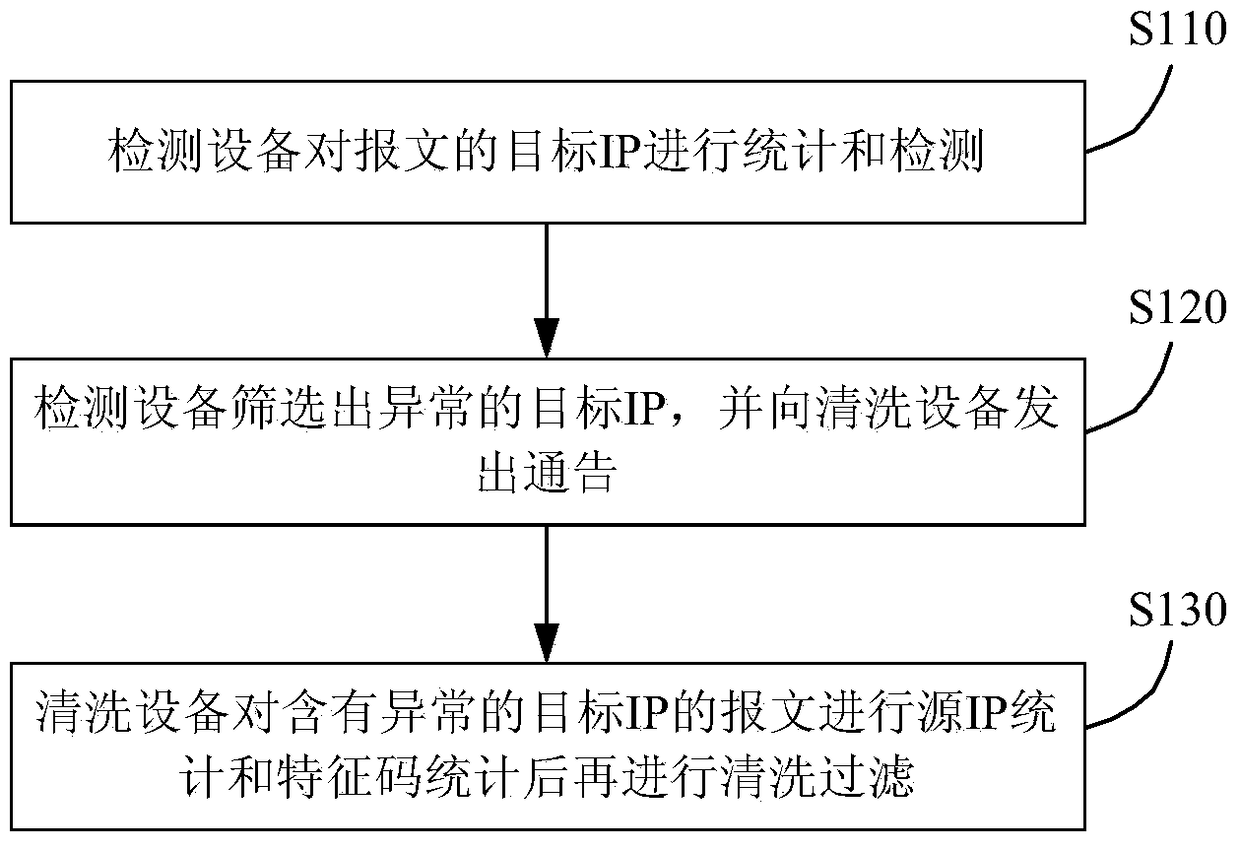
[0018] figure 1 It is a flowchart of a method for detecting abnormal traffic provided in Embodiment 1 of the present invention. The method is suitable for detecting and cleaning abnormal flow in a large flow environment. For example, some operators can use this method to detect and clean the traffic, so as to ensure the normal and stable operation of the network and the normal development of services. The method is executed by a detection device for abnormal flow detection and a cleaning device. The device can be set in the terminal, and can be implemented in the form of software and / or hardware.
[0019] like figure 1 As shown, the method includes:
[0020] S110. The detection device performs statistics and detection on the destination IP of the packet.
[0021] The execution equipment of the abnormal flow detection method includes detection equipment and cleaning equipment. First, the detection device receives the message from the server, and the detection device comple...
