Digital resource copyright protection method, opening method and device, and hardware storage device
A technology of digital resources and storage devices, applied in the direction of electronic digital data processing, computer security devices, program/content distribution protection, etc., can solve the problems of consumption, long time, etc., to reduce production costs, reduce the time consumed by binding, The decryption method is simple and convenient
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
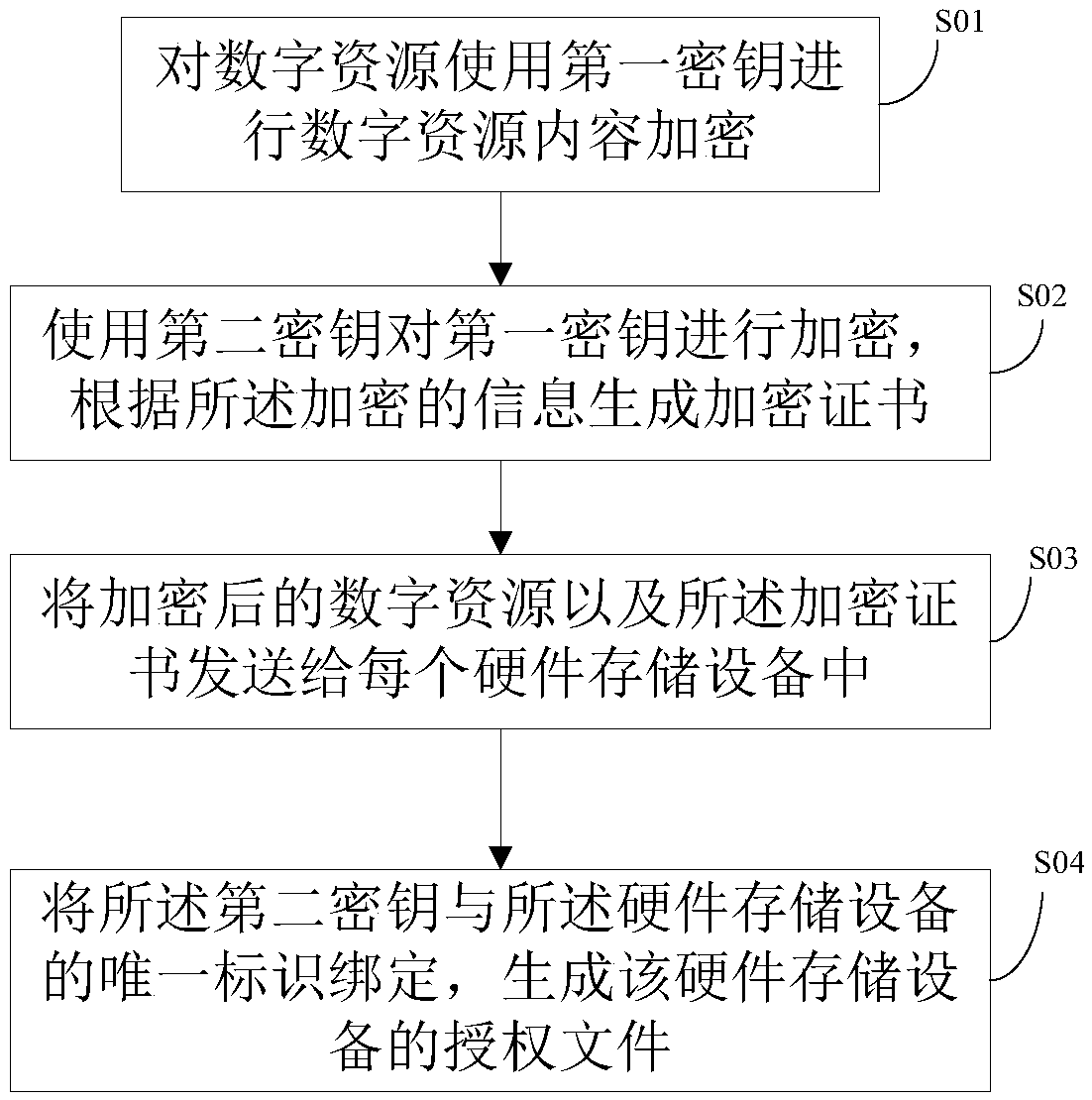
[0048] This embodiment provides a digital resource copyright protection method, which can be used in the copyright protection of massive digital resources based on hardware storage devices, the method flow chart is as follows figure 1 shown, including the following steps:
[0049] S01. Use the first key to encrypt the content of the digital resource on the digital resource. Here is the copyright protection encryption performed on the content of the digital resource, for example, the first key is key A, and the encryption method is DRM encryption.
