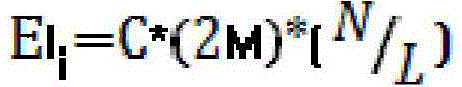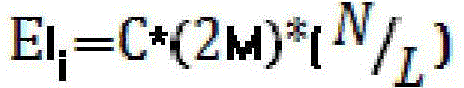Implementation method of fault-tolerant distributed security event data transmission protocol
A data transmission protocol and technology for security events, applied in the field of distributed processing and data transmission of massive security events, and can solve problems such as difficulty in use and poor scalability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] The present invention provides a method for implementing a fault-tolerant distributed security event data transmission protocol, including the following steps:
[0037] A. For the security events of the whole network, the event processing distributed cluster method is adopted: each node of the distributed cluster is called a Performer, and each Performer node is an independent physical server or virtual machine with comparable computing performance. Each Performer node establishes a message queue ML (MessageList), which is a first-in-first-out array;
[0038] B. The event processing cluster regularly elects a transactional node called Transactional, and the transactional node Transactional is responsible for fault-tolerant processing of the cluster. In addition to the functions of a general Performer node, the transactional node Transactional also builds a transactional message mapping table TMM (TransactionalMessageMap ), the mapping table backs up unprocessed messages...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com