A detection method and device for legitimate memory access
A memory access and detection method technology, applied in the field of computer programs, can solve the problems of low detection performance and low performance of instrumentation memory detection tools, and achieve the effect of improving detection efficiency and software performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
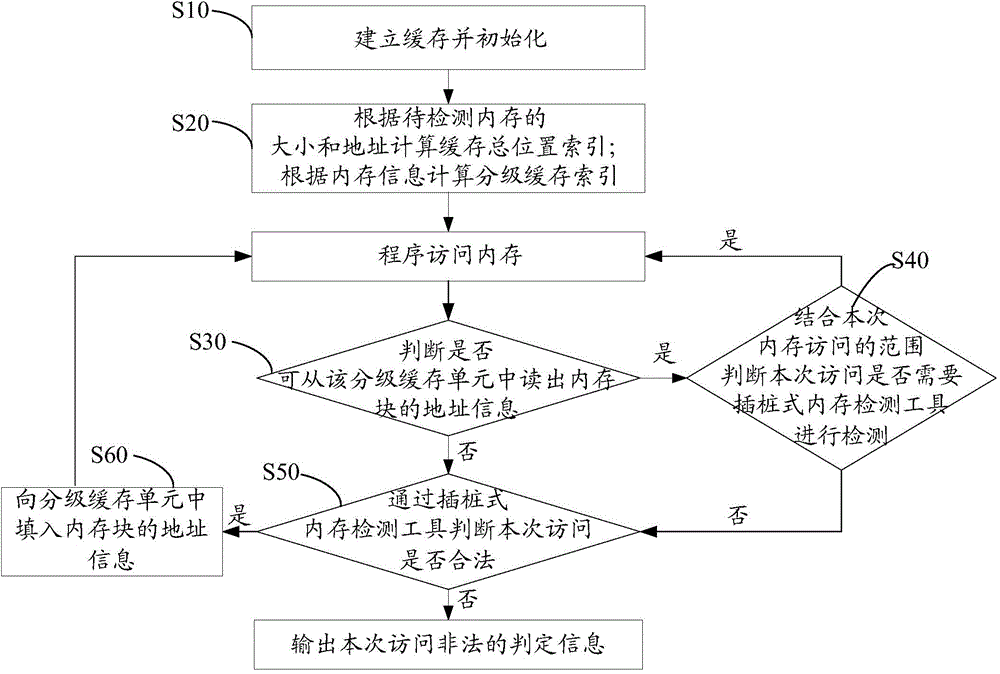
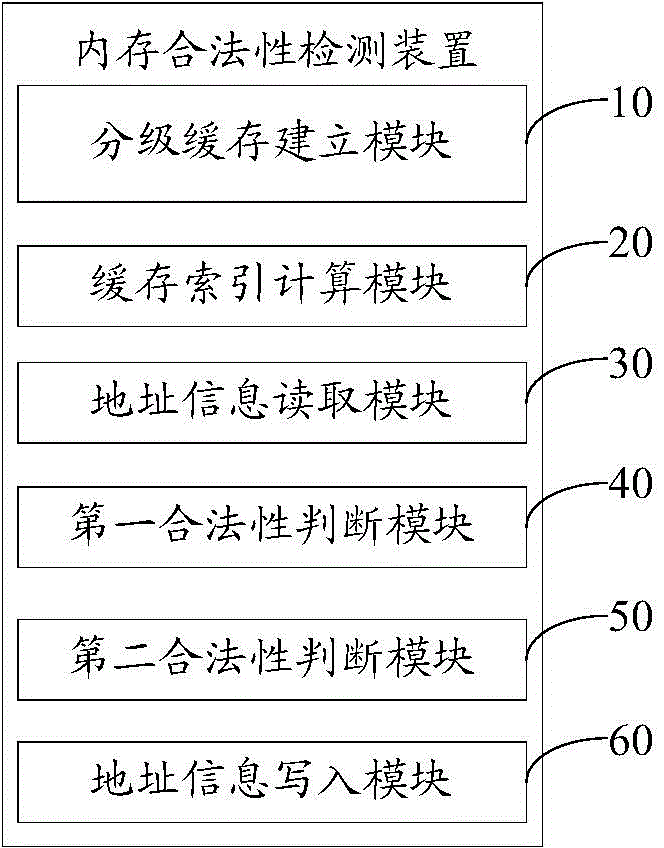
[0045] The present invention provides a detection method for legal memory access, referring to figure 1 , in an embodiment of the present invention, the legal memory access detection method at least includes the following steps:
[0046] S10, establish and initialize the cache; for example, according to the statistical data of general software memory usage, a 7-level cache can be established, each level of cache has 65536 units, and the corresponding sizes are 1~8, 9~128, 129~1K, 1k respectively Above ~ 8K, above 8k ~ 64K, above 64k ~ 1M and memory blocks above 1M bytes.
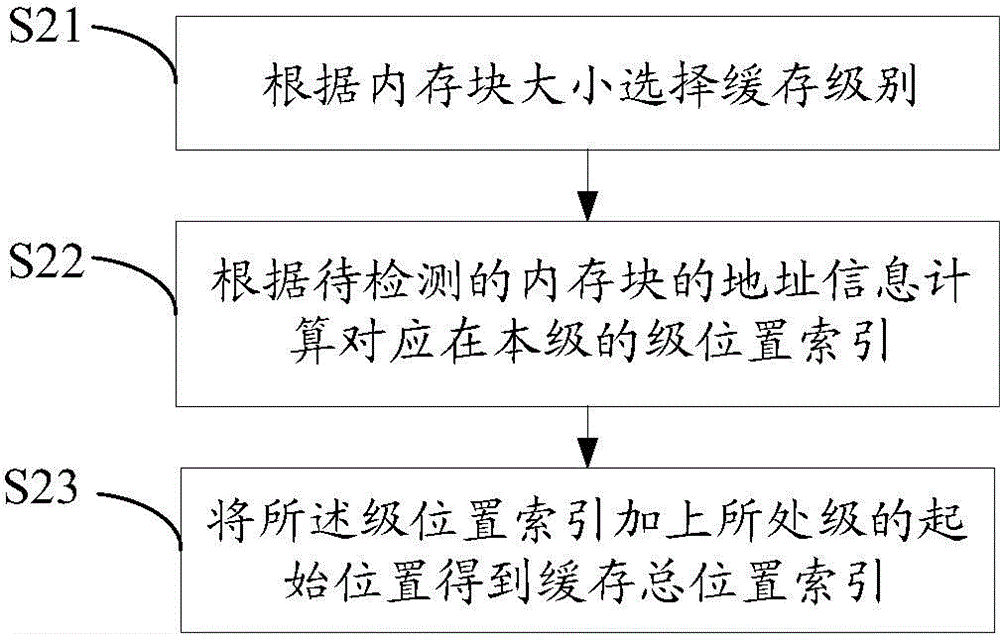
[0047] S20, calculate the total location index of the cache according to the size and address of the memory block to be detected; calculate the hierarchical cache index according to the memory information; for example, firstly, the cache level can ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com