Cloud computing ccs fine-grained data control method
A data control and cloud computing technology, applied in transmission systems, electrical components, etc., can solve the problems of not being able to fully understand all the information, not suitable for cloud computing environments, and complex access control of fine-grained encrypted data, so as to improve security and effect. Good results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] Below, in conjunction with accompanying drawing and specific embodiment, the present invention is described further:
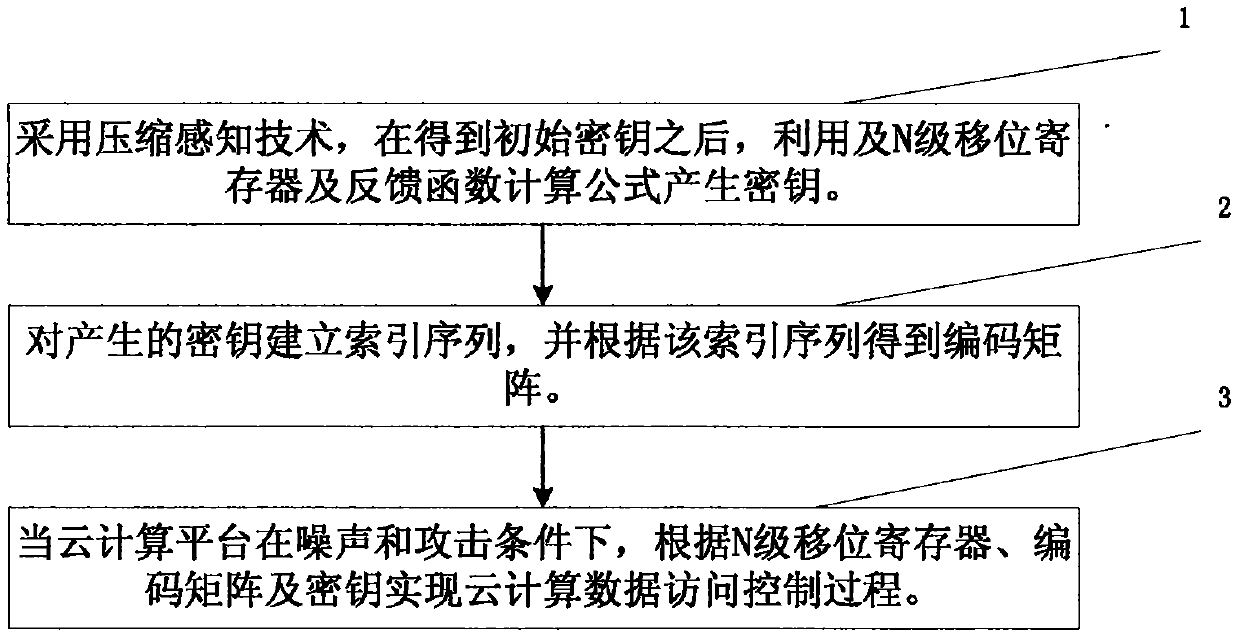
[0039] refer to figure 1 , a cloud computing CCS fine-grained data control method described in this embodiment, comprising the following steps:
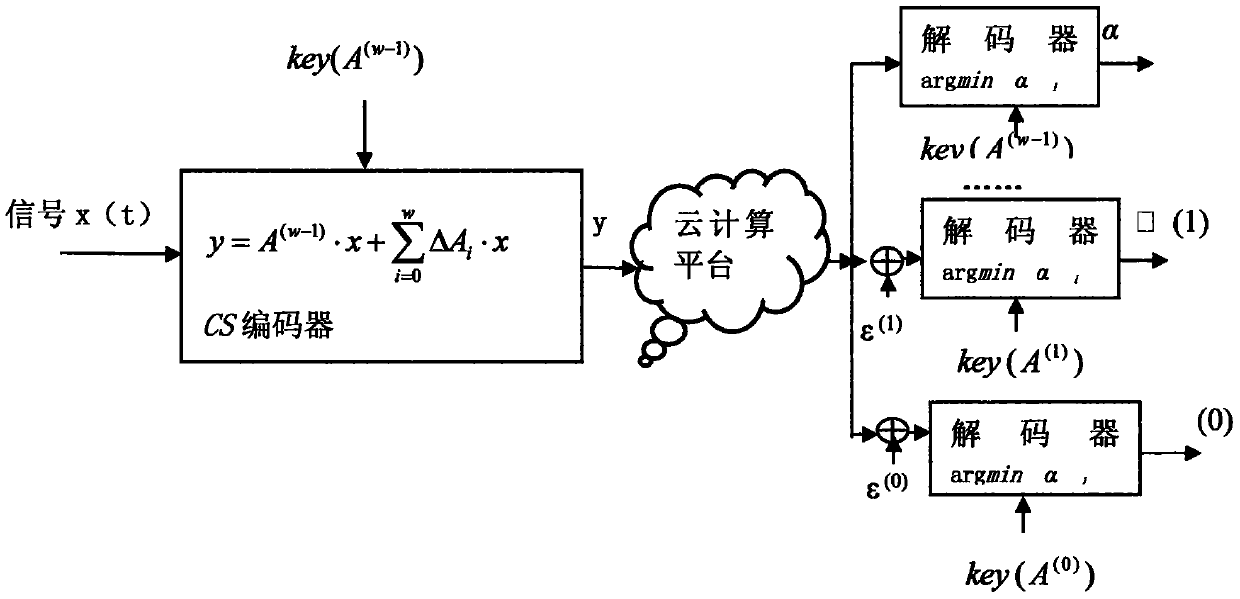
