Database encryption method and encryption database query method
An encryption method and database technology, applied in the field of data privacy protection, can solve problems such as low execution efficiency, inability to execute on ciphertext, loss, etc., to achieve the effect of protecting privacy, reducing communication and computing overhead, and improving execution efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0064] The specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings.
[0065] A kind of database encryption method designed by the present invention comprises the following steps in the actual application process:
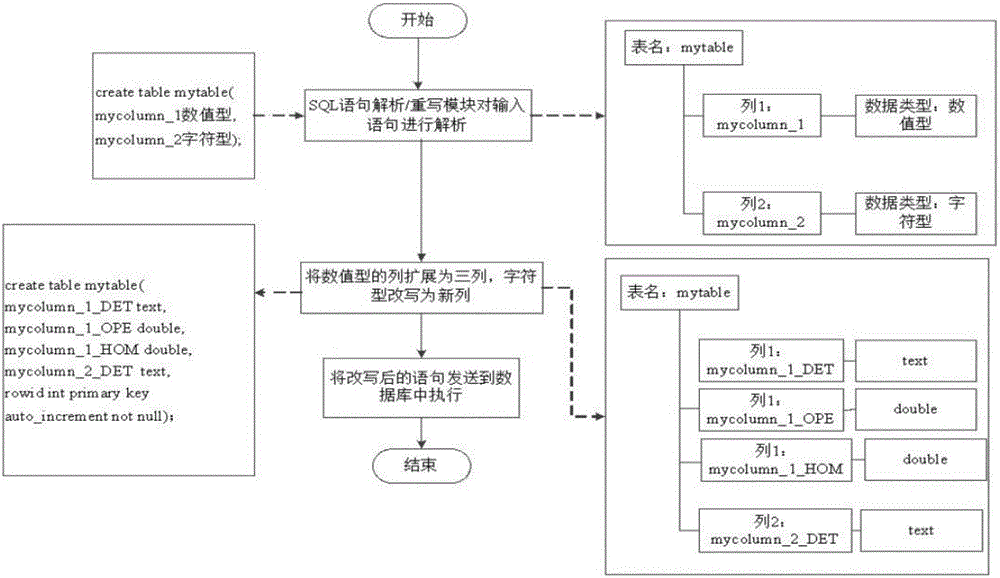
[0066] Step 001. Determine the data type of each data column in each table in the database. If the data type of the data column is numeric (int, float, double), then enter step 002; if the data type of the data column is character ( char, varchar, text), go to step 003.
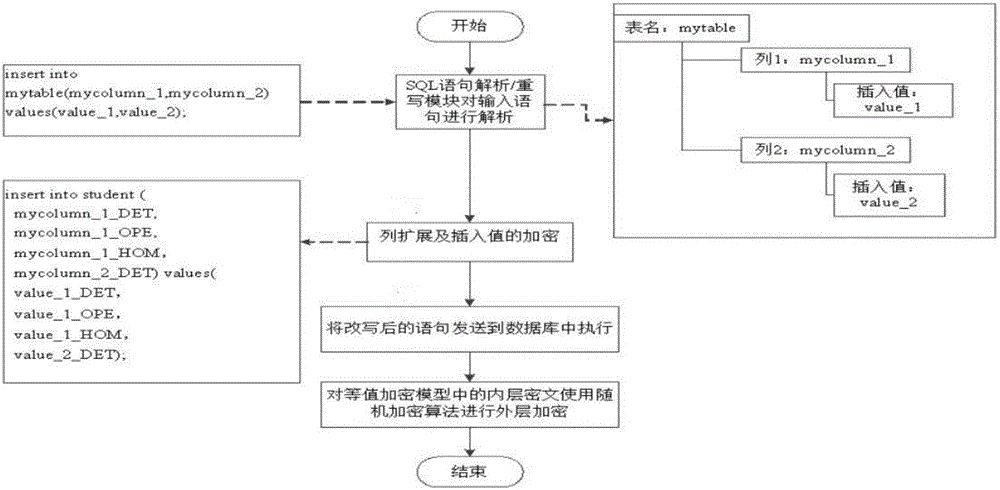
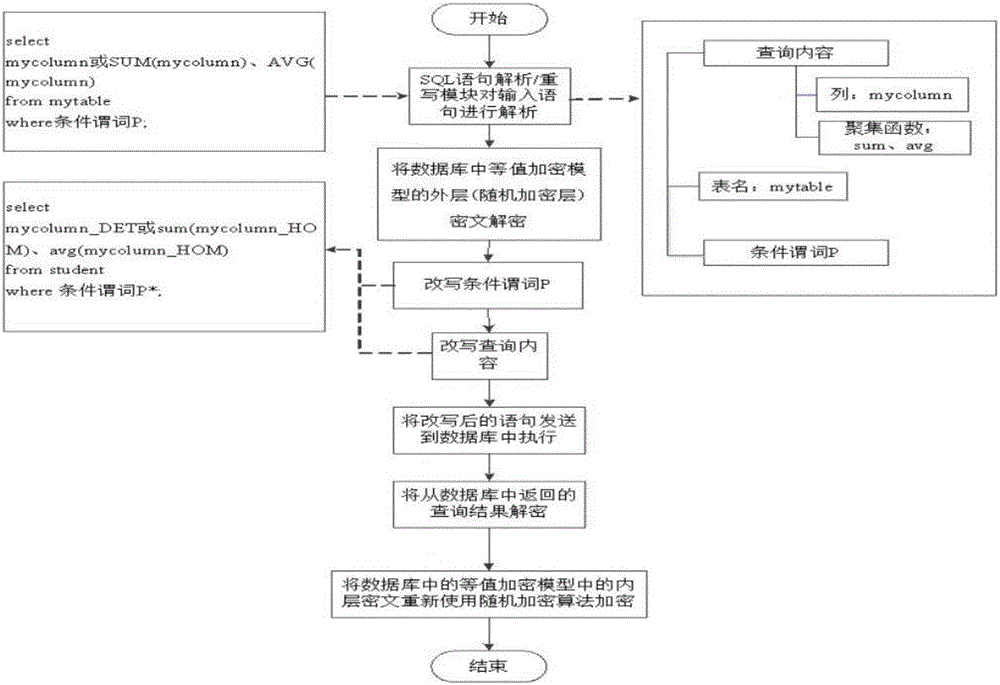
[0067] Step 002. For each data in the numerical data column, use the equivalent encryption algorithm, the storage encryption algorithm and the homomorphic encryption algorithm to encrypt respectively, and expand the numerical data column into three columns, and then press the three There is a one-to-one correspondence between columns and equivalent encryption algorithms, storage encryption algorithms, and homo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com