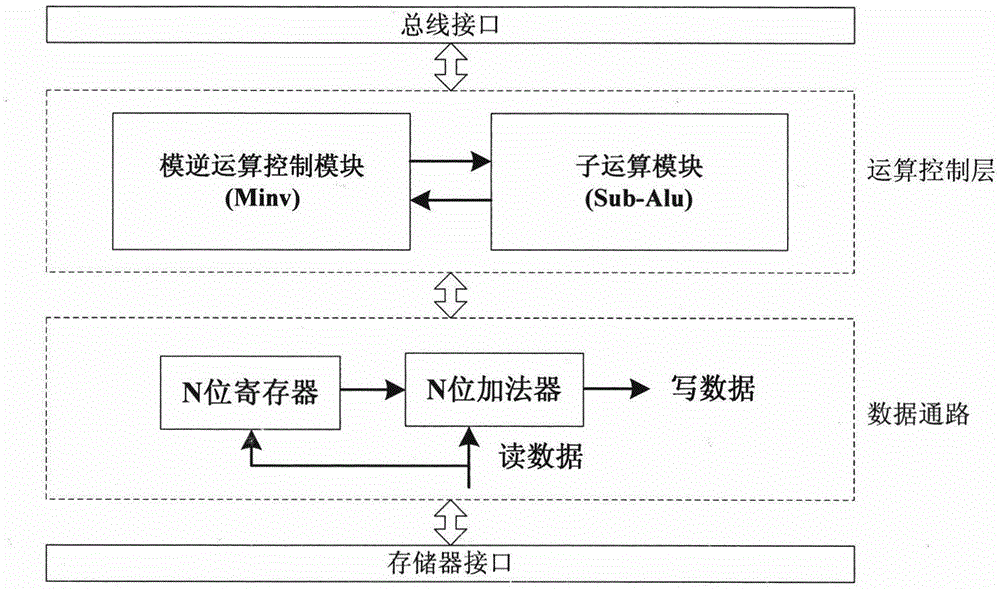
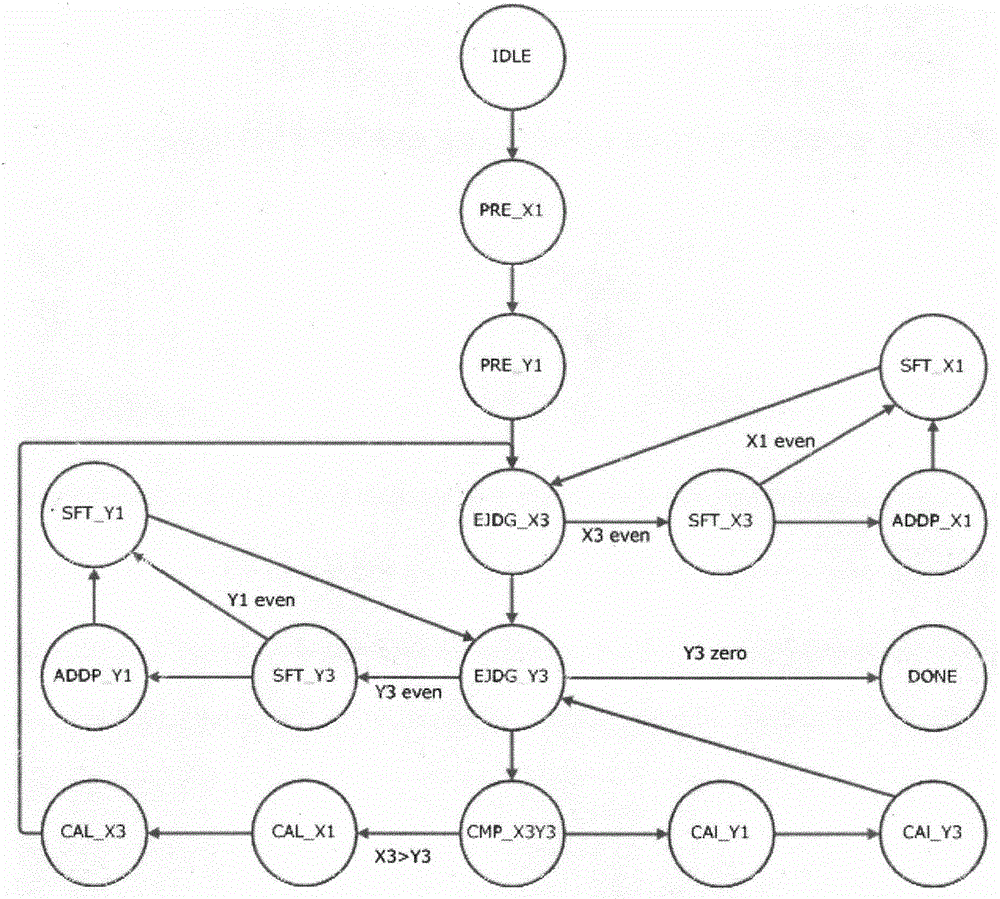
Unsigned processing method of modular inversion algorithm and modular inversion accelerator
A processing method, unsigned technology, applied in the field of public key cryptography, can solve problems such as widening, cumbersome integrated circuits, resource consumption, etc., and achieve the effect of reducing occupation, improving operation speed, and exempting the processing of symbols and carry
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
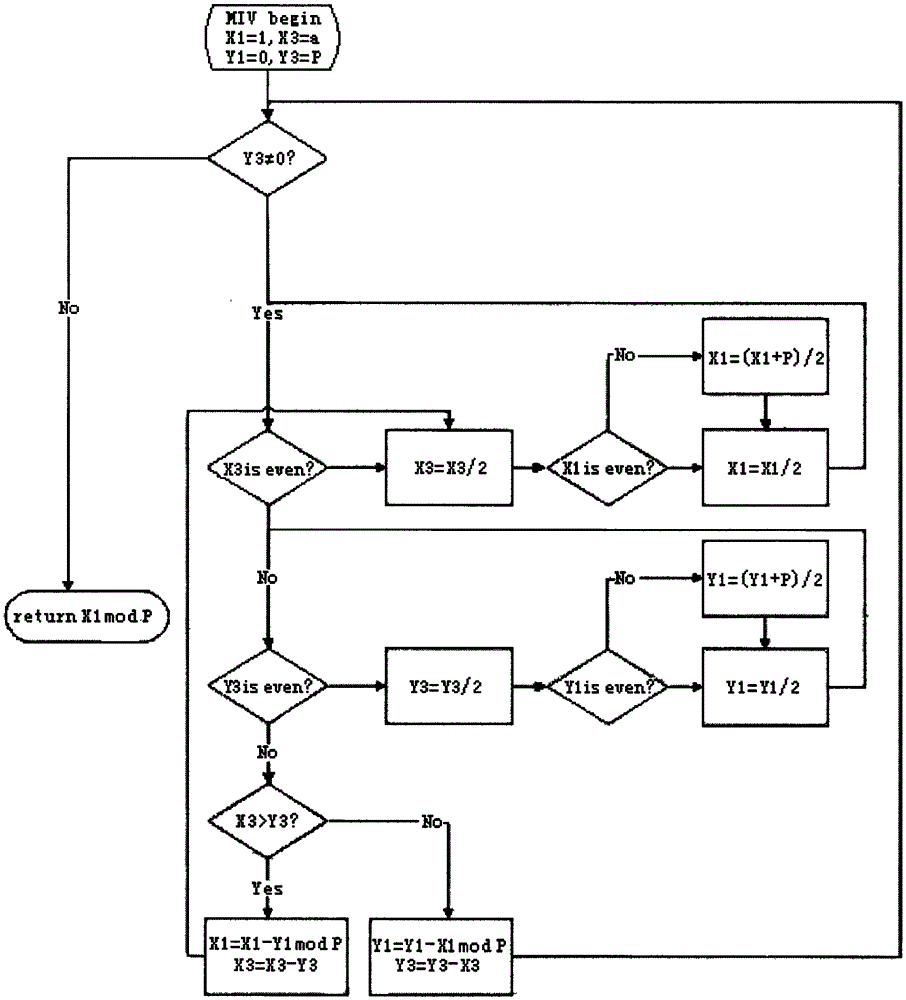
[0041] Such as figure 1 As shown, the unsigned processing method of the modular inverse algorithm is based on the extended Euclidean algorithm in the public key cryptography algorithm, and the modular subtraction operation is used to replace the subtraction operation in step 3 and condition 3 of the extended Euclidean algorithm, eliminating Step 3 of the extended Euclidean algorithm, the relevant operations on the temporary variables X2 and Y2 in condition 1 and condition 2, the modified algorithm is as follows:
[0042] Input: prime number p, a ∈ [1, p-1];
[0043] output: a -1 modp;
[0044] Step 1, initializing intermediate variables X1, X3, Y1, Y3, making it respectively: X1=1; X3=a; Y1=0; Y3=p;
[0045] Step 2. Determine the value of Y3: if Y3 is not 0, go to step 3; otherwise, go to step 4;
[0046] Step 3: Determine the following conditions in turn and perform related operations:
[0047] Condition 1: If X3 is an even number, complete the following operations: 1. C...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com