[0040] Step 1: Use compressed sensing technology (or CS technology, the English full name is Compressed Sensing), after obtaining the initial key, use the N-level shift register and the feedback function calculation formula to generate the key. The N is greater than or equal to 1. The shift register stores data in a manner of storing double-precision decimal numbers.
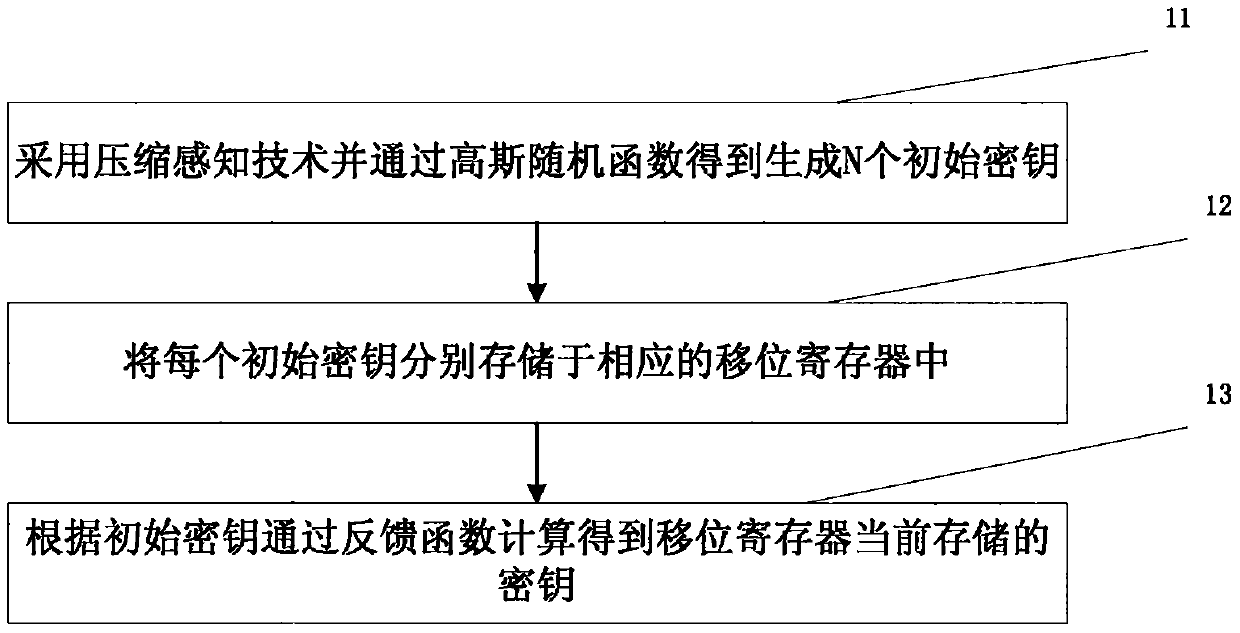
[0041] combined reference figure 2 , step 1 may also include the following steps:
[0042] Step 11, use compressed sensing technology and generate N initial keys through Gaussian random function; in this step 11, the initial state value c of the Gaussian function can be used (0) ~N(0,1) generates the initial key.
[0043] Step 12, storing...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com