[0050] S02. Use the second key to encrypt the first key, and generate an encryption certificate according to the encrypted information.
[0051] When mass-producing digital resources, such as when a batch of e-books is to be authorized in batches to several mobile phones, the above-mentioned key A is encrypted twice at this time, and the second key here is key B. When resources are authorized in batches, key B is selected to encry...
Embodiment 2
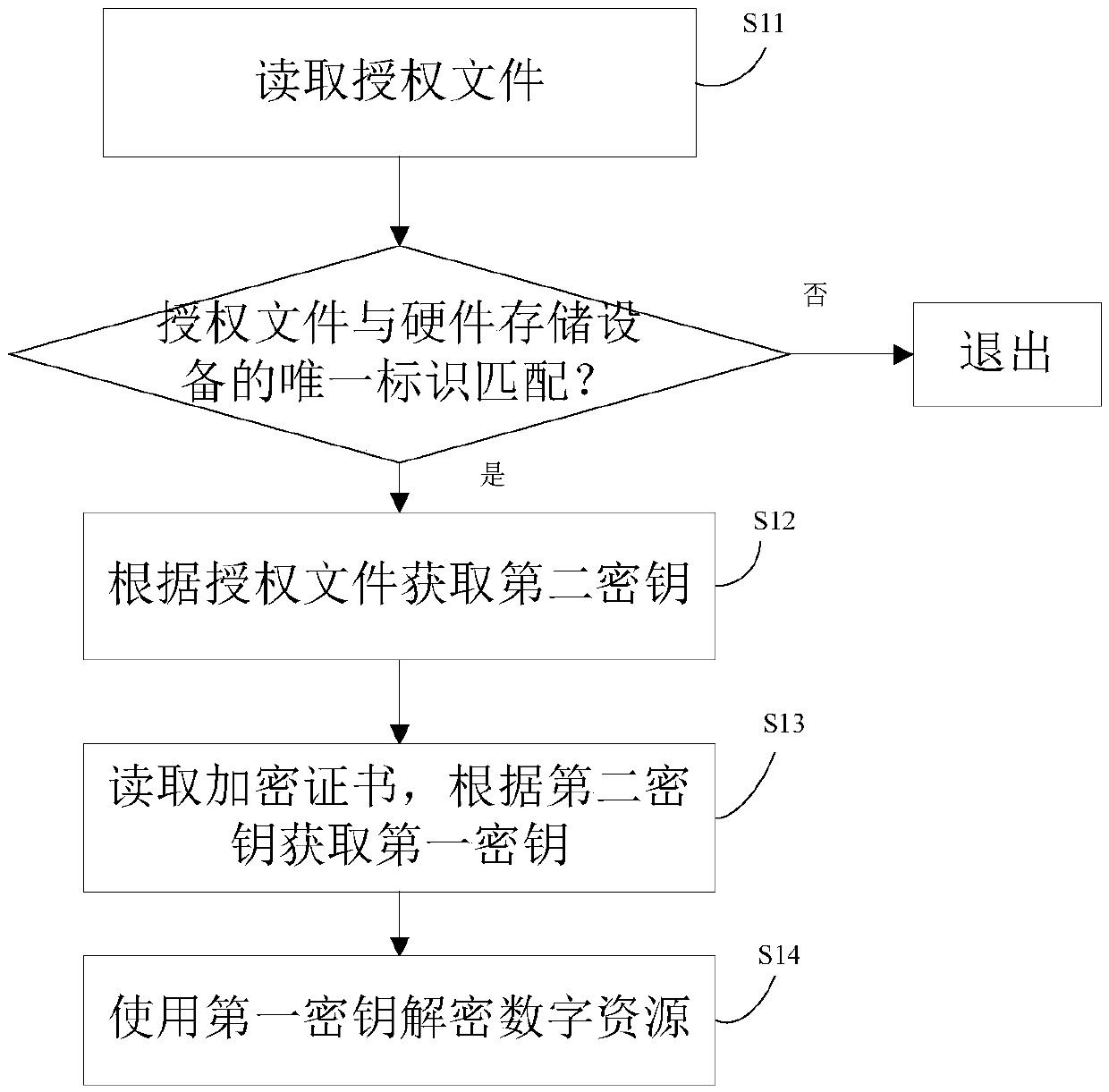
[0058] This embodiment provides a method for opening a copyright-protected digital resource, which can be used to open a digital resource mass-produced using the method in Embodiment 1 on a hardware storage device. The flow chart of the method is as follows figure 2 shown, including the following steps
[0059] S11. Read the authorization file, and judge whether the authorization file matches the unique identifier of the current hardware storage device. When matching, execute step S12, and exit the program directly if not matching, or prompt that the reason for exiting is not matching.
