Safety management method and device based on NFV (Network Function Virtualization)
A security management and security technology, applied in the field of communication network, can solve problems such as complex network architecture
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0035] The NFV-based security management method provided by the embodiment of the present invention may be executed by an NFV-based security management device.
[0036] like Figure 5 As shown, the NFV-based security management method provided by the embodiment of the present invention includes the following steps:
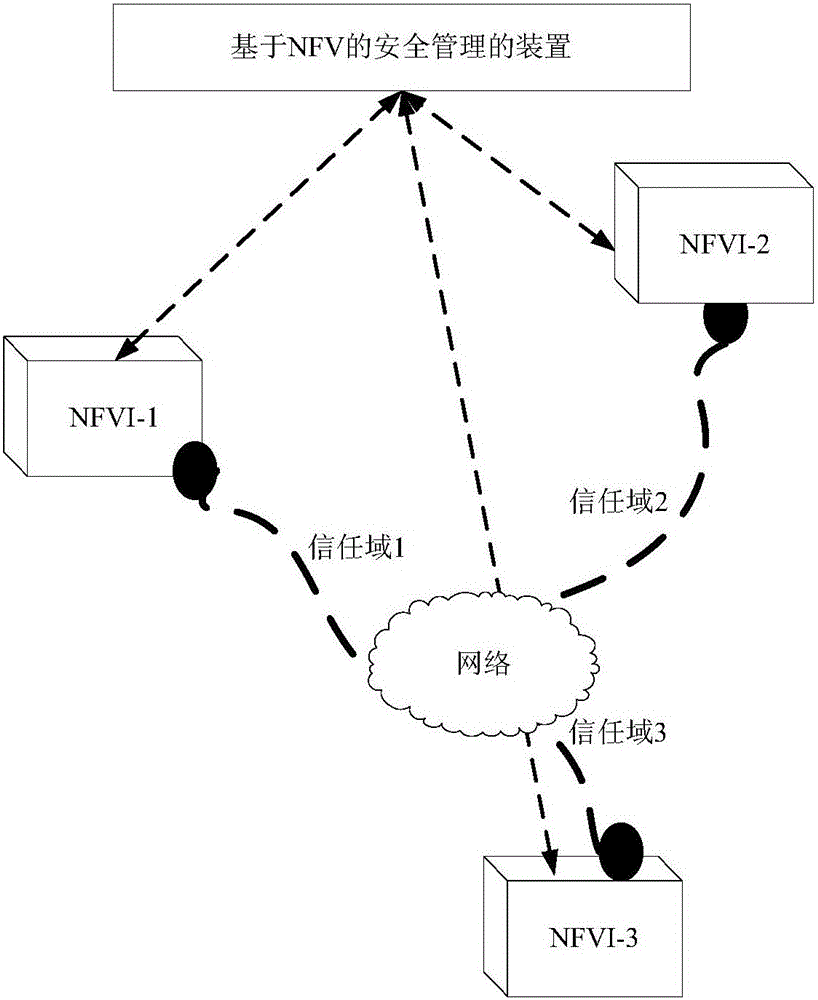
[0037] Step S101: Determine the changed target node in the NFV service network domain.
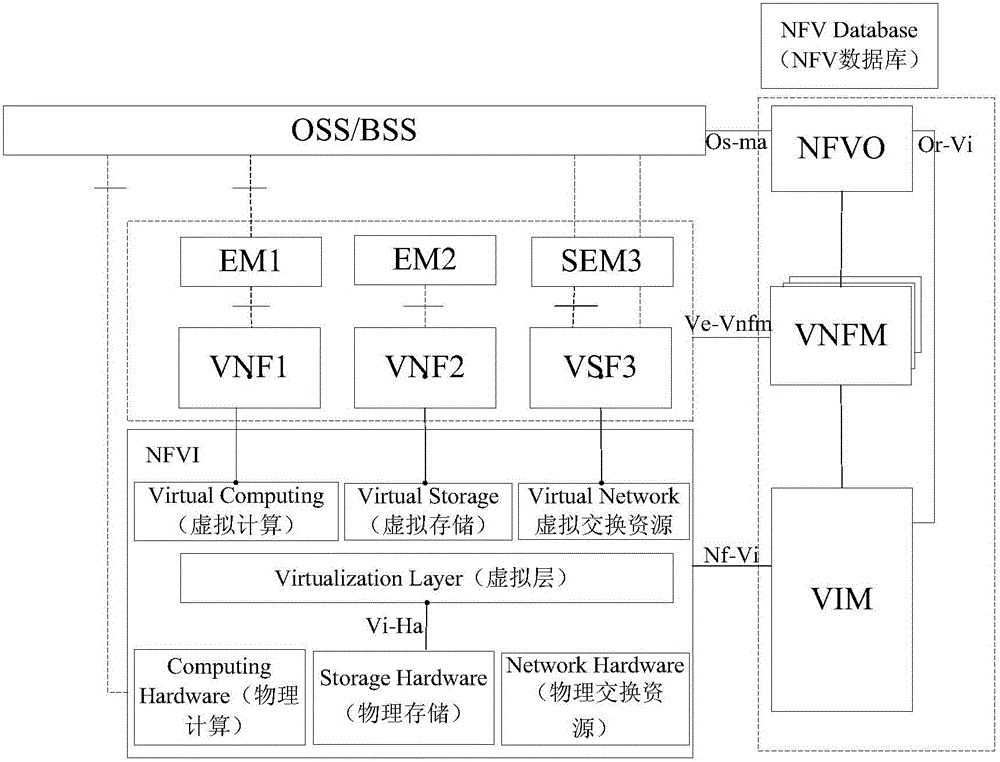
[0038] During the operation of the NFV network, the network will be changed according to certain requirements. For example, the network operator may add new nodes in the business network domain according to the requirements, or the network operation may change due to failures and other reasons. node. The so-called node can be a certain network element in the service network domain, for example, it can be a VNF, a virtual computing network element in NFVI, a physical computing network element, etc., or a virtual machine in the service network domain (that is, a virtual machine ...
