Help seeking method based on fingerprint identification
A fingerprint identification and fingerprint technology, applied in the field of communication, can solve the problems of malicious operation, inconvenient operation, cumbersome steps, etc., and achieve the effect of ensuring safety, facilitating rescue, improving efficiency and possibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
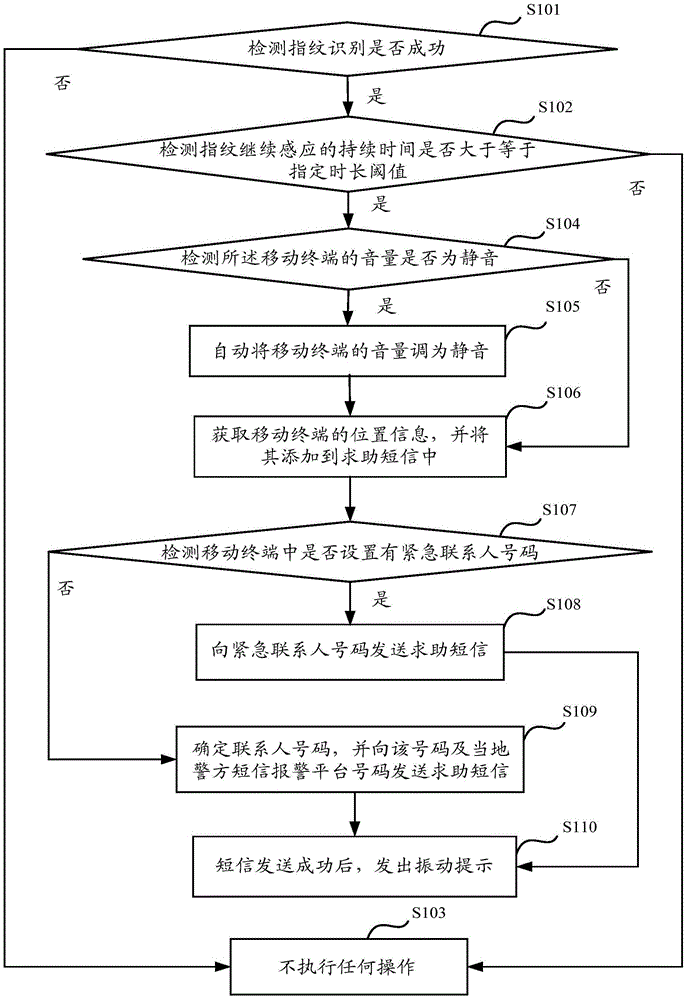
[0037] like figure 1 As shown, it is a schematic flowchart of a fingerprint identification-based help-seeking method provided in an embodiment of the present invention, which is applied to a mobile terminal, and the method includes:
[0038] S101. Detect whether the fingerprint identification is successful; if yes, execute S102; otherwise, execute S103.
[0039] In this example, the fingerprint identification sensor built in the mobile terminal is used to detect whether the fingerprint information input by the user matches the preset fingerprint information, and if they match, the identification of the user is successful.
[0040] S102. Detect whether the duration of fingerprint sensing is greater than or equal to a specified duration threshold; if yes, execute S104; otherwise, execute S103.
[0041] In this example, after the fingerprint identification is successful, the application measures the duration of the fingerprint sensing to realize the covert operation and ask for ...
Embodiment 2
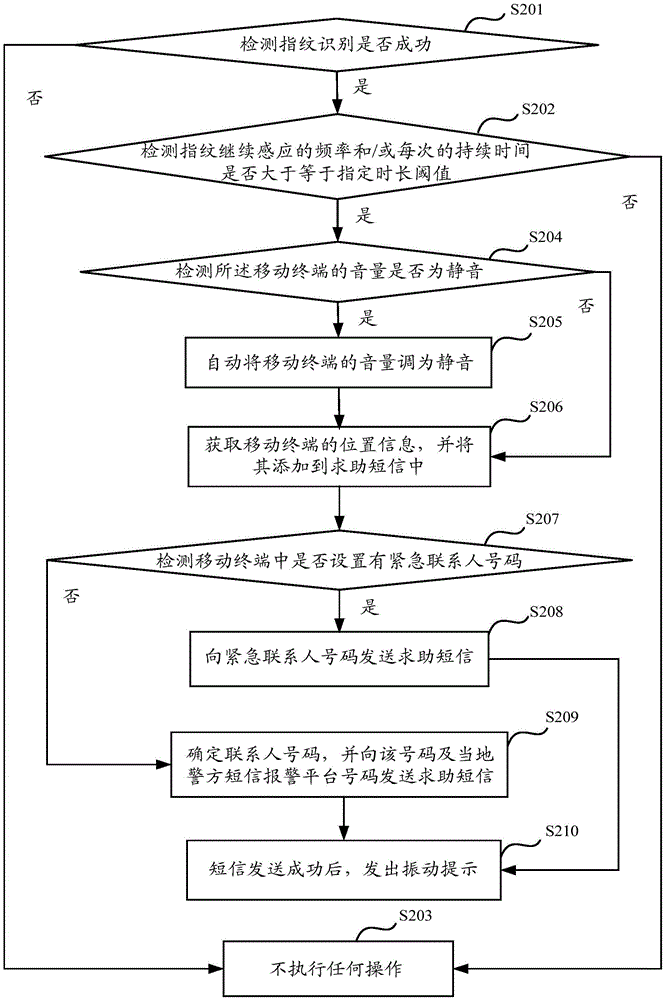
[0059] like figure 2 As shown, it is a schematic flowchart of a fingerprint identification-based help-seeking method provided in an embodiment of the present invention, which is applied to a mobile terminal, and the method includes:
[0060] S201. Detect whether the fingerprint recognition is successful; if yes, execute S202; otherwise, execute S203.