[0060] When accessing copyright-protected digital resources on the hardware storage device, start the copyright protection program, read the authorization file first, and enter the next step when the authorization file matches the unique identifier of the current hardware storage device.
[0061] S12. When the authorization file matches the unique identifier of the current hardware storage d...
Embodiment 3
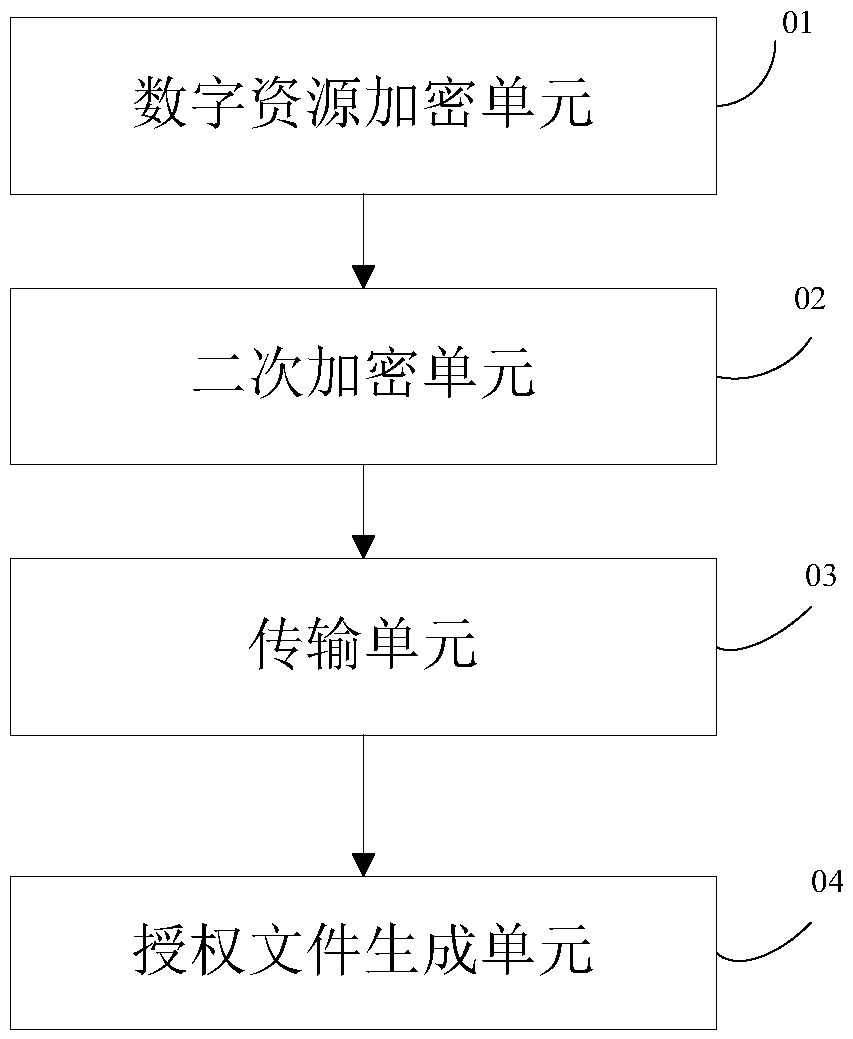
[0068] This embodiment provides a digital resource copyright protection device, the structural block diagram is as follows image 3 shown, including:
[0069] The digital resource encryption unit 01 is used to encrypt the content of the digital resource using the first key for the digital resource;
[0070] The secondary encryption unit 02 is configured to use the second key to encrypt the first key, and generate an encryption certificate according to the encrypted information;
[0071] A transmission unit 03, configured to send the encrypted digital resource and the encryption certificate to each hardware storage device;
[0072] An authorization file generation unit 04, configured to bind the second key with the unique identifier of the hardware storage device, and generate an authorization file for the hardware storage device.
[0073] Wherein, the digital resource encryption unit adopts DRM encryption.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com