Mobile communication inter-network honeypot system and method
A mobile communication network and honeypot technology, applied in transmission systems, electrical components, etc., can solve the problems that the signaling originator cannot receive the signaling response, the user's security is immediately damaged, and the trace protection method is implemented. Convenience, satisfying high reliability, and maintaining integrity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
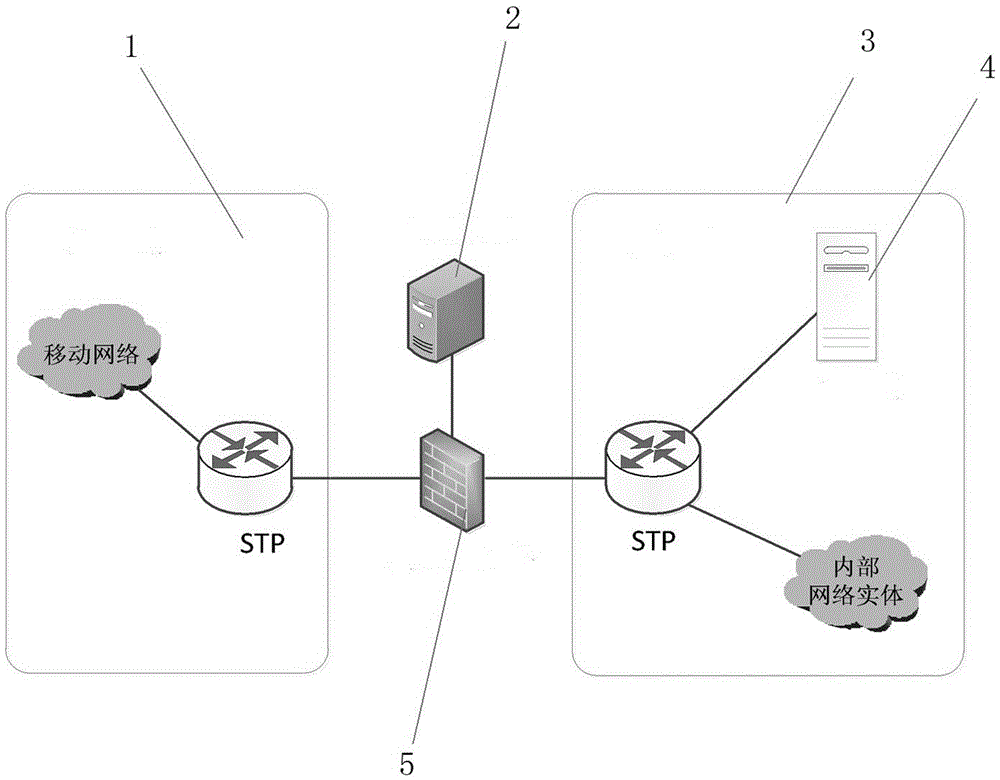
[0026] Example 1: Combining figure 1 , a kind of mobile communication network honeypot method, this method comprises the following steps:
[0027] Step 1: The underlying access device receives the signaling message and forwards it to the monitoring server; Step 2: The monitoring server detects the abnormality of the signaling; Step 3: The honeypot device processes the abnormal information.
[0028] The underlying access device receives the signaling message and forwards it to the monitoring server. The underlying device forwards the signaling that needs to be protected to the monitoring server according to the configuration; the signaling that does not need protection is directly forwarded to the STP of the internal network. The message is forwarded according to the destination address.
[0029] The monitoring server performs anomaly detection on the signaling, mainly for the received signaling message, the monitoring server selects an anomaly detection algorithm by looking ...
