Identity authentication method for low-rate wireless network
A wireless network and identity authentication technology, applied in the field of wireless network data processing, can solve problems such as ineffective identity authentication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
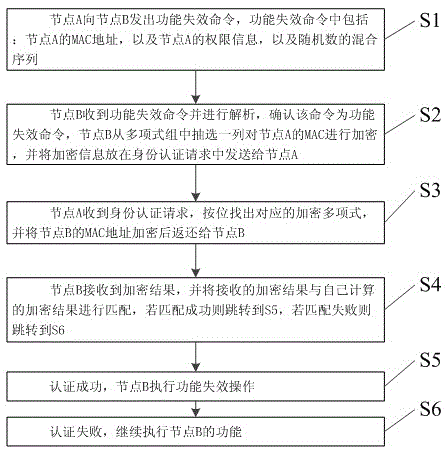
[0038] In Example 1, please refer to figure 1 , provide a kind of identity authentication method for low rate wireless network, described method is applied in ZigBee wireless network, described method comprises:
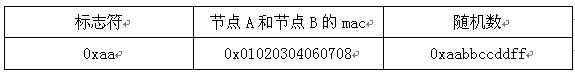
[0039] S1: Node A sends a function failure command to node B. The function failure command includes: node A's MAC address, node A's permission information, and a mixed sequence of random numbers;
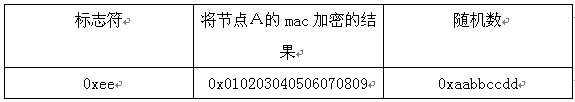
[0040] S2: Node B receives the function failure command and analyzes it, and confirms that the command is a function failure command. Node B selects a column from the polynomial group to encrypt the MAC of node A, and sends the encrypted information in the identity authentication request to Node A;
[0041] S3: Node A receives the identity authentication request, finds out the corresponding encryption polynomial bit by bit, and returns the MAC address of node B to node B after encrypting;
[0042] S4: Node B receives the encrypted result and matches the received encrypte...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com