[0061] In this example, the fingerprint identification sensor built in the mobile terminal is used to detect whether the fingerprint information input by the user matches the preset fingerprint information, and if they match, the identification of the user is successful.
[0062] S202, detecting whether the frequency of continuous fingerprint sensing and / or the duration of each continuous sensing is greater than or equal to a specified duration threshold; if yes, execute S204, otherwise, execute S203.
[0063] In this example, after the fingerprint identification is successful, continue to detect the frequency of the continuou...
Embodiment 3
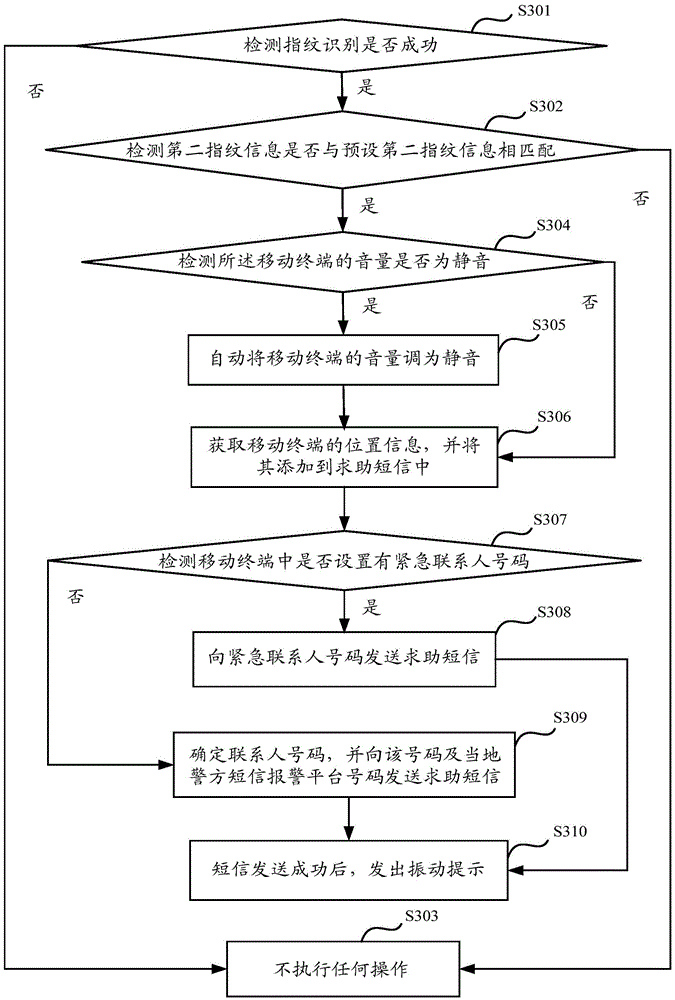
[0066] like image 3 As shown, it is a schematic flowchart of a fingerprint identification-based help-seeking method provided in an embodiment of the present invention, which is applied to a mobile terminal, and the method includes:
[0067] S301. Detect whether the fingerprint identification is successful; if yes, execute S302; otherwise, execute S303.
[0068] In this example, the fingerprint identification sensor built in the mobile terminal detects whether the first fingerprint information input by the user matches the preset first fingerprint information, and if they match, the identification of the user is successful. At the same time, the mobile terminal sends out a vibration prompt to prompt the user to input the second fingerprint information.
[0069] S302. Detect whether the second fingerprint information matches the preset second fingerprint information; if yes, execute S304; otherwise, execute S303.
[0070] In this example, after the fingerprint identification ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com