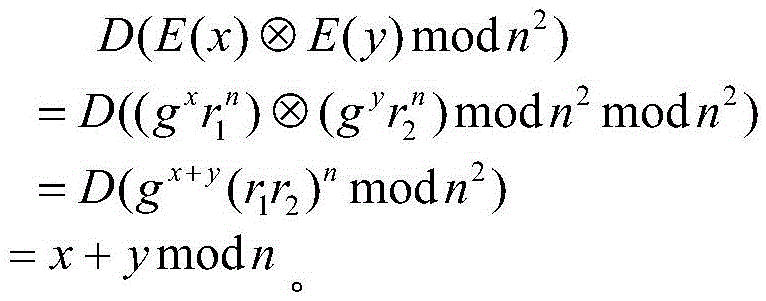Homomorphic key generating-sharing method and device
A key generation and homomorphic technology, applied in secure communication devices and key distribution, can solve the problems of key leakage, inability to monitor keys, and inability to control the number or time of reading by the shared person, to prevent ciphertext leakage, The effect of sharing safe and efficient, safe and efficient ciphertext sharing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
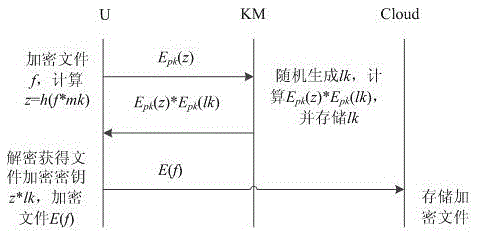
[0056] Implementation Mode 1: The homomorphic key generation process is as follows:
[0057] Step 1: User U multiplies his master key mk with the file name, and then obtains a string z through a hash function, uses his own homomorphic key to synthesize public key pk to encrypt z, and generates Epk(z), And send its corresponding file name to the key management center KM;
[0058] Step 2: The key management center KM gets the Epk(z) sent by the user, selects a random number lk, encrypts it with the user's public key to generate Epk(lk), calculates Epk(z)*Epk(lk), and sends it to the user , simultaneously storing said lk and the file name described in step 1 correspondingly;
[0059] Step 3: The user U obtains the file encryption key key=z*lk by decrypting the homomorphic synthetic private key sk, and then the user encrypts the file with the encryption key to obtain the encrypted ciphertext;
[0060] Further, the encrypted ciphertext is stored locally by the user or the user se...
Embodiment approach 2
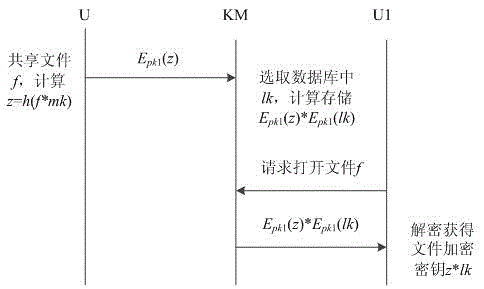
[0062] Embodiment 2: The key sharing process specifically includes:
[0063] This protocol mainly realizes the safe sharing of keys among different users and the control and monitoring of keys by the key management center. Before key sharing, a key must be generated through a key generation protocol, and then it can be shared with other users. Suppose user U wants to share his file f with user U1.
[0064] Protocol description:
[0065] Step 1: User U multiplies his master key mk with the file name, and then obtains the string z through the hash function. User U encrypts z with the homomorphic synthesis public key pk1 of other user U1, and generates Epk1(z ), and send Epk1(z) and the corresponding file name to the key management center, and notify the key management center to share the file with other users U1;
[0066] Step 2: The key management center KM obtains the Epk1(z) sent by the user U and the corresponding file name, and queries the corresponding lk according to t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com