Embodiment 2
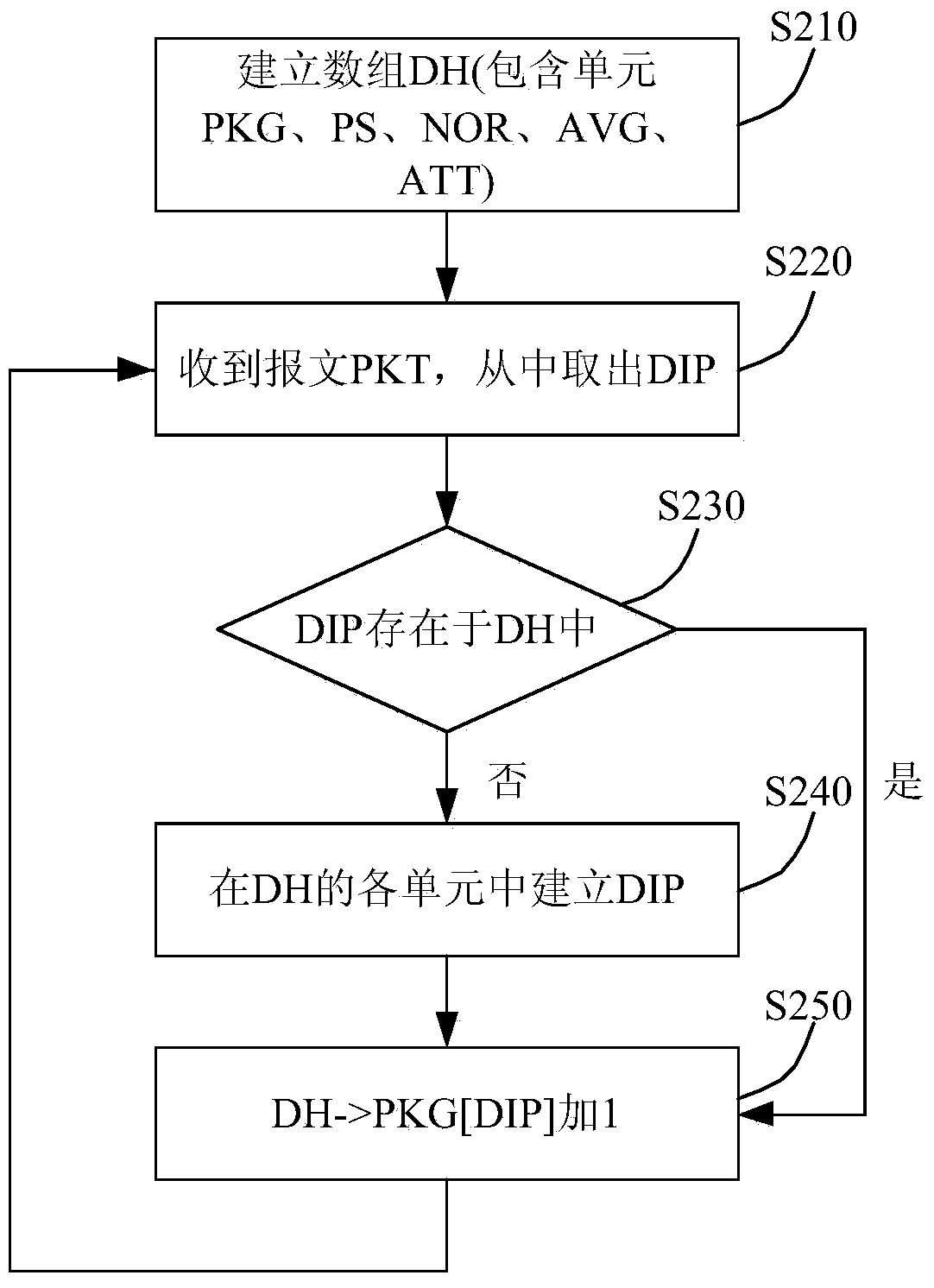
[0046] figure 2 It is a flow chart of a detection device collecting statistics on target IPs provided by Embodiment 2 of the present invention. Based on the first embodiment, this embodiment specifically exemplifies the process of the detection device collecting statistics on the target IP address of the message. like figure 2 shown, including:
[0047] S210. Create an array DH (including units PKG, PS, NOR, AVG, ATT).
[0048] Establish a hash array DH, which contains five subunits: PKG, PS, NOR, AVG and ATT, and then these subunits are a large array, and each position in the array belongs to the corresponding target IP, that is, each target IP has There are corresponding array bits.
[0049] S220. Receive the packet PKT, and extract the DIP from it.
[0050] The PKT contains the information of the target IP, that is, the DIP. When the detection device receives the PKT from the server, it takes out the DIP from it.
