Alarm association rule mining method and device
A rule and weighted correlation technology, applied in the field of communication, can solve the problems of low efficiency, complex network structure, high cost of obtaining effective alarm correlation rules, and achieve the effect of improving accurate determination and avoiding I/O overhead.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
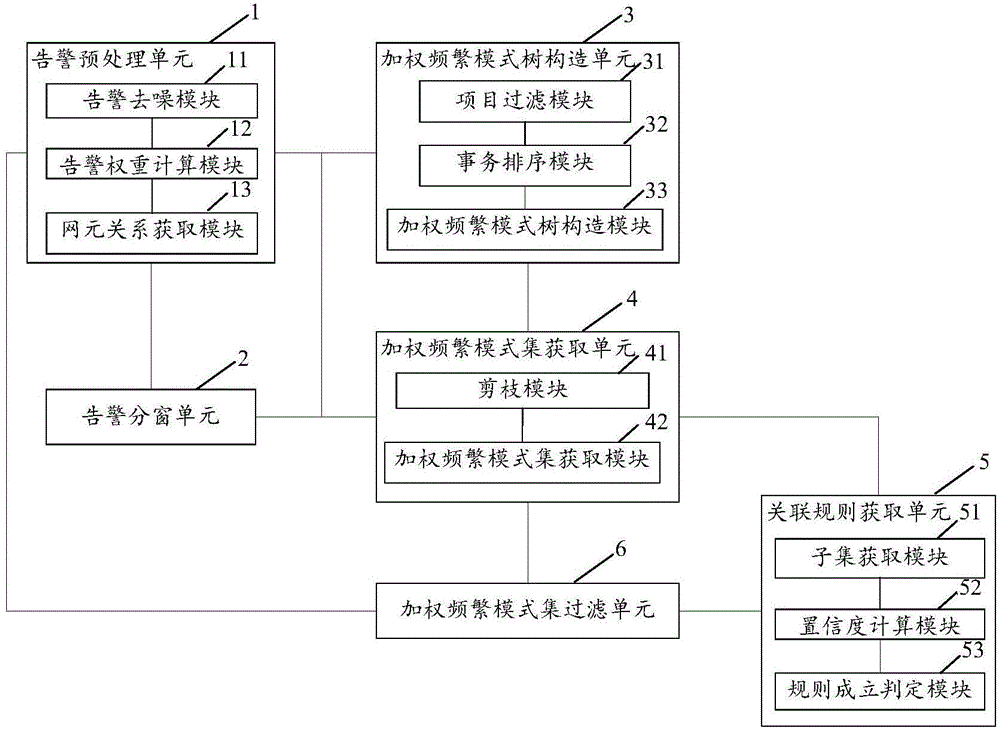
Image
Examples
Embodiment 2
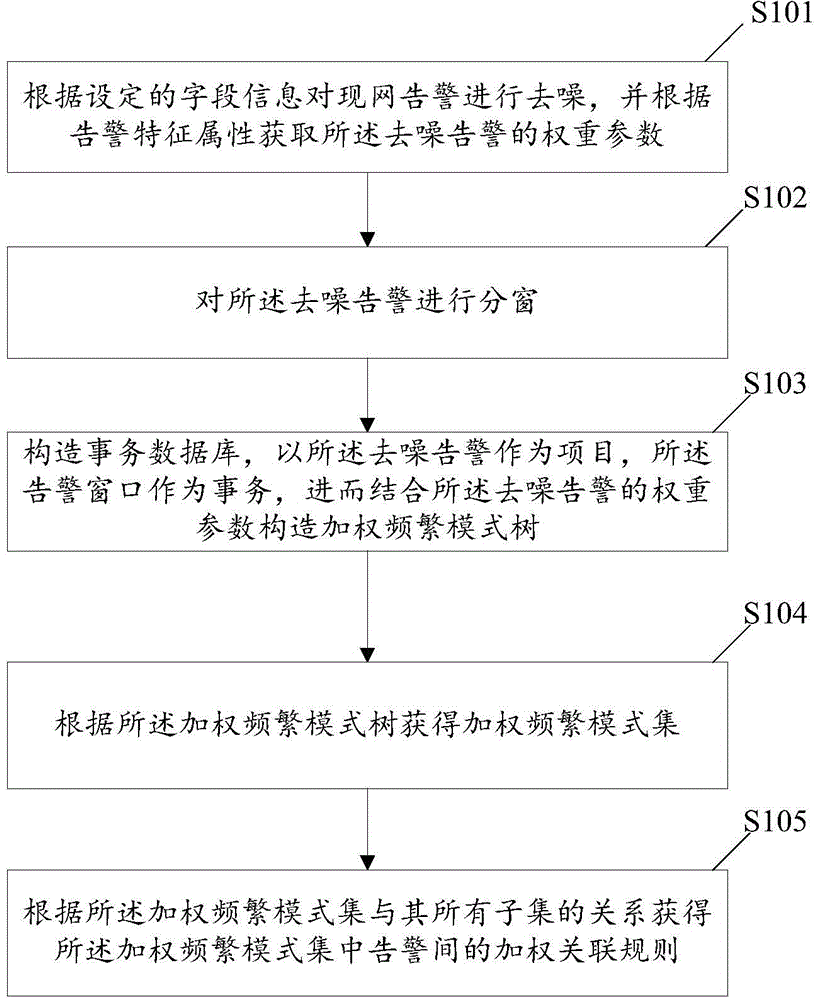
[0084] In order to set forth the present invention better, provide embodiment two of the present invention below, as figure 2 Shown:
[0085] Step S201: Denoise the alarm on the live network according to the set field information, and obtain the weight parameter of the denoised alarm according to the characteristic attribute of the alarm.