Embodiment 2
[0070] In order to let network managers know the current status of the network, the embodiment of the present invention sends a security alarm prompt to the NFV operation support entity after generating a corresponding security policy. Such as Figure 6 As shown, on the basis of Embodiment 1, after step S104 and before step S105, the method for security management based on network function virtualization NFV provided by the embodiment of the present invention further includes the following steps:
[0071] Step S106: Sending a security warning prompt to the NFV operation support entity (including OSS and BSS).
[0072] Specifically, it sends a security alarm prompt to the OSS in the NFV operation support entity.
[0073] In the method for security management based on network function virtualization NFV provided by the embodiment of the present invention, after the security management device generates a corresponding security policy, it sends a security alarm prompt to the NFV ...
Embodiment 3
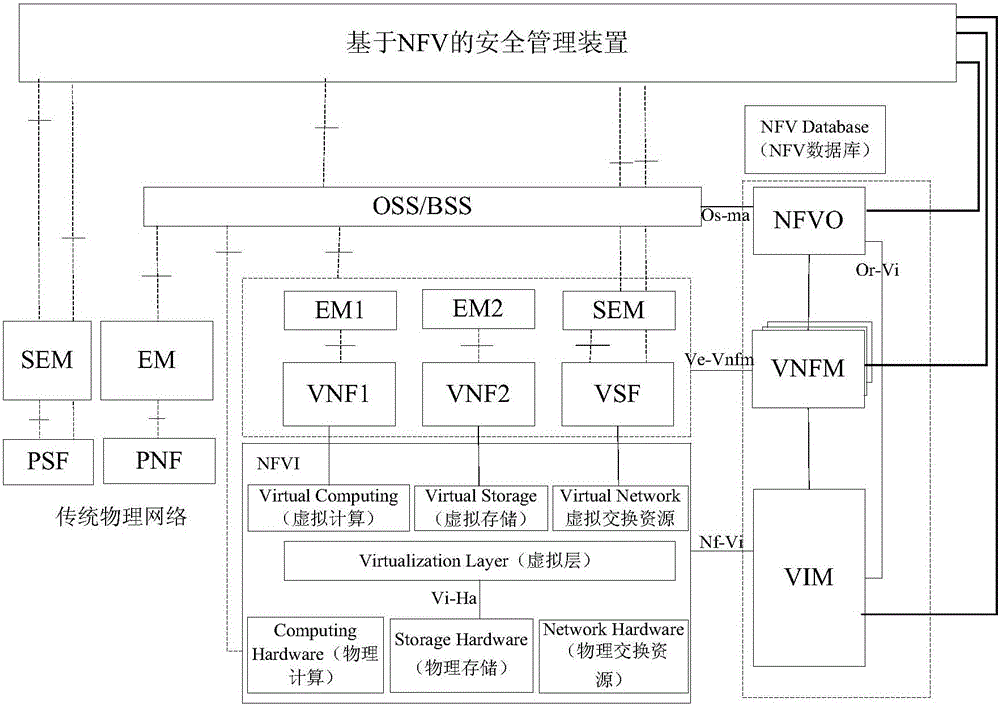
[0075] An embodiment of the present invention provides an apparatus for NFV-based security management, which is used to execute the method for NFV-based security management shown in any one of the foregoing embodiments (embodiment 1 or embodiment 2).
[0076] Such as Figure 7 As shown, the NFV-based security management device includes: a data acquisition module, a security monitoring module, and a security orchestration module;
[0077] The data acquisition module 71 is configured to determine the changed target node in the NFV service network domain, and acquire the network data transmitted by the target node, and send the acquired network data to the security monitoring module;
[0078] The security monitoring module 72 is configured to analyze whether there is an unsafe event in the network data acquired by the data acquisition module 71, and if there is an unsafe event, generate a corresponding security policy and send the security policy to the Security orchestration mo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com