Embodiment 2
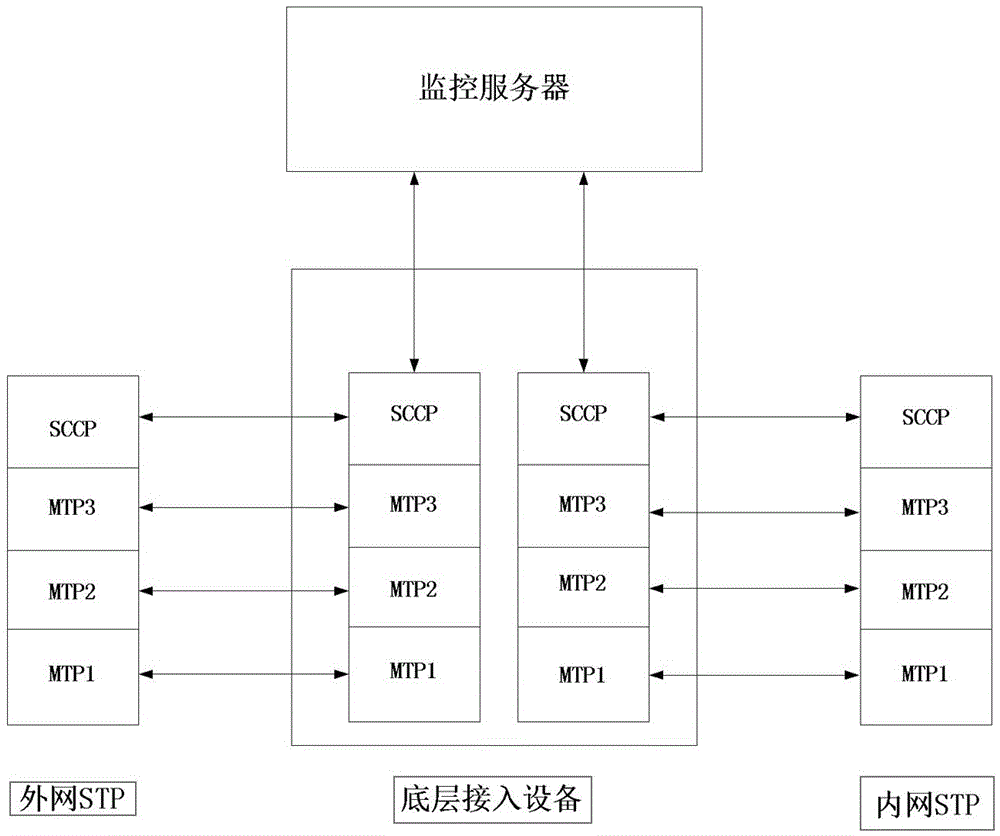
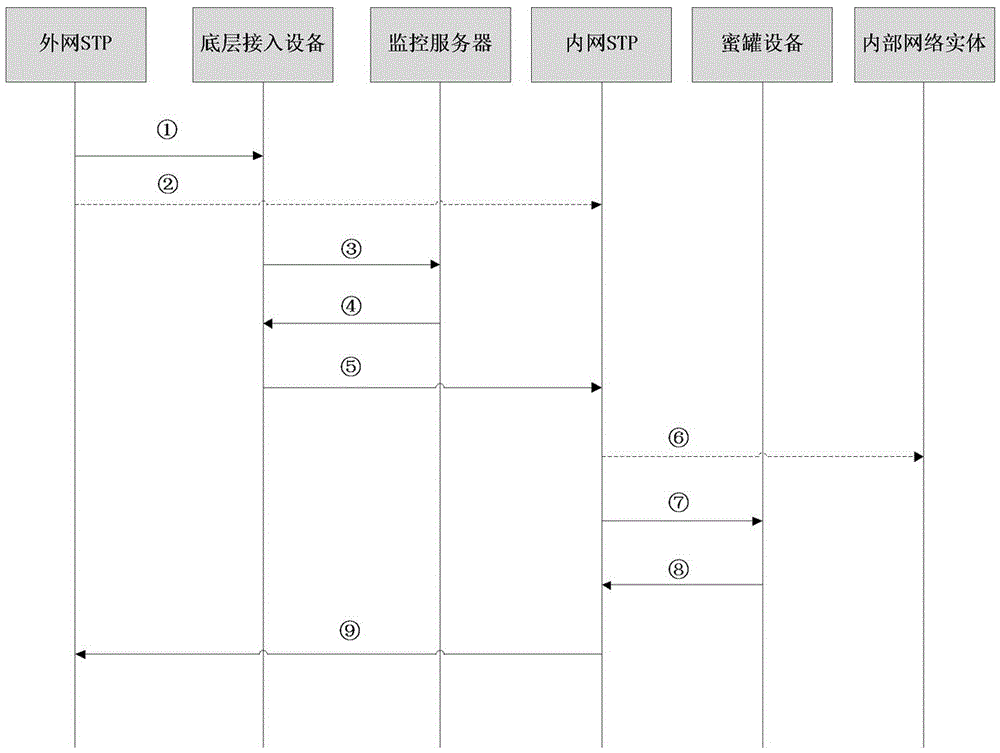
[0035] Example 2: Combining figure 1 , image 3 , a honeypot method between mobile communication networks, specifically comprising the following steps:
[0036] Step 1. The underlying access device receives the signaling message and forwards it to the monitoring server; the underlying access device forwards the signaling message to be detected to the server according to the configuration policy, and forwards other signaling messages directly to the destination device; the monitoring server returns The message is forwarded directly to the destination device.
[0037] Step 2: The monitoring server detects the abnormality of the signaling; in order to ensure the safety of the protected equipment, the monitoring server has the planning information of the protective network, and can adopt different detection methods according to the destination device type and message type of the signaling. The legal and normal signaling is not processed, and is directly forwarded through the un...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com