Synchronization method for medical LIS system inspection report, and preposed server
A cloud server and reporting technology, applied in the field of medical Internet, can solve the problems that inspection reports cannot be shared, and achieve the effects of saving time and cost, realizing storage and management, and reducing load
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
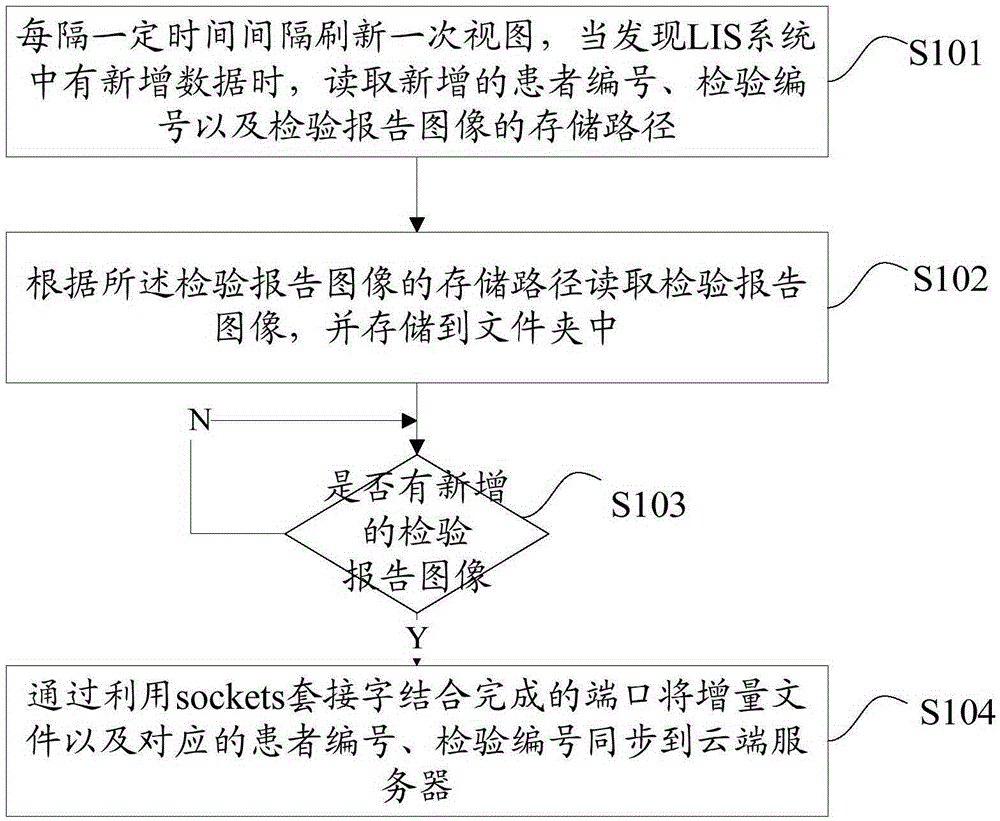
[0027] figure 1 The flowchart of the method for synchronizing the inspection report of the medical LIS system provided by the embodiment of the present invention is shown, and only the parts related to the embodiment of the present invention are shown for convenience of description.
[0028] The method for synchronizing the inspection report of the medical LIS system provided by the present embodiment comprises the following steps:
[0029] Step S101. Refresh the view every certain time interval. When new data is found in the LIS system, read the newly added patient number, test number and storage path of the test report image.
[0030] When the hospital conducts relevant item inspections for patients, a unique inspection number will be generated for each inspection, and each patient has a patient number, such as name, gender, mobile phone number, date of birth, etc. In the LIS system, the image of the inspection report will have a storage path. Assume that the only inspecti...
