Access control management method, device and system
A management method and management system technology, applied in the field of access control management methods, devices and systems, can solve problems such as lack of intelligence and inconvenience, and achieve the effect of improving user experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
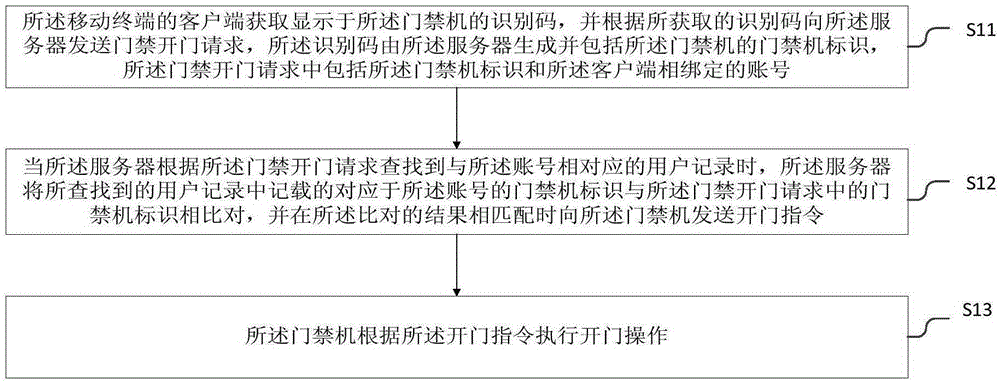
[0027] figure 2 It is a flow chart of the access control management method provided by the first embodiment of the present invention. The access control management method is applied to an access control management system including a mobile terminal, a server and an access control machine. see figure 2, this embodiment mainly describes the method based on the interaction between the mobile terminal, the access control machine and the server. Specifically, the access control management method provided in this embodiment includes the following steps:
[0028] Step S11, the client of the mobile terminal acquires the identification code displayed on the access control machine, and sends an access control opening request to the server according to the acquired identification code, the identification code is generated by the server and includes the The access control machine ID of the access control machine, the access control opening request includes the access control machine ...
no. 2 example
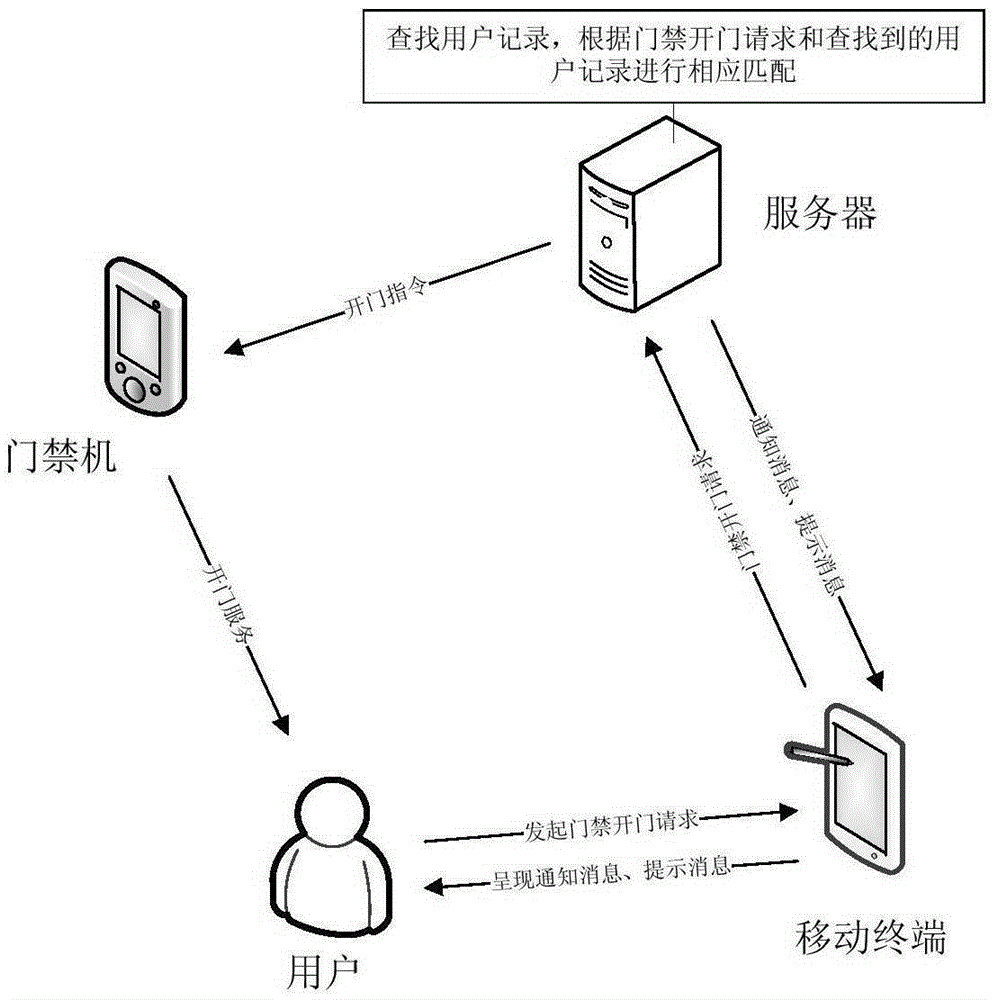
[0052] Figure 8 It is a flow chart of the access control management method provided by the second embodiment of the present invention. see Figure 8 , the present embodiment is an access control management method performed by a server, comprising the following steps:
[0053] Step S21, the server receives the access control door opening request sent by the mobile terminal, and the access control door opening request is generated by the client of the mobile terminal after obtaining the identification code displayed on the access control machine, and the identification code includes the access control machine identification of the access control machine , the access control door opening request includes the access control machine identifier and the account bound to the client;
[0054] Step S22, the server searches for a user record corresponding to the account according to the door opening request;
[0055] Step S23, when the user record corresponding to the account number ...
