LBS-based anti-attack location privacy protection method for IoV
A privacy protection and vehicle networking technology, applied in the field of location privacy protection based on anti-attack, can solve the problems of finding the real identity, Zhang solution is vulnerable to counterfeiting attacks and anti-tracking attacks, and it is difficult for authoritative organizations to achieve the effect of ensuring security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
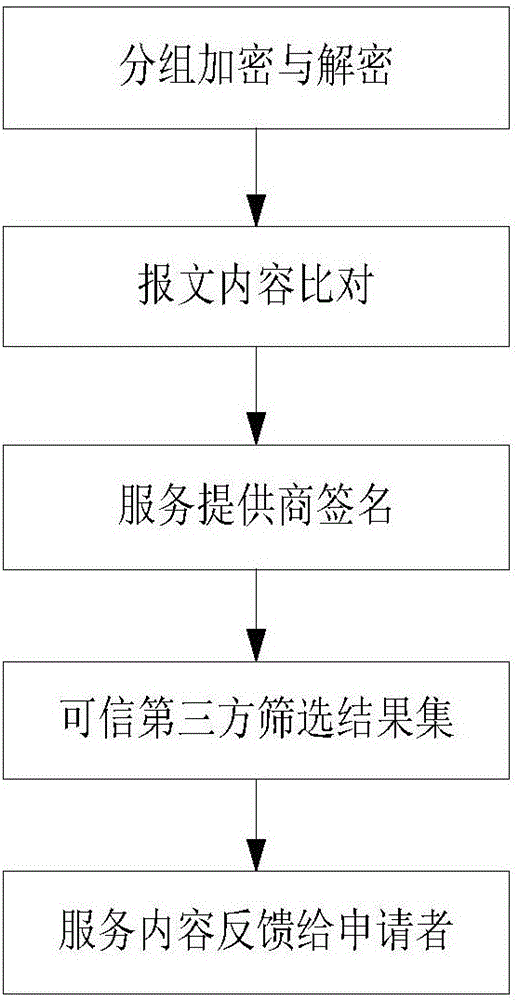
[0068] Such as figure 1 As shown, the detection method of the present embodiment has 5 steps, which are respectively:
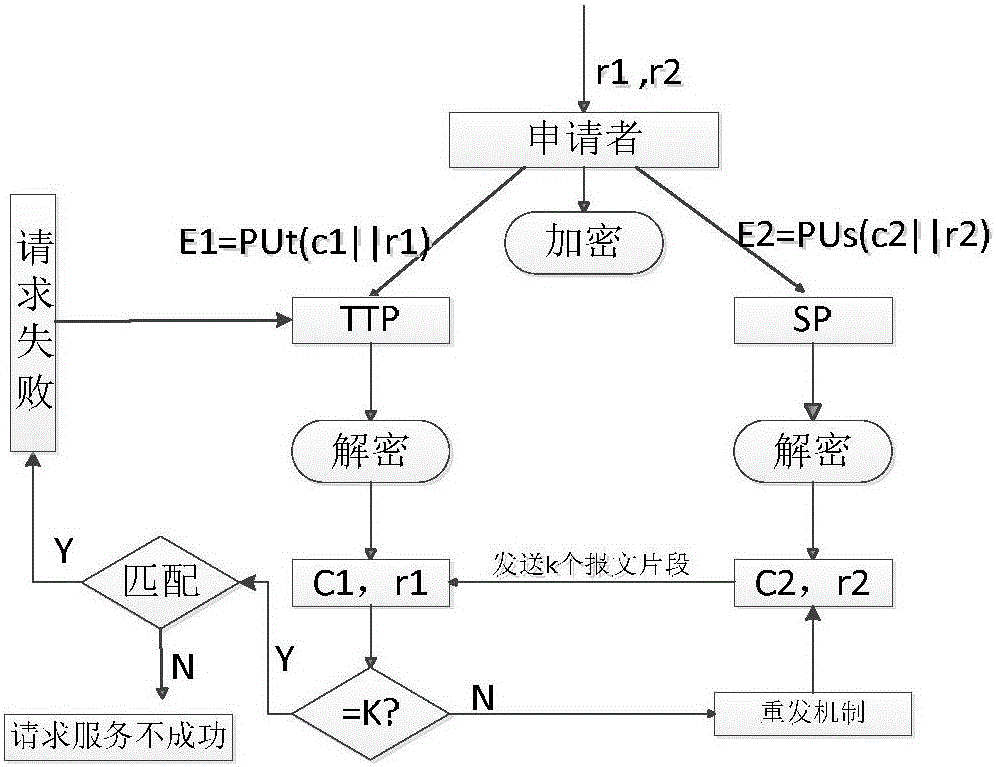
[0069] (1) Packet encryption and decryption: split the trajectory into two arrays, encrypt them with the public key and send them out, and the receiver uses the private key to decrypt and get the content of the message;
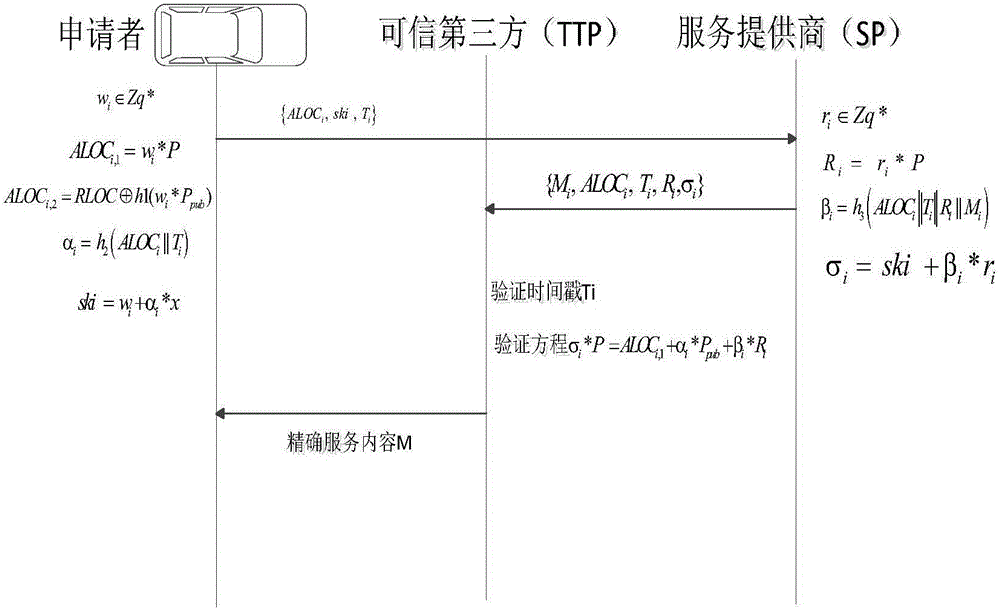
[0070] (2) Message content comparison: to prevent other parties from attacking the server or the service provider from tampering with the request message for profit, so the message must be transferred by a trusted third party during the transmission process, and the service provider and the trusted third party will respectively The service request information in the received message content is extracted, and then sent to the trusted third party by the service provider, and the result matching is performed on the trusted third party. Before matching, check whether the packet is lost. If the packet is lost, then Request resend; if there is no...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com