[0086] Alarm denoising refers to the cleaning and filtering of alarm data. Some alarms in the original alarm data are noise data or unnecessary for alarm mining and analysis, and these data need to be eliminated.
[0087] According to the set field information, delete alarms with incomplete field data, remove engineering alarms, remove non-communication equipment alarms, remove associated alarms, remove minor alarms, and remove duplicate alarms. The specific processing content is as follows:
[0088] a) For the full amount of alarm data, filter out the necessary field content according to the needs of mining. As shown in Table 1:
[00...
Embodiment 3
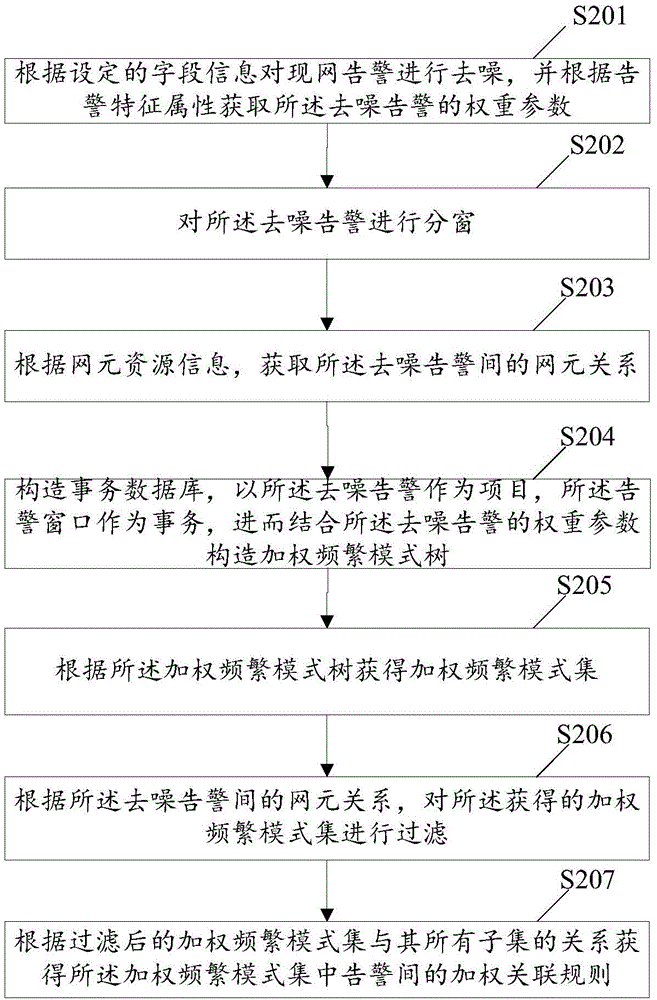
[0153] In order to better illustrate the steps of the present invention to construct a weighted frequent pattern tree, the third embodiment of the present invention is given below, as image 3 Shown:
[0154] In order to better explain the construction method of the weighted frequent pattern tree, some terms need to be explained:
[0155] Support: Assuming that X is an item set and D is a transactional database, the ratio of the number of transactions containing X in D to the total number of transactions in D is the support of X in D. The support of X is recorded as sup(X), and the association rules The support degree of is recorded as sup(X∪Y).
[0156] sup ( X ) = | { t ∈ D | X ⊆ t } | | ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com