[0051] S230. Determine whether the DIP exists in th...
Embodiment 3
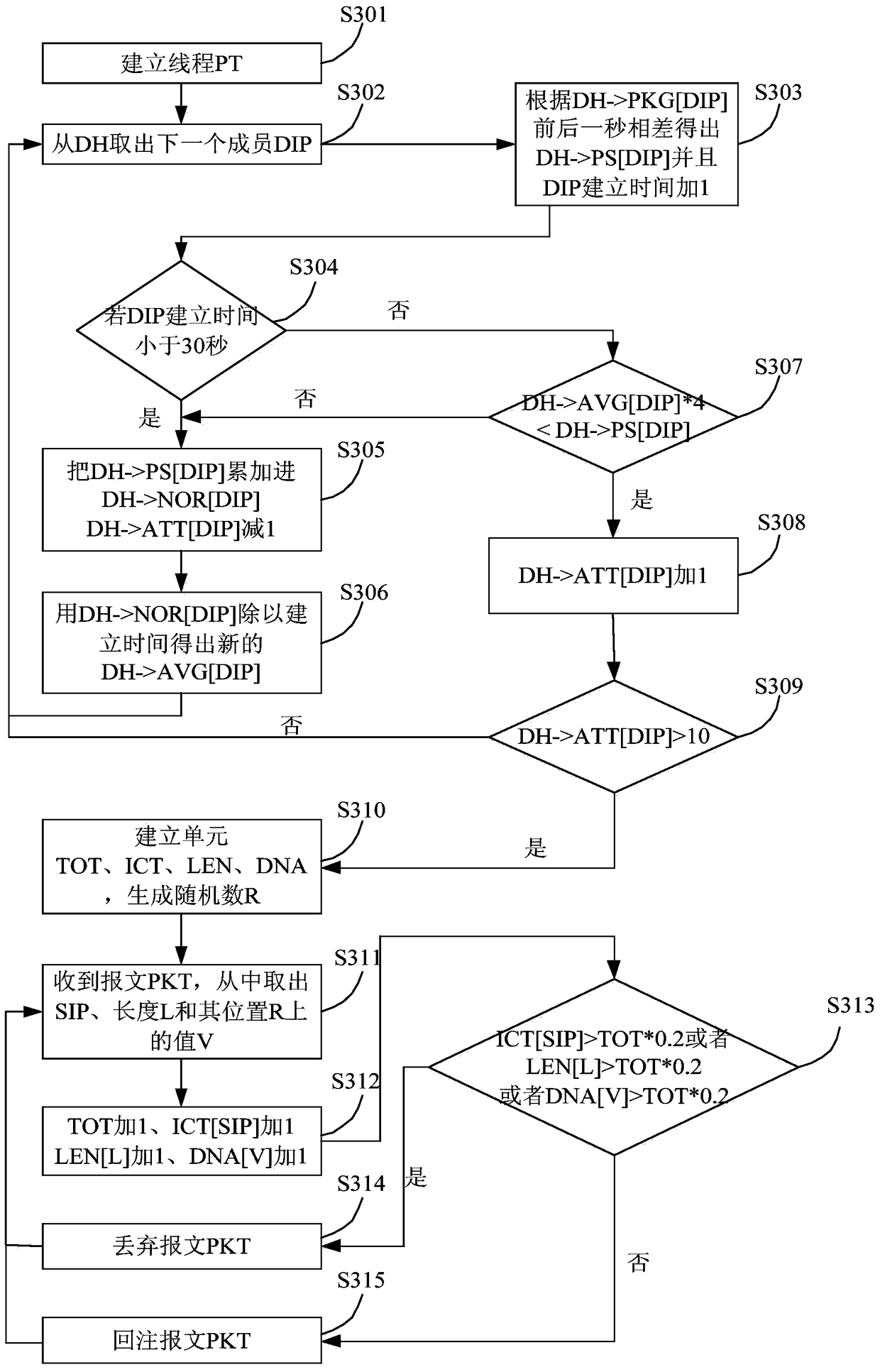
[0058] image 3 It is a specific flowchart of a method for detecting abnormal traffic provided by Embodiment 3 of the present invention. This embodiment is based on the above-mentioned embodiments. The detection device detects the target IP and the cleaning device performs source IP statistics on the abnormal target IP packets notified by the detection device, statistics of signatures and probability statistics of packet length. The whole process is described in detail. like image 3 shown, including:
[0059] S301. Create a thread PT.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com