Multiple image encryption method based on pwlcm chaos
An encryption method and image technology, applied in the direction of image communication, electrical components, etc., can solve problems such as low efficiency, and achieve the effects of high security, small amount of calculation, and strong key sensitivity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] Embodiments of the present invention will be further described in detail below in conjunction with specific drawings and examples.
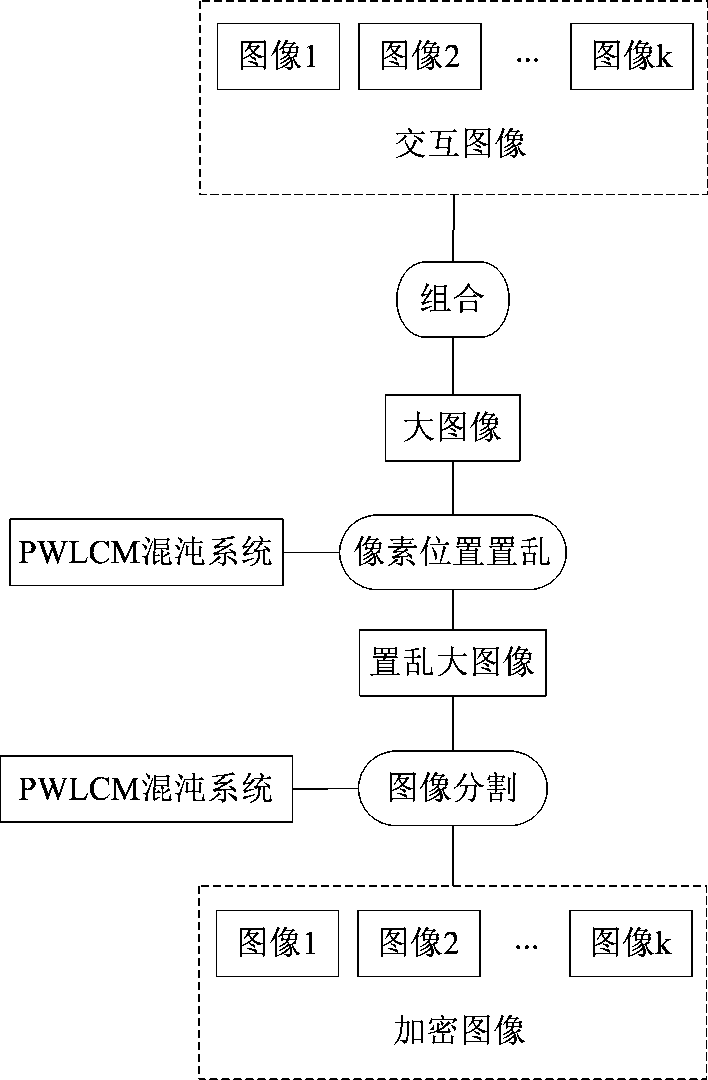
[0032] Encryption flowchart of multiple image encryption method based on PWLCM chaos, such as figure 1 shown.
[0033] The programming software used is Matlab 7.0, select figure 2 The nine gray images of the same size of 512×512 are the experimental objects. Using the multiple image encryption method based on PWLCM chaos, the specific process of encrypting nine interactive images is as follows:
[0034] 1. To encrypt 9 gray interactive images of the same size of 512×512, that is, I 1 , I 2 ,..., I 9 , the sender Alice converts 9 interactive images into a large image in a certain order, which can be expressed as
[0035]
[0036] Such as image 3 shown.
[0037] 2. Randomly select x 0 = 0.28153489126924 and p 1 = 0.44537834013456 respectively as the initial value and control parameters of the PWLCM chaotic system, using the ch...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com