Big file uploading and continuous uploading method and device for browser or server
A browser and server technology, applied to electrical components, transmission systems, etc., can solve problems such as high repetition rate, inability to verify the correctness of file data, and inability to guarantee data integrity, so as to ensure integrity, reduce operating procedures, and reduce The effect of development costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
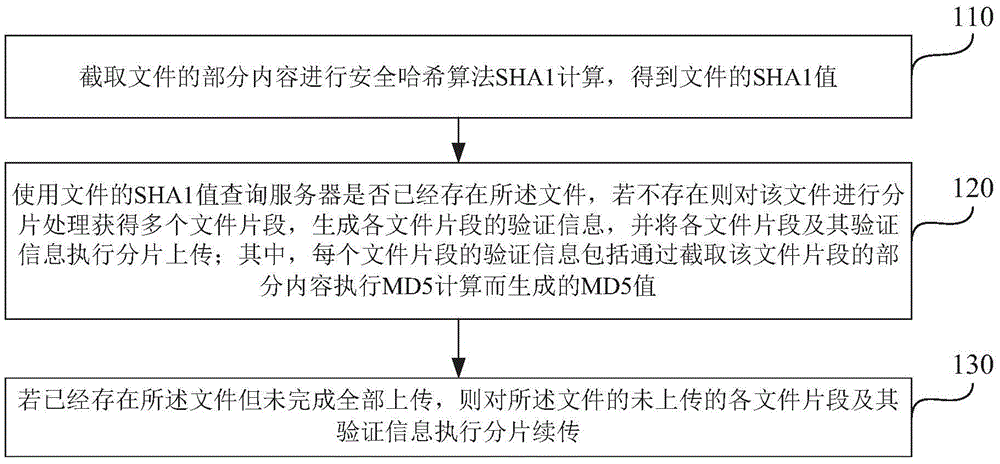
[0048] figure 1 It is a flow chart of a method for uploading and resuming a large file for a browser according to Embodiment 1 of the present invention. The browser can be a browser based on HTML5FileAPI, see figure 1 , which includes the following steps:
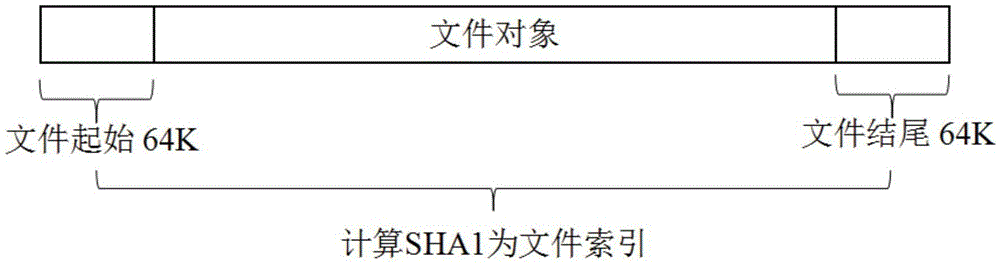
[0049] Step 110: Intercepting part of the content of the file to calculate the secure hash algorithm SHA1 to obtain the SHA1 value of the file.
[0050] The reason for using the SHA1 algorithm in this step is that SHA1 is currently a relatively widely used algorithm, and its performance is relatively low for browsers. If other algorithms are used, the overall performance may be reduced due to computational complexity. Intercepting part of the content of the file for calculation instead of intercepting the entire file will help reduce the resource consumption of the server and client, and reduce the load on the server.
[0051] Step 120: Use the SHA1 value of the file to inquire whether the file already exists in the serv...
Embodiment 2
[0059] image 3 It is a flow chart of the method for uploading and resuming a large file to a server according to Embodiment 2 of the present invention. refer to image 3 , which includes the following steps:
[0060] Step 210: Receive the file query request sent by the browser, the file query request includes the secure hash algorithm SHA1 value of the file to be queried; wherein, the SHA1 value is generated by the browser by intercepting part of the content of the file to be queried and performing SHA1 calculation of.
[0061] Step 220: Return the query result of whether the file exists to the browser.
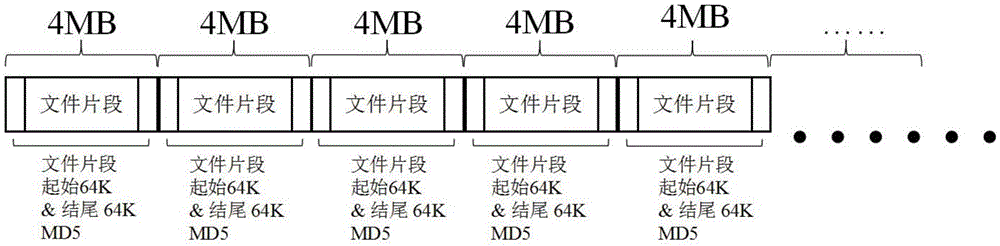
[0062] Step 230: Receive a plurality of fragmented data uploaded by the browser when the query result is non-existent. The fragmented data includes file fragments and their information digest algorithm MD5 values. Preferably, the segment data may include the serial number of the file segment, the content of the file segment and the MD5 value of the information digest alg...
Embodiment 3
[0070] Figure 4 It is a functional block diagram of a browser in Embodiment 3 of the present invention. The browser correspondingly executes the method in Embodiment 1, such as Figure 4 As shown, the browser includes: a SHA1 calculation module 310, which is used to intercept part of the content of the file and perform a secure hash algorithm SHA1 calculation to obtain the SHA1 value of the file; a file query module 320, which is used to use the SHA1 value of the file to query whether the server has There is a file; upload and resume module 330, which includes file segmentation submodule 331, MD5 calculation submodule 332, fragmentation upload submodule 333 and fragmentation resume submodule 334; file division submodule 331 is used for if not If there is a file, the file is fragmented to obtain a plurality of file fragments, and the MD5 calculation sub-module 332 is used to generate verification information of each file fragment, wherein the verification information of each ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com