Embodiment 2
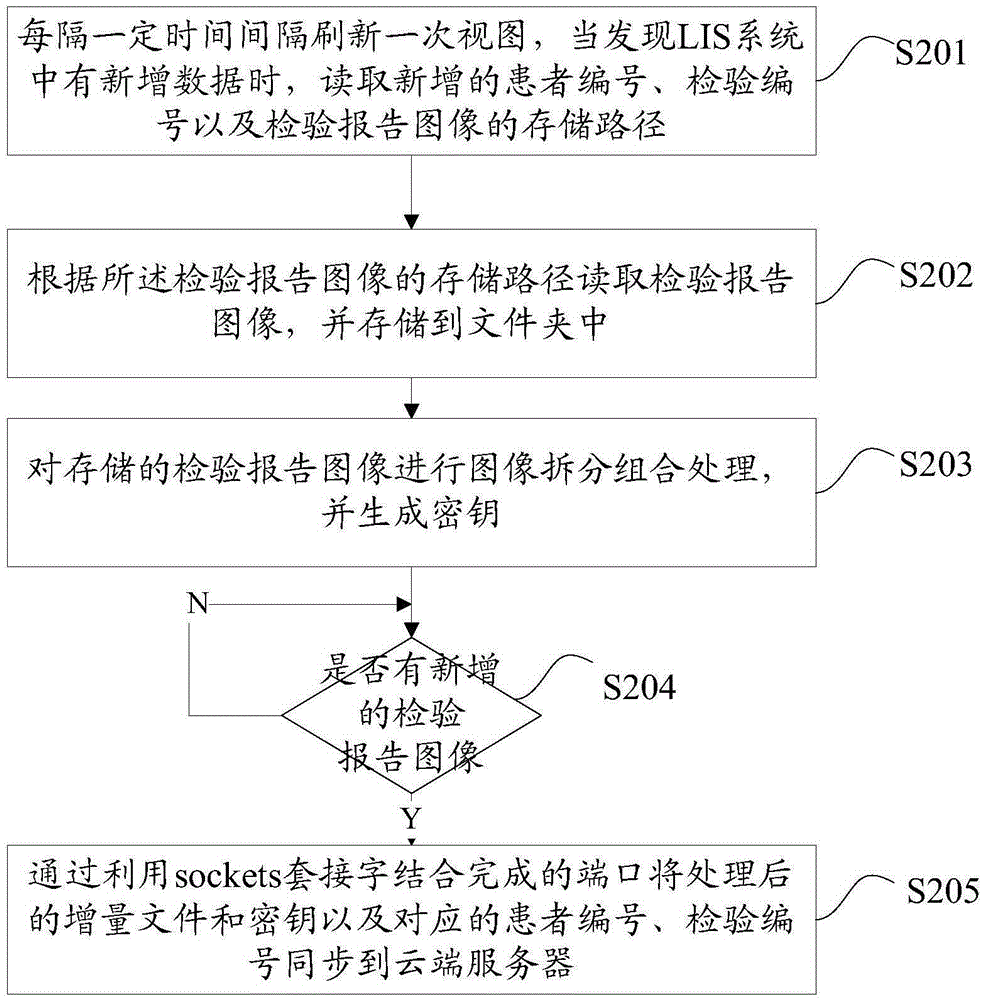
[0040] figure 2 The flowchart of the method for synchronizing the inspection report of the medical LIS system provided by the embodiment of the present invention is shown, and only the parts related to the embodiment of the present invention are shown for convenience of description.
[0041] The method for synchronizing the inspection report of the medical LIS system provided by the present embodiment comprises the following steps:
[0042] Step S201. Refresh the view every certain time interval. When new data is found in the LIS system, read the newly added patient number, test number and storage path of the test report image.
[0043] Step S202, read the inspection report image according to the storage path of the inspection report image, and store it in a folder.
[0044] The above steps S201 and S202 are the same as steps S101 and S102 in the first embodiment, and will not be repeated here.
[0045] Step S203, performing image splitting and combination processing on the...
Embodiment 3
[0066] Figure 6 The structure of the front-end server provided by the embodiment of the present invention is shown, and only the parts related to the embodiment of the present invention are shown for convenience of description.
[0067] The front-end servers provided in this embodiment include:
[0068] The data refresh unit 71 is used to refresh the view every certain time interval, and read the storage path of the newly added patient number, test number and test report image when new data is found in the LIS system;
[0069] A file storage unit 72, configured to read the inspection report image according to the storage path of the inspection report image, and store it in a folder;
[0070] The scanning judging unit 73 is used to scan once every preset time whether there is a new inspection report image, that is, an incremental file;
[0071] The data synchronization unit 74 is used for synchronizing the incremental file and the corresponding patient number and inspection ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com