no. 3 example
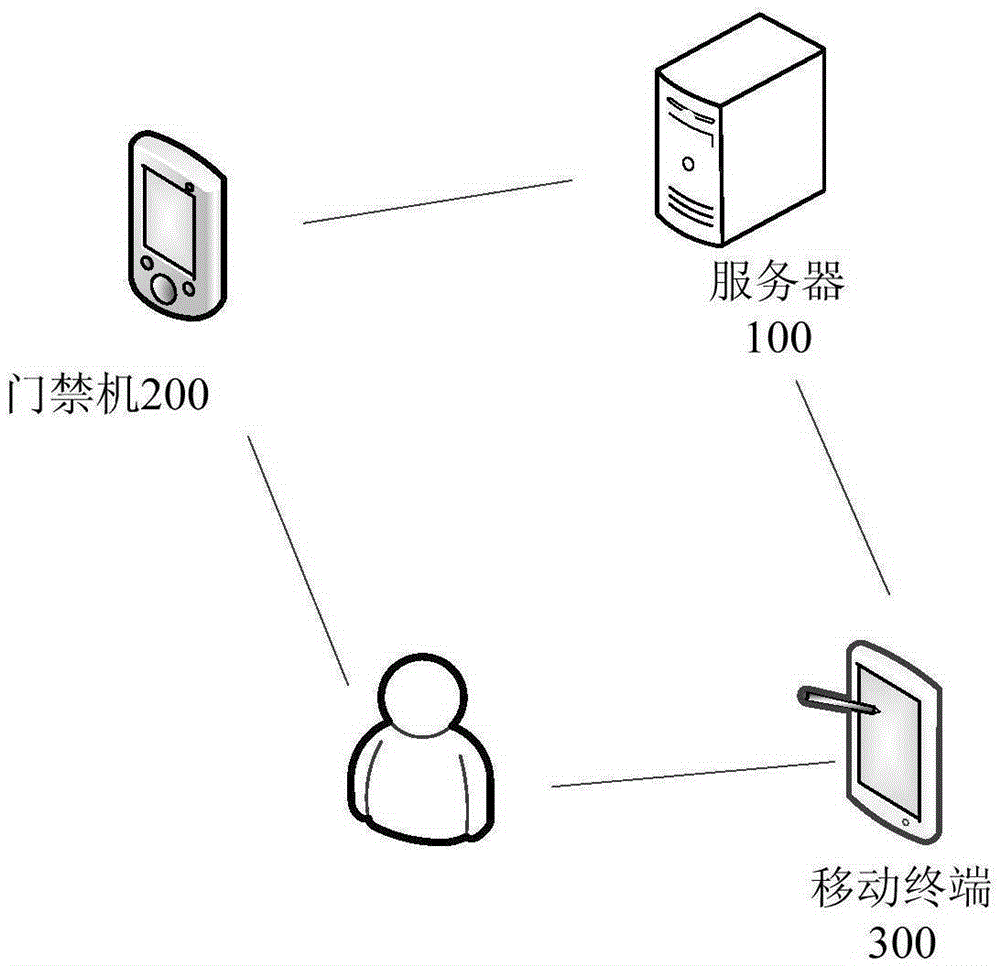
[0060] Figure 9 It is a schematic structural diagram of the access control management system provided by the third embodiment of the present invention. see Figure 9 , the access control management system 300 provided in this embodiment may include a mobile terminal 310 , a server 320 and an access control machine 330 .
[0061] The mobile terminal 310 is used to obtain the identification code displayed on the access control machine 330 through its client terminal, and send a door control opening request to the server 320 according to the obtained identification code, and the identification code is generated by the server 320 It also includes the access control machine identification of the access control machine 330, and the access control opening request includes the access control machine identification and the account bound to the client.
[0062] The server 320 is configured to, when the user record corresponding to the account is found according to the request for ope...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com